The Iranian condition-sponsored group dubbed MuddyWater has been attributed to a beforehand unseen command-and-command (C2) framework known as PhonyC2 which is been set to use by the actor considering the fact that 2021.
Evidence demonstrates that the custom made produced, actively developed framework has been leveraged in the February 2023 attack on Technion, an Israeli investigate institute, cybersecurity company Deep Intuition reported in a report shared with The Hacker Information.
What’s more, additional hyperlinks have been unearthed concerning the Python 3-centered application and other assaults carried out by MuddyWater, such as the ongoing exploitation of PaperCut servers.
“It is structurally and functionally very similar to MuddyC3, a earlier MuddyWater custom C2 framework that was written in Python 2,” security researcher Simon Kenin claimed. “MuddyWater is repeatedly updating the PhonyC2 framework and altering TTPs to stay clear of detection.”
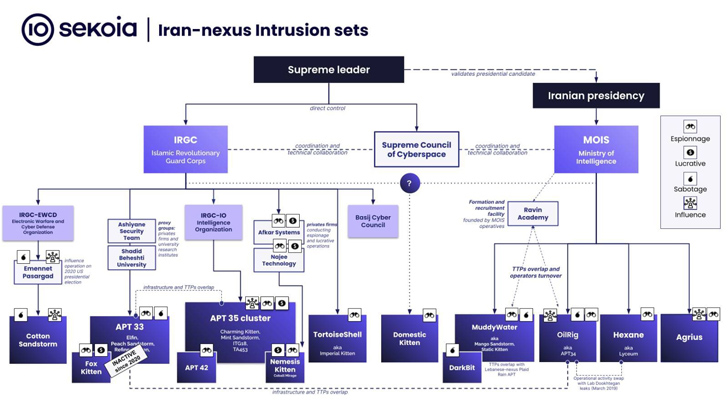
MuddyWater, also acknowledged as Mango Sandstorm (formerly Mercury), is a cyber espionage group that is acknowledged to operate on behalf of Iran’s Ministry of Intelligence and Security (MOIS) considering the fact that at the very least 2017.
The conclusions get there almost 3 months following Microsoft implicated the danger actor for carrying out harmful attacks on hybrid environments, when also contacting out its collaboration with a related cluster tracked as Storm-1084 (aka DEV-1084 or DarkBit) for reconnaissance, persistence, and lateral motion.

“Iran conducts cyber functions aiming at intelligence selection for strategic uses, basically targeting neighboring states, in distinct Iran’s geopolitical rivals this sort of as Israel, Saudi Arabia, and Arabic Gulf nations around the world, a ongoing target noticed in all operations considering that 2011,” French cybersecurity enterprise Sekoia mentioned in an overview of pro-Iranian authorities cyber attacks.
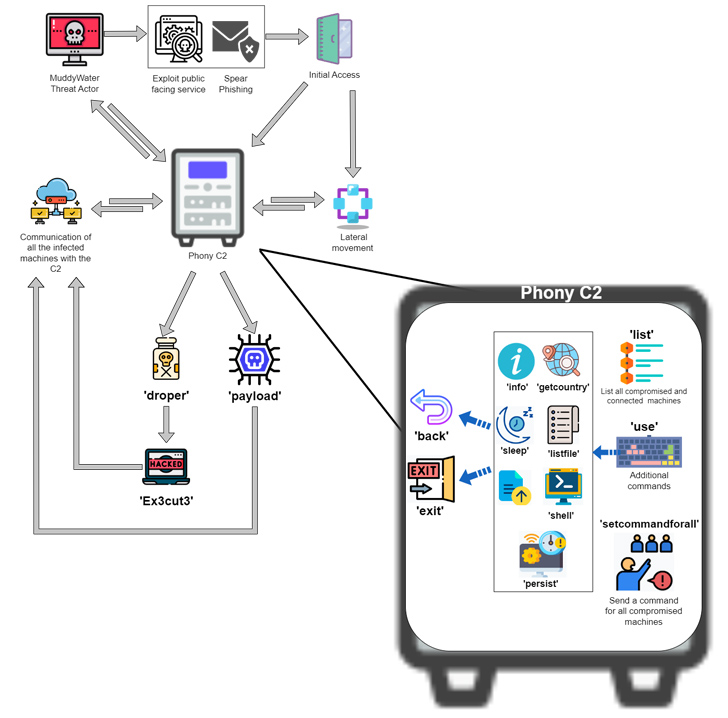
Attack chains orchestrated by the group, like other Iran-nexus intrusion sets, use susceptible community-dealing with servers and social engineering as the key first entry points to breach targets of fascination.
“These include the use of charismatic sock puppets, the lure of possible work alternatives, solicitation by journalists, and masquerading as imagine tank industry experts looking for thoughts,” Recorded Upcoming observed final year. “The use of social engineering is a central component of Iranian APT tradecraft when engaging in cyber espionage and information and facts operations.”
Deep Intuition claimed it discovered the PhonyC2 framework in April 2023 on a server that’s connected to broader infrastructure set to use by MuddyWater in its attack targeting Technion earlier this yr. The very same server was also observed to host Ligolo, a staple reverse tunneling instrument used by the threat actor.
The link stems from the artifact names “C:programdatadb.sqlite” and “C:programdatadb.ps1,” which Microsoft explained as personalized PowerShell backdoors used by MuddyWater and which are dynamically created through the PhonyC2 framework for execution on the infected host.
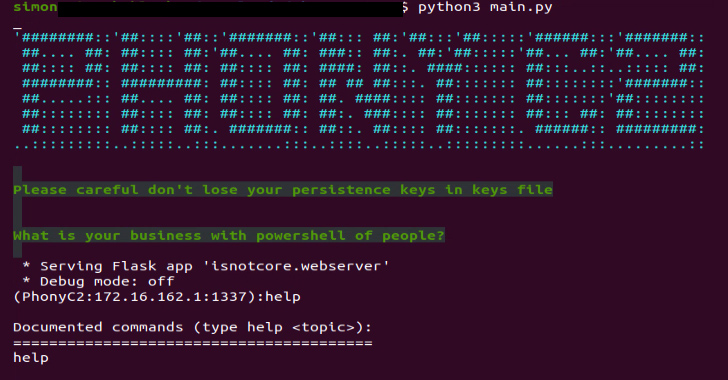
PhonyC2 is a “write-up-exploitation framework used to make different payloads that connect back to the C2 and hold out for guidance from the operator to conduct the closing step of the ‘intrusion kill chain,'” Kenin said, calling it a successor to MuddyC3 and POWERSTATS.

Some of the the notable commands supported by the framework are as follows –
- payload: Make the payloads “C:programdatadb.sqlite” and “C:programdatadb.ps1” as effectively as a PowerShell command to execute db.ps1, which, in flip, executes db.sqlite
- droper: Produce diverse variants of PowerShell commands to crank out “C:programdatadb.sqlite” by reaching out to the C2 server and crafting the encoded contents despatched by the server to the file
- Ex3minimize3: Develop different variants of PowerShell commands to generate “C:programdatadb.ps1” — a script that includes the logic to decode db.sqlite — and the final-phase
- listing: Enumerate all related equipment to the C2 server
- setcommandforall: Execute the same command throughout all linked hosts simultaneously
- use: Get a PowerShell shell on a distant computer system
- persist: Crank out a PowerShell code to allow the operator to get persistence on the contaminated host so it will hook up back again to the server upon a restart
Muddywater is much from the only Iranian country-condition team to train its eyes on Israel. In recent months, many entities in the region have been focused by at minimum 3 distinctive actors these as Charming Kitten (aka APT35), Imperial Kitten (aka Tortoiseshell), and Agrius (aka Pink Sandstorm).
Identified this write-up intriguing? Abide by us on Twitter and LinkedIn to read additional special information we article.
Some parts of this article are sourced from:
thehackernews.com


 Fluhorse: Flutter-Based Android Malware Targets Credit Cards and 2FA Codes
Fluhorse: Flutter-Based Android Malware Targets Credit Cards and 2FA Codes