Google on Monday declared that it is simplifying the approach of enabling two-issue authentication (2FA) for customers with personal and Workspace accounts.
Also called, 2-Move Verification (2SV), it aims to incorporate an additional layer of security to users’ accounts to avoid takeover assaults in case the passwords are stolen.
The new change entails incorporating a second move method, these kinds of as an authenticator application or a hardware security vital, in advance of turning on 2FA, thus removing the have to have for employing the a lot less protected SMS-based authentication.
“This is notably handy for corporations utilizing Google Authenticator (or other equal time-based mostly a single-time password (TOTP) apps),” the enterprise claimed. “Previously, buyers had to help 2SV with a phone range just before remaining able to insert Authenticator.”
Buyers with hardware security keys have two solutions to insert them to their accounts, which include by registering a FIDO1 credential on the components key or by assigning a passkey (i.e., a FIDO2 credential) to a person.

Google notes that Workspace accounts could however be essential to enter their passwords alongside their passkey if the admin coverage for “Allow for consumers to skip passwords at sign-in by working with passkeys” is turned off.
In another noteworthy update, end users who decide to transform off 2FA from their account settings will now no lengthier have their enrolled next actions mechanically taken off.
“When an administrator turns off 2SV for a person from the Admin console or via the Admin SDK, the 2nd components will be taken out as prior to, to be certain user off-boarding workflows continue being unaffected,” Google stated.
The enhancement comes as the research huge reported above 400 million Google accounts have started out applying passkeys above the past 12 months for passwordless authentication.
Modern day authentication solutions and specifications like FIDO2 are created to resist phishing and session hijacking attacks by leveraging cryptographic keys produced by and connected to smartphones and computers in buy to verify consumers as opposed to a password that can be simply stolen via credential harvesting or stealer malware.
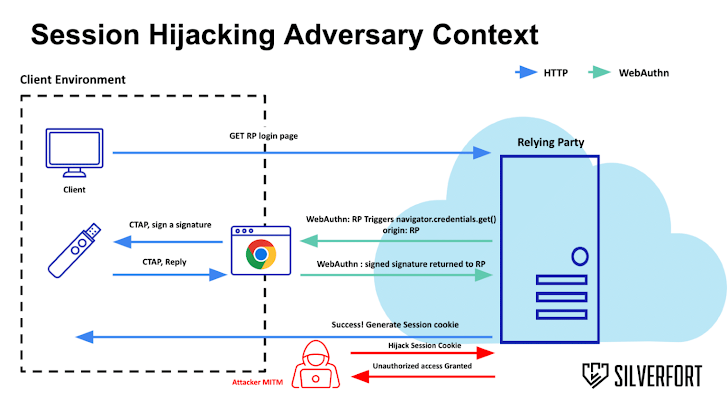
Even so, new research from Silverfort has located that a threat actor could get close to FIDO2 by staging an adversary-in-the-center (AitM) attack that can hijack consumer classes in programs that use one indicator-on (SSO) methods like Microsoft Entra ID, PingFederate, and Yubico.
“A profitable MitM attack exposes the whole request and response information of the authentication course of action,” security researcher Dor Segal saidsaid.
“When it finishes, the adversary can obtain the generated point out cookie and hijack the session from the sufferer. Set simply, there is no validation by the application following the authentication ends.”

The attack is designed probable owing to the fact that most programs do not shield the session tokens established immediately after authentication is successful, therefore allowing a poor actor to get unauthorized accessibility.
What is actually a lot more, there is no validation carried out on the product that requested the session, this means any product can use the cookie until it expires. This will make it doable to bypass the authentication stage by attaining the cookie by suggests of an AitM attack.
To ensure that the authenticated session is used entirely by the customer, it is recommended to adopt a technique known as token binding, which enables applications and services to cryptographically bind their security tokens to the Transportation Layer Security (TLS) protocol layer.
Whilst the token binding is minimal to Microsoft Edge, Google past thirty day period introduced a new element in Chrome called Gadget Bound Session Qualifications (DBSC) to assist secure customers versus session cookie theft and hijacking assaults.
Located this post interesting? Follow us on Twitter and LinkedIn to study extra exclusive content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Russian Operator of BTC-e Crypto Exchange Pleads Guilty to Money Laundering
Russian Operator of BTC-e Crypto Exchange Pleads Guilty to Money Laundering