A remarkably focused cyber attack versus an East Asian IT company concerned the deployment of a tailor made malware penned in Golang identified as RDStealer.
“The operation was energetic for additional than a yr with the stop objective of compromising credentials and details exfiltration,” Bitdefender security researcher Victor Vrabie claimed in a technical report shared with The Hacker Information.
Proof collected by the Romanian cybersecurity business shows that the campaign commenced in early 2022. The focus on was an unspecified IT corporation located in East Asia.
In the early phases, the procedure relied on quickly accessible distant entry trojans like AsyncRAT and Cobalt Strike, in advance of transitioning to bespoke malware in late 2021 or early 2022 in a bid to thwart detection.
A major evasion tactic issues the use of Microsoft Windows folders that are probable to be excluded from scanning by security software package (e.g., System32 and Software Files) to retail outlet the backdoor payloads.

A single of the sub-folders in issue is “C:Plan FilesDellCommandUpdate,” which is the listing for a genuine Dell software known as Dell Command | Update.
Bitdefender reported all the equipment infected over the training course of the incident have been made by Dell, suggesting that the risk actors intentionally selected this folder to camouflage the destructive activity.
This line of reasoning is bolstered by the point that the danger actor registered command-and-control (C2) domains these kinds of as “dell-a[.]ntp-update[.]com” with the purpose of blending in with the target setting.
The intrusion established is characterised by the use of a server-aspect backdoor called RDStealer, which specializes in gathering clipboard information and keystroke details from the host.
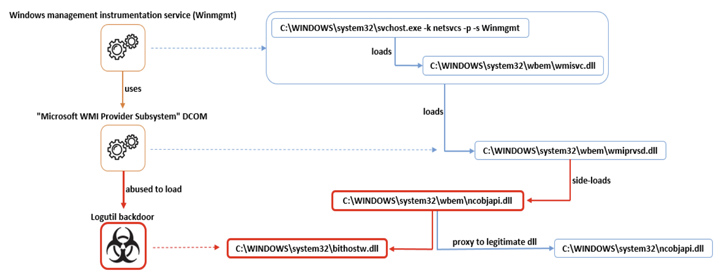
But what would make it stand out is its ability to “watch incoming RDP [Remote Desktop Protocol] connections and compromise a distant device if consumer travel mapping is enabled.”
Consequently when a new RDP consumer connection is detected, instructions are issued by RDStealer to exfiltrate sensitive information, this kind of as browsing heritage, qualifications, and personal keys from applications like mRemoteNG, KeePass, and Google Chrome.
“This highlights the simple fact that danger actors actively seek qualifications and saved connections to other systems,” Bitdefender’s Marin Zugec reported in a second investigation.
Approaching WEBINAR🔐 Mastering API Security: Comprehension Your Genuine Attack Area
Explore the untapped vulnerabilities in your API ecosystem and acquire proactive techniques in the direction of ironclad security. Be part of our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:soon afterdisplay:inline-block.verify_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-appropriate-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimension:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:just afterwidth:50pxheight:6pxcontent:”border-top:2px strong #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-pounds:900textual content-align:leftline-top:33px.wn-descriptiontext-align:leftfont-dimension:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
What’s more, the connecting RDP clients are infected with a different Golang-centered tailor made malware identified as Logutil to maintain a persistent foothold on the sufferer network making use of DLL facet-loading techniques and facilitate command execution.
Not significantly is regarded about the danger actor other than the point that it has been energetic courting back to at minimum 2020.
“Cybercriminals continually innovate and check out novel approaches to greatly enhance the trustworthiness and stealthiness of their destructive activities,” Zugec stated.
“This attack serves as a testomony to the escalating sophistication of fashionable cyber assaults, but also underscores the actuality that menace actors can leverage their newfound sophistication to exploit more mature, broadly adopted systems.”
Observed this short article fascinating? Observe us on Twitter and LinkedIn to go through more distinctive content we article.
Some parts of this article are sourced from:
thehackernews.com


 ASUS Releases Patches to Fix Critical Security Bugs Impacting Multiple Router Models
ASUS Releases Patches to Fix Critical Security Bugs Impacting Multiple Router Models