An Android voice phishing (aka vishing) malware marketing campaign regarded as FakeCalls has reared its head as soon as once more to goal South Korean consumers under the guise of above 20 well-liked economical apps.
“FakeCalls malware possesses the operation of a Swiss military knife, in a position not only to conduct its primary aim but also to extract non-public details from the victim’s machine,” cybersecurity firm Examine Point said.
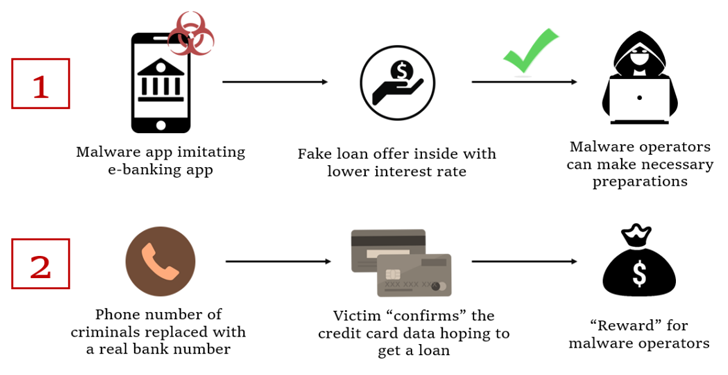
FakeCalls was beforehand documented by Kaspersky in April 2022, describing the malware’s abilities to imitate phone conversations with a lender consumer help agent.
In the noticed attacks, customers who set up the rogue banking app are enticed into calling the fiscal establishment by presenting a fake very low-curiosity bank loan.
At the place the place the phone connect with truly takes place, a pre-recorded audio with directions from the true bank is played. At the exact same time, malware also conceals the phone selection with the bank’s serious variety to give the perception that a dialogue is going on with an precise bank personnel on the other conclusion.
The final intention of the marketing campaign to get the victim’s credit card details, which the menace actors assert is expected to qualify for the non-existent personal loan.
The malicious app also requests for intrusive permissions so as to harvest sensitive knowledge, including stay audio and movie streams, from the compromised gadget, which are then exfiltrated to a distant server.
The most current FakeCalls samples additional apply numerous strategies to keep below the radar. A person of the methods requires introducing a large amount of files inside of nested directories to the APK’s asset folder, causing the size of the file title and route to breach the 300-character restrict.
“The malware builders took specific treatment with the technical facets of their generation as nicely as employing numerous exclusive and successful anti-evaluation strategies,” Examine Point stated. “In addition, they devised mechanisms for disguised resolution of the command-and-handle servers guiding the operations.”
Although the attack exclusively focuses on South Korea, the cybersecurity organization has warned that the very same practices can be repurposed to focus on other regions across the world.
The results also arrive as Cyble lose light on two Android banking trojans dubbed Nexus and GoatRAT that can harvest precious details and carry out financial fraud.
Nexus, a rebranded version of SOVA, also incorporates a ransomware module that encrypts the saved data files and can abuse Android’s accessibility expert services to extract seed phrases from cryptocurrency wallets.
WEBINARDiscover the Hidden Hazards of 3rd-Get together SaaS Apps
Are you knowledgeable of the threats associated with third-social gathering app obtain to your firm’s SaaS apps? Join our webinar to learn about the kinds of permissions being granted and how to lower risk.
RESERVE YOUR SEAT
In contrast, GoatRAT is made to target Brazilian financial institutions and joins the likes of BrasDex and PixPirate to commit fraudulent dollars transfer about the PIX payments platform though displaying a faux overlay window to conceal the activity.
The advancement is part of a rising development wherever threat actors have unleashed ever more innovative banking malware to automate the total course of action of unauthorized funds transfers on infected products.
Cybersecurity business Kaspersky stated it detected 196,476 new mobile banking trojans and 10,543 new cellular ransomware trojans in 2022, with China, Syria, Iran, Yemen, and Iraq emerging as the best countries attacked by cell malware, such as adware.
Spain, Saudi Arabia, Australia, Turkey, China, Switzerland, Japan, Colombia, Italy, and India direct the checklist of top rated countries contaminated by cellular money threats.
“In spite of the drop in general malware installers, the ongoing expansion of cell banking Trojans is a crystal clear indicator that cybercriminals are concentrating on money get,” Kaspersky researcher Tatyana Shishkova stated.
Observed this article exciting? Stick to us on Twitter and LinkedIn to go through additional special content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Telegram, WhatsApp Trojanized to Target Cryptocurrency Wallets
Telegram, WhatsApp Trojanized to Target Cryptocurrency Wallets