A new destructive campaign has been observed hijacking GitHub accounts and committing malicious code disguised as Dependabot contributions with an purpose to steal passwords from developers.
“The destructive code exfiltrates the GitHub project’s defined insider secrets to a destructive C2 server and modify any current javascript information in the attacked task with a web-kind password-stealer malware code effecting any close-person distributing its password in a web type,” Checkmarx stated in a technical report.
The malware is also built to seize GitHub tricks and variables to a remote server by implies of a GitHub Action.

The application source chain security organization said it observed the atypical commits to hundreds of general public and non-public GitHub repositories among July 8 and 11, 2023.
It has emerged that the victims experienced their GitHub personal entry tokens stolen and utilised by the risk actors to make destructive code commits to users’ repositories by posing as Dependabot.
Dependabot is developed to inform consumers of security vulnerabilities in a project’s dependencies by routinely making pull requests to maintain them up-to-day.
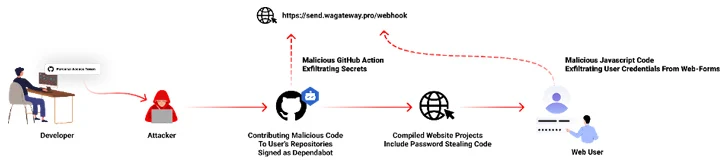
“The attackers accessed the accounts using compromised PATs (Personalized Obtain Token) — most very likely exfiltrated silently from the victim’s progress atmosphere,” the enterprise mentioned. Most compromised people are positioned in Indonesia.
Nevertheless, the exact technique by which this theft may have taken location is now unclear, although it truly is suspected that it may well have involved a rogue bundle inadvertently mounted by the developers.
The enhancement highlights the continued tries on aspect of threat actors to poison open up-source ecosystems and aid provide chain compromises.
This is evidenced by a new data exfiltration campaign focusing on both equally npm and PyPI that takes advantage of as numerous as 39 counterfeit offers to gather sensitive equipment facts and transmit the particulars to a distant server.
Forthcoming WEBINARFight AI with AI — Battling Cyber Threats with Next-Gen AI Instruments
Prepared to tackle new AI-pushed cybersecurity challenges? Be a part of our insightful webinar with Zscaler to handle the developing danger of generative AI in cybersecurity.
Supercharge Your Techniques
The modules, released in excess of several times amongst September 12 and 24, 2023, display a progressive improve in complexity, scope, and obfuscation approaches, Phylum said.
The Israeli company is also monitoring what it characterised as a large typosquat marketing campaign aimed at npm, in which 125 offers masquerading as angular and respond are becoming applied to send out machine facts to a remote Discord channel.
On the other hand, the activity seems to be portion of a “investigation venture,” with the author professing that it’s done to “uncover out if any of the bug bounty plans I’m participating in will get affected by just one of the deals so that I could be the 1st a person to notify them and guard their infrastructure.”
“This is in violation of the npm Suitable Use Coverage, and these sorts of strategies set a strain on people tasked with maintaining these ecosystems clean,” Phylum cautioned.
Uncovered this posting intriguing? Follow us on Twitter and LinkedIn to read a lot more exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com


 China’s BlackTech Hacking Group Exploited Routers to Target U.S. and Japanese Companies
China’s BlackTech Hacking Group Exploited Routers to Target U.S. and Japanese Companies