Numerous menace actors have been noticed opportunistically weaponizing a now-patched critical security vulnerability impacting many Zoho ManageEngine merchandise because January 20, 2023.
Tracked as CVE-2022-47966 (CVSS score: 9.8), the remote code execution flaw permits a full takeover of the susceptible techniques by unauthenticated attackers.
As several as 24 unique items, like Obtain Supervisor In addition, ADManager As well as, ADSelfService Additionally, Password Manager Pro, Remote Accessibility As well as, and Distant Checking and Management (RMM), are impacted by the issue.
The shortcoming “will allow unauthenticated remote code execution thanks to utilization of an out-of-date third-bash dependency for XML signature validation, Apache Santuario,” Bitdefender’s Martin Zugec mentioned in a technical advisory shared with The Hacker News.
In accordance to the Romanian cybersecurity firm, the exploitation initiatives are said to have commenced the working day just after penetration testing business Horizon3.ai produced a proof-of-strategy (PoC) final month.
A bulk of the attack victims are found in Australia, Canada, Italy, Mexico, the Netherlands, Nigeria, Ukraine, the U.K., and the U.S.
The primary aim of the attacks detected to day revolves all around deploying resources on vulnerable hosts such as Netcat and Cobalt Strike Beacon.
Some intrusions have leveraged the original entry to install AnyDesk computer software for remote obtain, although a couple of others have tried to put in a Windows edition of a ransomware pressure recognised as Buhti.
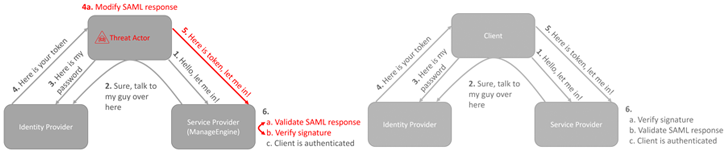
What’s extra, there is proof of a focused espionage procedure, with the threat actors abusing the ManageEngine flaw to deploy malware able of executing following-stage payloads.
“This vulnerability is a different distinct reminder of the value of maintaining programs up to day with the newest security patches whilst also employing solid perimeter protection,” Zugec mentioned.
“Attackers really don’t want to scour for new exploits or novel techniques when they know that lots of businesses are susceptible to older exploits due, in element, to the absence of suitable patch management and risk management.”
Uncovered this short article attention-grabbing? Adhere to us on Twitter and LinkedIn to browse additional distinctive written content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Researchers focus AI on finding exoplanets
Researchers focus AI on finding exoplanets