Processing alerts swiftly and proficiently is the cornerstone of a Security Functions Centre (SOC) professional’s role. Menace intelligence platforms can noticeably greatly enhance their skill to do so. Let’s obtain out what these platforms are and how they can empower analysts.
The Challenge: Inform Overload
The modern day SOC faces a relentless barrage of security alerts produced by SIEMs and EDRs. Sifting by way of these alerts is equally time-consuming and source-intense. Analyzing a probable menace usually necessitates searching across various resources before getting conclusive proof to verify if it poses a actual risk. This course of action is further hampered by the stress of paying useful time investigating artifacts that finally flip out to be false positives.
As a consequence, a considerable portion of these activities keep on being uninvestigated. This highlights a critical problem: finding vital facts related to distinctive indicators speedily and precisely. Risk knowledge platforms supply a answer. These platforms help you to seem up any suspicious URL, IP, or other indicator and receive quick insights into its prospective risk. One particular this sort of platform is Danger Intelligence Lookup from ANY.Operate.
Threat Intelligence Platforms to the Rescue
Specialised platforms for SOC investigations leverage their databases of danger facts, aggregated from diverse sources. Acquire, for instance, ANY.RUN’s Risk Intelligence Lookup (TI Lookup). This platform collects Indicators of Compromise (IOCs) from tens of millions of interactive assessment classes (responsibilities) done within just the ANY.Operate sandbox.
The platform delivers an more dimension of risk knowledge: logs of processes, registry and network exercise, command line contents, and other program details produced throughout sandbox investigation periods. Users can then research for appropriate facts across these fields.
Danger Intelligence Platforms Gains
Deeper Visibility into Threats
In its place of relying on scattered details resources, these kinds of platforms offer a solitary issue of access to search for IOCs throughout several data details. This features URLs, file hashes, IP addresses, logged gatherings, command lines, and registries, permitting for far more detailed risk identification and investigation.
More rapidly Inform Investigations
When a security incident takes place, time is of the essence. TI platforms support assemble pertinent risk intelligence info fast, enabling a further knowing of the attack’s nature, influenced techniques, and compromise scope. This can appreciably pace up and improve response endeavours.
Proactive Threat Searching
Threat intelligence platforms empower groups to actively hunt for acknowledged IOCs affiliated with distinct malware families. This proactive tactic can help uncover hidden threats just before they escalate into key incidents.
They can deliver access to data that could possibly reveal likely vulnerabilities related with identified threats. This data can inform risk assessments and support corporations prioritize security efforts based mostly on the most urgent hazards.
Menace Investigation and Choice-Producing
Armed with in-depth insights into malware behavior, groups can a lot more properly assess threats and make informed selections about containment, remediation, and future preventative actions. This steady mastering cycle strengthens the over-all security posture and team competency.
Danger Intelligence System Query Illustrations
Exploring with Person Indicators

Envision you suspect a compromised technique inside of your network is downloading malicious files. You pinpoint a certain IP tackle as the opportunity supply and choose to investigate additional. Enter the IP tackle into the look for bar of a risk intelligence system. Instantly, the platform flags the address as malicious and linked to the Remcos malware, featuring facts on domains, ports, and even documents related with this IP.
It also delivers accessibility to investigation periods where by this IP tackle was concerned and lists Methods, Approaches, & Strategies (TTPs) utilized by malware in these classes.
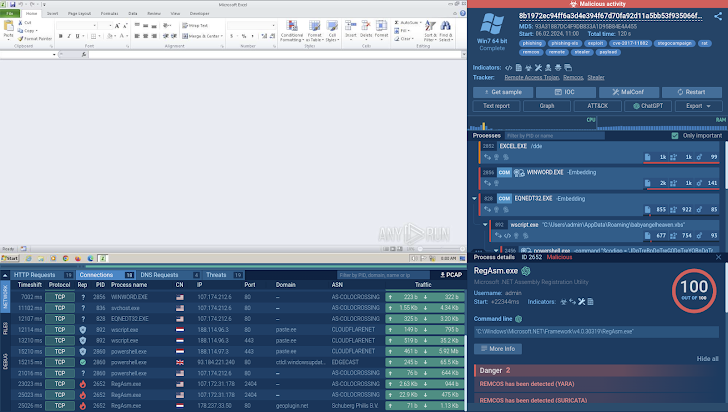
You can research each session in detail by basically clicking on it. The program will consider you to the session’s web page in the ANY.Run sandbox, wherever you will be ready to check out all the processes, connections, and registry exercise, as well as collect the malware’s config and IOCs or down load a extensive threat report.
Flexible Research with Wildcards
A further beneficial aspect of threat intelligence platforms like TI Lookup is the skill to submit wildcards and mixed queries.
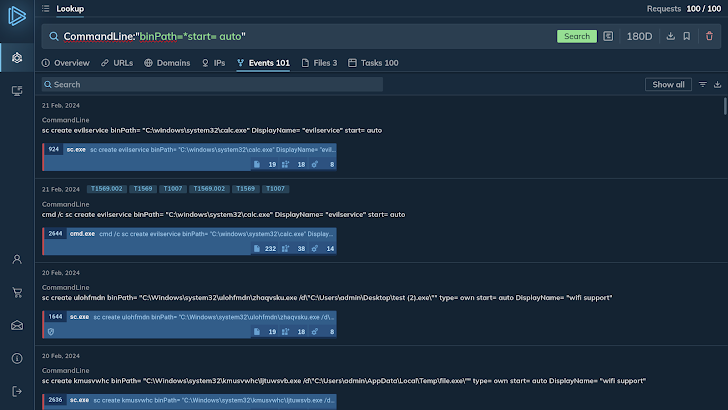
For occasion, the question “binPath=*start off= automobile” takes advantage of the asterisk wildcard and lookups for any command line with “binPath=” followed by any figures that stop with “commence= vehicle”.
The platform returns a hundred periods in which the very same fragment appeared. A closer examination of the research final results indicates that this specific command line artifact is characteristic of the Tofsee malware.
Blended Research Requests
One more alternative for conducting an investigation is to pool together all obtainable indicators and submit them to the risk intelligence system to establish all cases exactly where these criteria show up collectively.
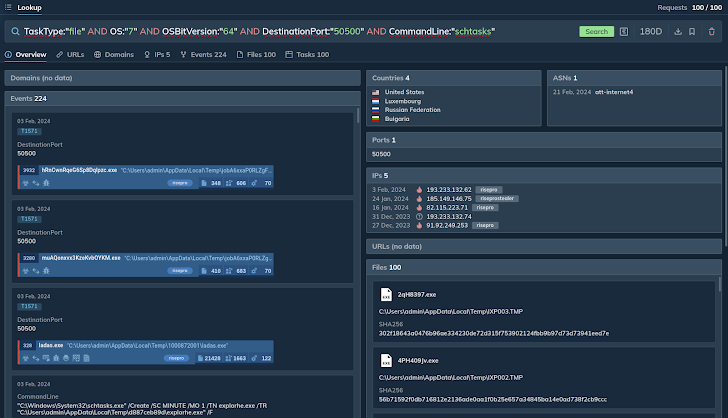
For example, you can build a question that searches for all tasks (sessions) categorized as “file,” operate on Windows 7, with a 64-bit running system, connecting to port 50500 and that contains the string “schtasks” in the command line.
The platform then identifies quite a few classes that meet the specified requirements and also offers a checklist of IPs tagged with “RisePro,” highlighting the malware responsible.
Test Menace Intelligence Lookup
Threat Intelligence Lookup from ANY.Operate lets you examine threats with precision. Review procedures, data files, network activity, and more. Refine your look for with 30+ fields, including IPs, domains, logged occasions, and MITRE tactics. Mix parameters for holistic knowledge. Use wildcard queries to increase your get to.
Request a trial to receive 50 totally free requests to investigate the platform.
Located this post attention-grabbing? This short article is a contributed piece from a single of our valued associates. Adhere to us on Twitter and LinkedIn to read far more special content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Five Eyes Agencies Expose APT29’s Evolving Cloud Attack Tactics
Five Eyes Agencies Expose APT29’s Evolving Cloud Attack Tactics