Employment companies and retail corporations mainly located in the Asia-Pacific (APAC) region have been specific by a previously undocumented risk actor acknowledged as ResumeLooters considering that early 2023 with the purpose of stealing delicate data.
Singapore-headquartered Group-IB claimed the hacking crew’s actions are geared in the direction of job search platforms and the theft of resumes, with as a lot of as 65 web sites compromised involving November 2023 and December 2023.
The stolen data files are approximated to comprise 2,188,444 consumer data documents, of which 510,259 have been taken from work research websites. Over two million unique email addresses are existing inside the dataset.
“By employing SQL injection assaults towards web-sites, the menace actor makes an attempt to steal user databases that may include things like names, phone quantities, emails, and DoBs, as well as facts about career seekers’ practical experience, employment record, and other delicate individual data,” security researcher Nikita Rostovcev reported in a report shared with The Hacker Information.

“The stolen information is then put up for sale by the risk actor in Telegram channels.”
Team-IB reported it also uncovered evidence of cross-web-site scripting (XSS) bacterial infections on at least four respectable work lookup internet websites that are created to load destructive scripts responsible for exhibiting phishing pages capable of harvesting administrator qualifications.
ResumeLooters is the second team just after GambleForce that has been discovered staging SQL injection attacks in the APAC area given that late December 2023.
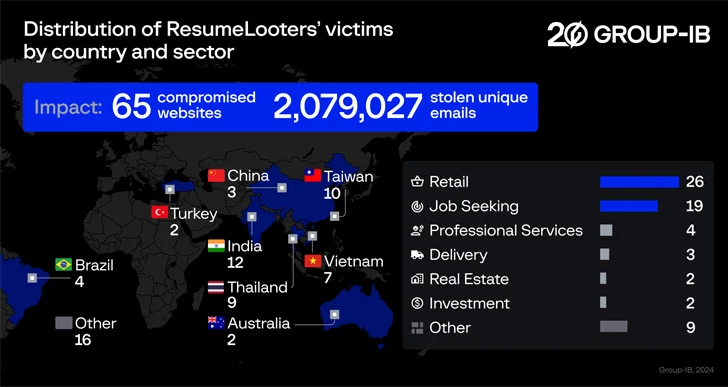
A vast majority of the compromised internet sites are centered in India, Taiwan, Thailand, Vietnam, China, Australia, and Turkey, despite the fact that compromises have also been documented from Brazil, the U.S., Turkey, Russia, Mexico, and Italy.
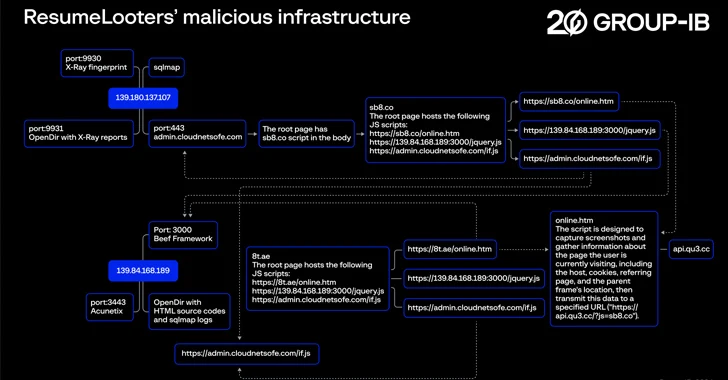
The modus operandi of ResumeLooters involves the use of the open-resource sqlmap resource to have out SQL injection assaults and fall and execute added payloads these as the BeEF (quick for Browser Exploitation Framework) penetration screening device and rogue JavaScript code intended to obtain sensitive knowledge and redirect end users to credential harvesting internet pages.
The cybersecurity firm’s assessment of the menace actor’s infrastructure reveals the existence of other tools like Metasploit, dirsearch, and xray, alongside a folder hosting the pilfered knowledge.

The campaign appears to be economically motivated, presented the point that ResumeLooters have set up two Telegram channels named 渗透数据中心 and 万国数据阿力 final calendar year to sell the data.
“ResumeLooters is nonetheless a further example of how much damage can be designed with just a handful of publicly readily available applications,” Rostovcev reported. “These assaults are fueled by lousy security as properly as insufficient database and web-site administration procedures.”
“It is placing to see how some of the oldest nevertheless remarkably efficient SQL attacks continue to be widespread in the location. On the other hand, the tenacity of the ResumeLooters team stands out as they experiment with numerous techniques of exploiting vulnerabilities, which includes XSS assaults.”
Located this write-up intriguing? Comply with us on Twitter and LinkedIn to study extra unique articles we put up.
Some parts of this article are sourced from:
thehackernews.com

 Recent SSRF Flaw in Ivanti VPN Products Undergoes Mass Exploitation
Recent SSRF Flaw in Ivanti VPN Products Undergoes Mass Exploitation