Bogus installers for Adobe Acrobat Reader are becoming utilised to distribute a new multi-practical malware dubbed Byakugan.
The starting off issue of the attack is a PDF file penned in Portuguese that, when opened, reveals a blurred graphic and asks the sufferer to simply click on a connection to down load the Reader application to look at the material.
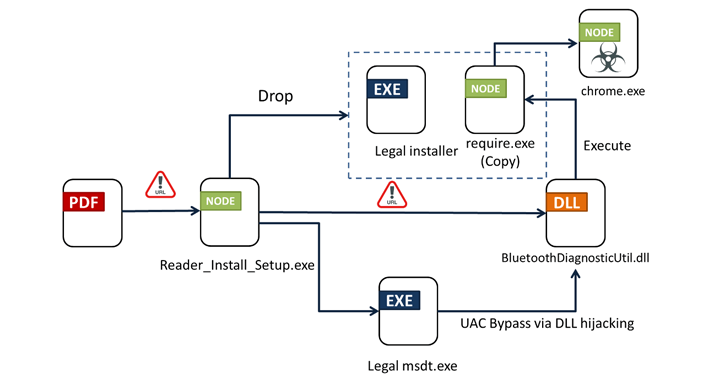
In accordance to Fortinet FortiGuard Labs, clicking the URL sales opportunities to the shipping and delivery of an installer (“Reader_Set up_Setup.exe”) that activates the infection sequence. Facts of the marketing campaign had been initially disclosed by the AhnLab Security Intelligence Centre (ASEC) final thirty day period.
The attack chain leverages methods like DLL hijacking and Windows User Obtain Manage (UAC) bypass to load a destructive dynamic-website link library (DLL) file named “BluetoothDiagnosticUtil.dll,” which, in transform, loads unleashes the last payload. It also deploys a genuine installer for a PDF reader like Wondershare PDFelement.
The binary is equipped to obtain and exfiltrate procedure metadata to a command-and-management (C2) server and fall the major module (“chrome.exe”) from a distinct server that also functions as its C2 for obtaining files and commands.
“Byakugan is a node.js-primarily based malware packed into its executable by pkg,” security researcher Pei Han Liao reported. “In addition to the primary script, there are quite a few libraries corresponding to attributes.”

This contains location up persistence, monitoring the victim’s desktop utilizing OBS Studio, capturing screenshots, downloading cryptocurrency miners, logging keystrokes, enumerating and uploading files, and grabbing details saved in web browsers.
“There is a expanding development to use equally clear and malicious parts in malware, and Byakugan is no exception,” Fortinet stated. “This approach will increase the total of sounds produced throughout examination, earning precise detections a lot more tricky.”
The disclosure will come as ASEC uncovered a new marketing campaign that propagates the Rhadamanthys info stealer less than the guise of an installer for groupware.
“The menace actor made a pretend internet site to resemble the primary site and exposed the web site to the customers working with the advert feature in lookup engines,” the South Korean cybersecurity company explained. “The malware in distribution makes use of the oblique syscall strategy to cover from the eyes of security remedies.”
It also follows a discovery that a manipulated version of Notepad++ is remaining employed by unidentified risk actors to propagate the WikiLoader malware (aka WailingCrab).
Identified this article attention-grabbing? Stick to us on Twitter and LinkedIn to read much more special information we article.
Some parts of this article are sourced from:
thehackernews.com

 New Wave of JSOutProx Malware Targeting Financial Firms in APAC and MENA
New Wave of JSOutProx Malware Targeting Financial Firms in APAC and MENA