A destructive Python package uploaded to the Python Deal Index (PyPI) has been uncovered to comprise a thoroughly-highlighted details stealer and remote access trojan.
The bundle, named colourfool, was discovered by Kroll’s Cyber Threat Intelligence team, with the company calling the malware Color-Blind.
“The ‘Colour-Blind’ malware factors to the democratization of cybercrime that could lead to an intensified danger landscape, as various variants can be spawned from code sourced from others,” Kroll scientists Dave Truman and George Glass mentioned in a report shared with The Hacker Information.
colourfool, like other rogue Python modules identified in current months, conceals its malicious code in the setup script, which details to a ZIP archive payload hosted on Discord.
The file contains a Python script (code.py) that will come with various modules developed to log keystrokes, steal cookies, and even disable security software package.
The malware, other than doing protection evasion checks to identify if it really is staying executed in a sandbox, establishes persistence by usually means of a Visual Basic script and takes advantage of transfer[.]sh for details exfiltration.
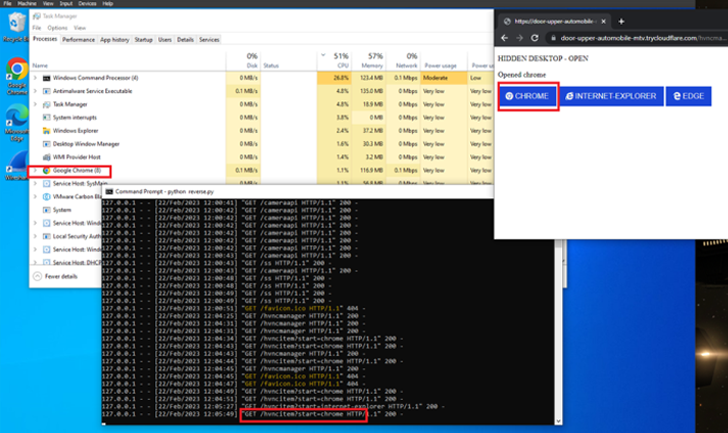
“As a approach of remote handle, the malware begins a Flask web software, which it helps make obtainable to the internet through Cloudflare’s reverse tunnel utility ‘cloudflared,’ bypassing any inbound firewall policies,” the scientists mentioned.
The use of Cloudflare tunnels mirrors one more marketing campaign that was disclosed by Phylum very last thirty day period which designed use of 6 fraudulent deals to distribute a stealer-cum-RAT dubbed poweRAT.
The trojan is function prosperous and is able of collecting passwords, terminating programs, taking screenshots, logging keystrokes, opening arbitrary web web pages on a browser, executing instructions, capturing crypto wallet info, and even snooping on victims via the web digicam.
The results come as danger actors are leveraging the source code linked with W4SP stealer to spawn copycat variations that are dispersed by using Python packages like ratebypass, imagesolverpy, and 3m-promo-gen-api.
What’s extra, Phylum found 3 a lot more packages – named pycolured, pycolurate, and colurful – that have been employed to supply a Go-based remote entry trojan referred to as Spark.
Adding to the attacks targeting PyPI, the program offer chain security agency also discovered details of a enormous attack marketing campaign wherein unfamiliar menace actors revealed as numerous as 1,138 deals to deploy a Rust executable, which is then used to fall supplemental malware binaries.
“The risk/reward proposition for attackers is well really worth the somewhat minuscule time and energy, if they can land a whale with a unwanted fat crypto wallet,” the Phylum exploration team explained.
“And the decline of a few bitcoin pales in comparison to the opportunity harm of the decline of a developer’s SSH keys in a substantial enterprise these types of as a corporation or government.”
Identified this short article interesting? Comply with us on Twitter and LinkedIn to read through additional exclusive information we post.
Some parts of this article are sourced from:
thehackernews.com


 Russian Government Bans Foreign Messaging Apps
Russian Government Bans Foreign Messaging Apps