A new investigation of the sophisticated industrial spyware named Predator has revealed that its potential to persist involving reboots is supplied as an “increase-on attribute” and that it relies upon on the licensing alternatives opted by a client.
“In 2021, Predator spy ware couldn’t survive a reboot on the infected Android technique (it had it on iOS),” Cisco Talos researchers Mike Gentile, Asheer Malhotra, and Vitor Ventura said in a report shared with The Hacker Information. “Nevertheless, by April 2022, that ability was staying offered to their customers.”
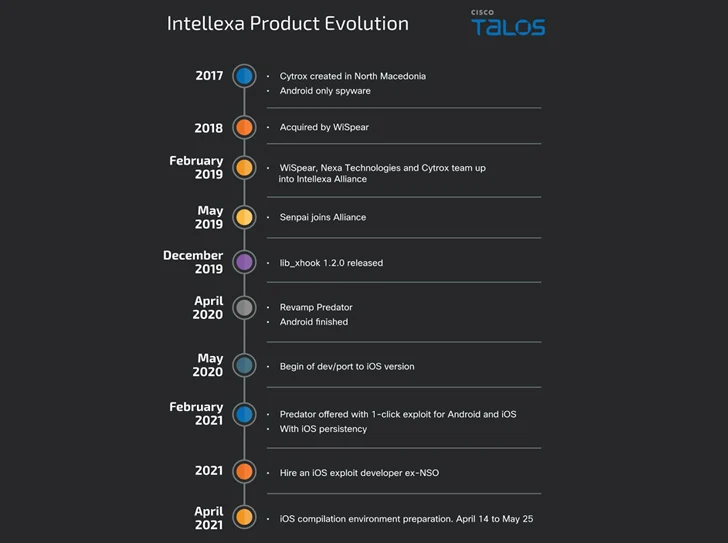
Predator is the solution of a consortium known as the Intellexa Alliance, which incorporates Cytrox (subsequently acquired by WiSpear), Nexa Systems, and Senpai Systems. The two Cytrox and Intellexa were being additional to the Entity List by the U.S. in July 2023 for “trafficking in cyber exploits utilised to attain access to information and facts methods.”
The most current conclusions occur much more than six months immediately after the cybersecurity vendor in depth the internal workings of Predator and its harmonious equation with yet another loader element referred to as Alien.
“Alien is vital to Predator’s prosperous working, which includes the further components loaded by Predator on desire,” Malhotra advised The Hacker News at the time. “The marriage among Alien and Predator is very symbiotic, requiring them to continuously operate in tandem to spy on victims.”
Future WEBINAR Conquer AI-Powered Threats with Zero Belief – Webinar for Security Pros
Classic security steps would not slash it in present-day planet. It’s time for Zero Belief Security. Protected your data like hardly ever before.
Be part of Now
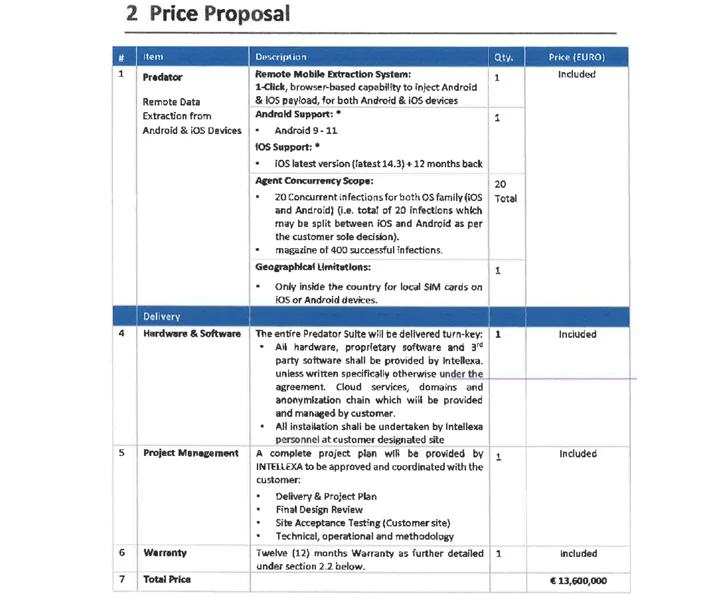
Predator, which can focus on each Android and iOS, has been described as a “distant mobile extraction technique” which is bought on a licensing product that operate into tens of millions of bucks based on the exploit made use of for first obtain and the amount of concurrent bacterial infections, putting them out of arrive at of script kiddies and amateur criminals.
Spyware such as Predator and Pegasus, which is produced by NSO Team, typically count on zero-day exploit chains in Android, iOS, and web browsers as covert intrusion vectors. As Apple and Google go on to plug the security gaps, these exploit chains may well be rendered ineffective, forcing them to go back to the drawing board.
Even so, it is value noting that the organizations behind mercenary surveillance instruments can also procure either entire or partial exploit chains from exploit brokers and vogue them into an operational exploit that can be employed to proficiently breach concentrate on gadgets.
Yet another crucial part of Intellexa’s business enterprise model is that offloads the get the job done of environment up the attack infrastructure to the clients by themselves, leaving it with area for plausible deniability need to the campaigns come to gentle (as it inevitably does).
“The delivery of Intellexa’s supporting hardware is accomplished at a terminal or airport,” the scientists mentioned.
“This shipping approach is acknowledged as Price Insurance policies and Freight (CIF), which is element of the shipping and delivery industry’s jargon (‘Incoterms’). This system lets Intellexa to declare that they have no visibility of where the systems are deployed and inevitably found.”

On major of that, Intellexa possesses “very first-hand information” of whether their clients are doing surveillance functions exterior their individual borders owing to the reality that the operations are intrinsically related to the license, which, by default, is limited to a solitary phone country code prefix.
This geographic limitation, nevertheless, can be loosened for an further rate.
Cisco Talos noted that when general public exposure of personal-sector offensive actors and their campaigns have been successful at attribution attempts, it has experienced minimal impression on their capacity to carry out and improve their business enterprise throughout the planet, even if it could impact their buyers, these types of as governments.
“It may perhaps boost the costs by earning them invest in or build new exploit chains but these suppliers seem to have seamlessly obtained new exploit chains, enabling them to continue being in business by leaping from just one established of exploits to a different as a usually means of initial accessibility,” the researchers said.
“What is desired is the public disclosure of specialized analyses of the cell spy ware and tangible samples enabling general public scrutiny of the malware. These types of community disclosures will not only enable greater analyses and generate detection initiatives but also impose progress expenses on sellers to continually evolve their implants.”
Located this report appealing? Follow us on Twitter and LinkedIn to read through far more distinctive written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication
Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication