As lots of as 55 zero-working day vulnerabilities had been exploited in the wild in 2022, with most of the flaws identified in software package from Microsoft, Google, and Apple.
Though this figure signifies a lessen from the yr ahead of, when a staggering 81 zero-times ended up weaponized, it continue to signifies a important uptick in modern yrs of threat actors leveraging unknown security flaws to their gain.
The conclusions occur from threat intelligence agency Mandiant, which famous that desktop operating units (19), web browsers (11), IT and network administration products and solutions (10), and mobile working systems (six) accounted for the most exploited product or service types.
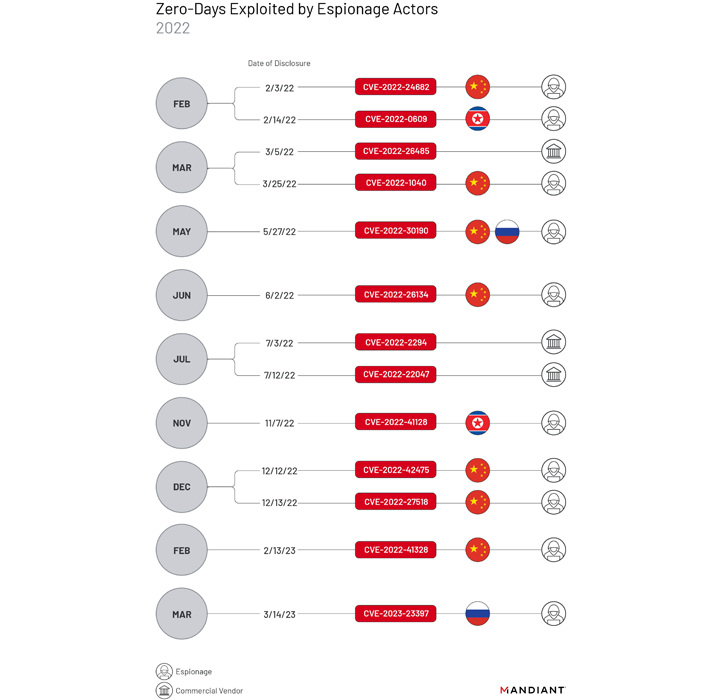
Of the 55 zero-day bugs, 13 are believed to have been abused by cyber espionage teams, with 4 other people exploited by monetarily motivated risk actors for ransomware-linked operations. Business spyware suppliers ended up linked to the exploitation of three zero-days.
Amongst state-sponsored groups, individuals attributed to China have emerged as the most prolific, exploiting 7 zero-times – CVE-2022-24682, CVE-2022-1040, CVE-2022-30190, CVE-2022-26134, CVE-2022-42475, CVE-2022-27518, and CVE-2022-41328 – during the year.
A lot of the exploitation has targeted on vulnerabilities in edge network products these types of as firewalls for acquiring preliminary entry. Several China-nexus clusters have also been noticed leveraging a flaw in Microsoft Diagnostics Software (aka Follina) as element of disparate strategies.
“A number of independent campaigns might reveal that the zero-day was dispersed to several suspected Chinese espionage clusters by using a digital quartermaster,” Mandiant claimed, including it points to the “existence of a shared advancement and logistics infrastructure and potentially a centralized coordinating entity.”

North Korean and Russian menace actors, on the other hand, have been connected to the exploitation of two zero-days every. This incorporates CVE-2022-0609, CVE-2022-41128, CVE-2022-30190, and CVE-2023-23397.
The disclosure comes as danger actors are also acquiring improved at turning recently disclosed vulnerabilities into powerful exploits for breaching a broad range of targets throughout the planet.
“While the discovery of zero-day vulnerabilities is a useful resource-intensive endeavor and effective exploitation is not assured, the overall variety of vulnerabilities disclosed and exploited has ongoing to improve, the kinds of qualified computer software, together with Internet of Issues (IoT) units and cloud alternatives, continue to evolve, and the selection of actors exploiting them has expanded,” Mandiant reported.
WEBINARDiscover the Concealed Hazards of 3rd-Occasion SaaS Apps
Are you mindful of the threats connected with 3rd-social gathering app entry to your company’s SaaS applications? Join our webinar to discover about the sorts of permissions getting granted and how to limit risk.
RESERVE YOUR SEAT
The Mandiant report also follows a warning from Microsoft’s Electronic Danger Assessment Centre about Russia’s persistent kinetic and cyber focusing on as the war in Ukraine continues into the second yr.
The tech giant stated considering the fact that January 2023 it has noticed “Russian cyber menace activity altering to improve damaging and intelligence gathering capacity on Ukraine and its partners’ civilian and army assets.”
It even further warned of a achievable “renewed damaging campaign” mounted by the nation-state team regarded as Sandworm (aka Iridium) on companies positioned in Ukraine and in other places.
What is additional, Moscow-backed hackers have deployed at minimum two ransomware and 9 wiper households towards more than 100 Ukrainian entities. No fewer than 17 European international locations have been qualified in espionage campaigns involving January and mid-February 2023, and 74 nations have been specific considering the fact that the start of the war.
Other important features associated with Russian danger activity contain the use of ransomware as weapons of cyber sabotage, getting first access via various solutions, and leveraging real and pseudo hacktivist groups to extend the achieve of Moscow’s cyber presence.
Discovered this posting interesting? Abide by us on Twitter and LinkedIn to go through more distinctive content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Ferrari Reveals Data Breach Ransom Attack
Ferrari Reveals Data Breach Ransom Attack