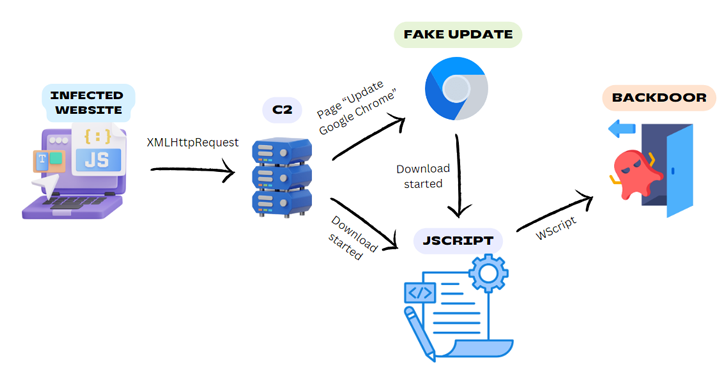
Reputable-but-compromised websites are staying utilized as a conduit to provide a Windows backdoor dubbed BadSpace below the guise of fake browser updates.
“The risk actor employs a multi-phase attack chain involving an contaminated internet site, a command-and-command (C2) server, in some cases a faux browser update, and a JScript downloader to deploy a backdoor into the victim’s program,” German cybersecurity business G Details explained in a report.
Specifics of the malware have been initially shared by researchers kevross33 and Gi7w0rm final thirty day period.
It all commences with a compromised web-site, such as those designed on WordPress, to inject code that incorporates logic to establish if a user has visited the web site just before.
Ought to it be the user’s 1st stop by, the code collects facts about the device, IP handle, user-agent, and locale, and transmits it to a tough-coded domain via an HTTP GET ask for.

The response from the server subsequently overlays the contents of the web site with a phony Google Chrome update pop-up window to both immediately drop the malware or a JavaScript downloader that, in turn, downloads and executes BadSpace.
An examination of the C2 servers applied in the campaign has uncovered connections to a acknowledged malware known as SocGholish (aka FakeUpdates), a JavaScript-dependent downloader malware which is propagated via the exact mechanism.
BadSpace, in addition to employing anti-sandbox checks and placing up persistence applying scheduled responsibilities, is capable of harvesting process data and processing commands that make it possible for it to consider screenshots, execute recommendations applying cmd.exe, browse and write files, and delete the scheduled activity.
The disclosure arrives as the two eSentire and Sucuri have warned different strategies leveraging bogus browser update lures in compromised web pages to distribute details stealers and remote entry trojans.
Located this short article fascinating? Observe us on Twitter and LinkedIn to browse extra special content we submit.
Some parts of this article are sourced from:
thehackernews.com

 NiceRAT Malware Targets South Korean Users via Cracked Software
NiceRAT Malware Targets South Korean Users via Cracked Software