Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Motor (GKE) that could be possibly exploited by risk actors with a Google account to choose handle of a Kubernetes cluster.
The critical shortcoming has been codenamed Sys:All by cloud security company Orca. As a lot of as 250,000 lively GKE clusters in the wild are estimated to be vulnerable to the attack vector.
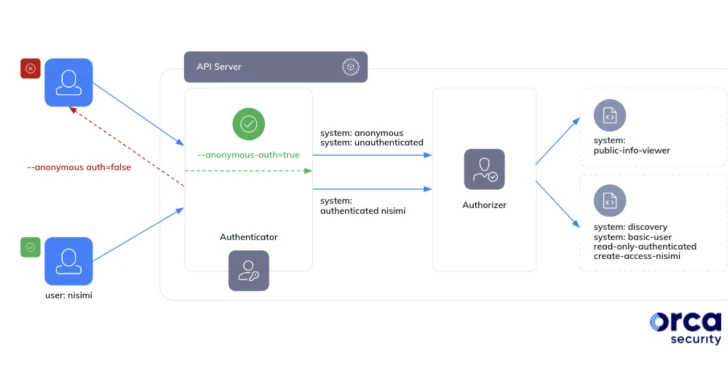
In a report shared with The Hacker Information, security researcher Ofir Yakobi claimed it “stems from a very likely common misunderstanding that the technique:authenticated group in Google Kubernetes Motor involves only confirmed and deterministic identities, whilst in fact, it includes any Google authenticated account (even outside the house the firm).”

The technique:authenticated group is a unique group that involves all authenticated entities, counting human users and support accounts. As a consequence, this could have severe effects when directors inadvertently bestow it with extremely permissive roles.
Exclusively, an external danger actor in possession of a Google account could misuse this misconfiguration by utilizing their very own Google OAuth 2. bearer token to seize control of the cluster for follow-on exploitation this sort of as lateral motion, cryptomining, denial-of-provider, and delicate information theft.
To make issues even worse, this method does not leave a trail in a way that can be joined back to the actual Gmail or Google Workspace account that obtained the OAuth bearer token.
Sys:All has been found to effect many organizations, leading to the publicity of several sensitive knowledge, these as JWT tokens, GCP API keys, AWS keys, Google OAuth credentials, personal keys, and credentials to container registries, the final of which could then be applied to trojanize container photos.
Following accountable disclosure to Google, the enterprise has taken ways to block the binding of the system:authenticated team to the cluster-admin job in GKE versions 1.28 and later on.
“To assist protected your clusters against mass malware attacks that exploit cluster-admin obtain misconfigurations, GKE clusters jogging variation 1.28 and later on will not likely allow you to bind the cluster-admin ClusterRole to the process:nameless consumer or to the technique:unauthenticated or technique:authenticated groups,” Google now notes in its documentation.

Google is also recommending people to not bind the procedure:authenticated group to any RBAC roles, as very well as assess irrespective of whether the clusters have been bound to the team applying both of those ClusterRoleBindings and RoleBindings and remove unsafe bindings.
Orca has also warned that though there is no general public report of a huge-scale attack employing this method, it could be only a issue of time, necessitating that buyers just take acceptable methods to safe their cluster accessibility controls.
“Even though this is an advancement, it is crucial to be aware that this continue to leaves a lot of other roles and permissions that can be assigned to the group,” the corporation reported.
Identified this short article exciting? Stick to us on Twitter and LinkedIn to examine additional distinctive information we publish.
Some parts of this article are sourced from:
thehackernews.com

 What is Nudge Security and How Does it Work?
What is Nudge Security and How Does it Work?