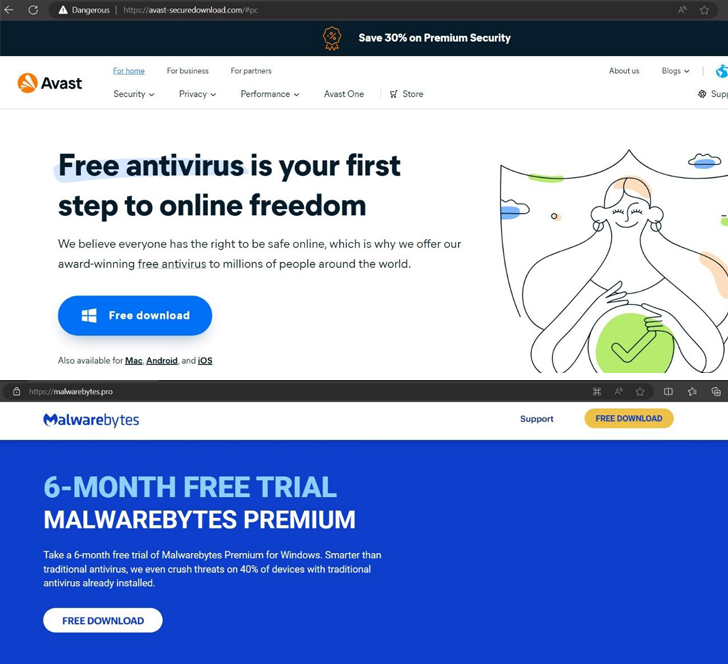
Menace actors have been observed producing use of phony internet websites masquerading as genuine antivirus remedies from Avast, Bitdefender, and Malwarebytes to propagate malware capable of stealing sensitive details from Android and Windows products.
“Hosting destructive program through web sites which seem respectable is predatory to typical people, specifically these who appear to safeguard their units from cyber attacks,” Trellix security researcher Gurumoorthi Ramanathan said.
The listing of internet websites is down below –
- avast-securedownload[.]com, which is applied to deliver the SpyNote trojan in the sort of an Android package deal file (“Avast.apk”) that, at the time mounted, requests for intrusive permissions to examine SMS messages and connect with logs, set up and delete apps, acquire screenshot, monitor area, and even mine cryptocurrency
- bitdefender-application[.]com, which is utilised to supply a ZIP archive file (“set up-gain-x86-x64.exe.zip”) that deploys the Lumma info stealer malware
- malwarebytes[.]pro, which is applied to provide a RAR archive file (“MBSetup.rar”) that deploys the StealC info stealer malware
The cybersecurity organization stated it also uncovered a rogue Trellix binary named “AMCoreDat.exe” that serves as a conduit to drop a stealer malware able of harvesting target information and facts, which include browser information, and exfiltrating it to a remote server.

It is now not very clear how these bogus web-sites are distributed, but equivalent strategies in the past have employed tactics such as malvertising and look for motor optimization (Web optimization) poisoning.
Stealer malware have progressively turn into a frequent threat, with cybercriminals promotion various customized variants with varying amounts of complexity. This consists of new stealers like Acrid, SamsStealer, ScarletStealer, and Waltuhium Grabber, as well as updates to current types such as SYS01stealer (aka Album Stealer or S1deload Stealer).
“The point that new stealers surface just about every now and then, combined with the simple fact that their performance and sophistication may differ considerably, signifies that there is a criminal marketplace demand from customers for stealers,” Kaspersky claimed in a latest report.
The progress comes as scientists have found a new Android banking trojan called Antidot that disguises itself as a Google Enjoy update to facilitate information and facts theft by abusing Android’s accessibility and MediaProjection APIs.
“Features-smart Antidot is capable of keylogging, overlay assaults, SMS exfiltration, monitor captures, credentials theft, gadget handle, and execution of instructions received from the attackers,” Broadcom-owned Symantec said in a bulletin.
Uncovered this post attention-grabbing? Adhere to us on Twitter and LinkedIn to browse additional unique articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 How Do Hackers Blend In So Well? Learn Their Tricks in This Expert Webinar
How Do Hackers Blend In So Well? Learn Their Tricks in This Expert Webinar