A new Android malware strain named Goldoson has been detected in the formal Google Enjoy Keep spanning more than 60 legit applications that collectively have over 100 million downloads.
An further eight million installations have been tracked through 1 shop, a primary third-get together app storefront in South Korea.
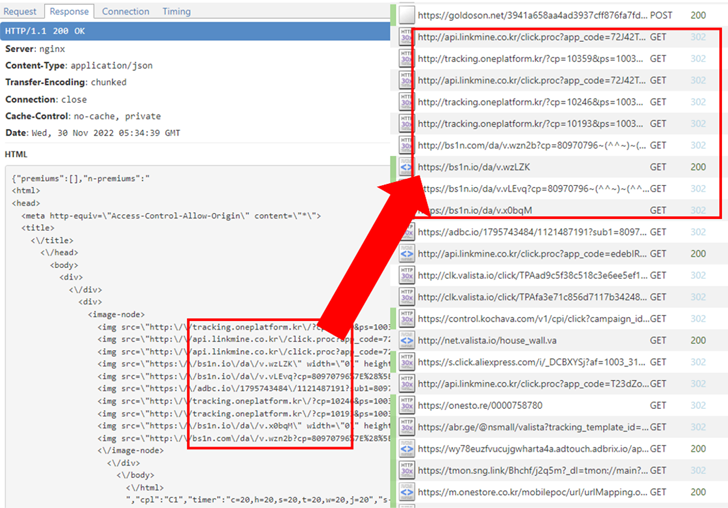
The rogue component is part of a third-get together computer software library utilized by the applications in problem and is able of gathering facts about mounted apps, Wi-Fi and Bluetooth-related products, and GPS spots.
“Also, the library is armed with the functionality to complete ad fraud by clicking commercials in the qualifications with out the user’s consent,” McAfee security researcher SangRyol Ryu stated in a report published very last week.
What is actually much more, it incorporates the means to stealthily load web internet pages, a characteristic that could be abused to load advertisements for economic financial gain. It achieves this by loading HTML code in a hidden WebView and driving targeted traffic to the URLs.
Pursuing accountable disclosure to Google, 36 of the 63 offending apps have been pulled from the Google Enjoy Retail outlet. The remaining 27 apps have been up-to-date to remove the destructive library.
Some of the prominent apps include things like –
- L.Position with L.Shell out
- Swipe Brick Breaker (taken out)
- Revenue Supervisor Expense & Spending budget
- TMAP – 대리,주차,전기차 충전,킥보드를 티맵에서!
- 롯데시네마
- 지니뮤직 – genie
- 컬쳐랜드[컬쳐캐쉬]
- GOM Participant
- 메가박스 (removed), and
- Dwell Rating, Authentic-Time Score
The conclusions emphasize the want for application developers to be transparent about the dependencies utilized in their program, not to point out consider satisfactory steps to safeguard users’ data from these types of abuse.
“Attackers are becoming additional complex in their attempts to infect in any other case authentic apps throughout platforms,” Kern Smith, vice president of income engineering for the Americas at Zimperium, reported.
“The use of third-party SDKs and code, and their prospective to introduce malicious code into or else authentic applications is only continuing to grow as attackers begin to target the software program source chain to achieve the major footprint probable.”
Forthcoming WEBINARMaster the Art of Dark Web Intelligence Accumulating
Understand the art of extracting menace intelligence from the dark web – Be part of this specialist-led webinar!
Conserve My Seat!
The progress arrives as Cyble took the wraps off a new Android banking trojan dubbed Chameleon that has been lively since January 2023 and is focusing on users in Australia and Poland.
The trojan is no diverse from other banking malware noticed in the wild owing to its abuse of Android’s accessibility services to harvest credentials and cookies, log keystrokes, stop its uninstallation, and carry out other nefarious things to do.
It truly is also designed to display screen rogue overlays on leading of a unique list of apps, intercept SMS messages, and even comprises an unused operation that allows it to down load and execute yet another payload.
Chameleon, correct to its name, has a penchant for evasion by incorporating anti-emulation checks to detect if the product is rooted or it is remaining executed in a debugging ecosystem, and if so, terminate by itself.
To mitigate these types of threats, buyers are suggested to only obtain apps from reliable sources, scrutinize app permissions, use strong passwords, permit multi-component authentication, and exercising warning when getting SMS or emails from unidentified senders.
Uncovered this report intriguing? Adhere to us on Twitter and LinkedIn to read more unique written content we post.
Some parts of this article are sourced from:
thehackernews.com


 WhatsApp, Signal Claim Online Safety Bill Threatens User Privacy and Safety
WhatsApp, Signal Claim Online Safety Bill Threatens User Privacy and Safety