An energetic Android malware campaign dubbed Exotic Check out has been principally concentrating on people in South Asia, specifically those people in India and Pakistan, with malware dispersed by using committed internet websites and Google Engage in Keep.
Slovak cybersecurity firm said the activity, ongoing because November 2021, is not joined to any acknowledged menace actor or team. It is really tracking the group at the rear of the procedure less than the identify Digital Invaders.
“Downloaded applications present authentic performance, but also contain code from the open up-resource Android XploitSPY RAT,” ESET security researcher Lukáš Štefanko stated in a technological report produced now.
The campaign is said to be very specific in character, with the apps offered on Google Perform getting negligible selection of installs ranging from zero to 45. The apps have considering that been taken down.

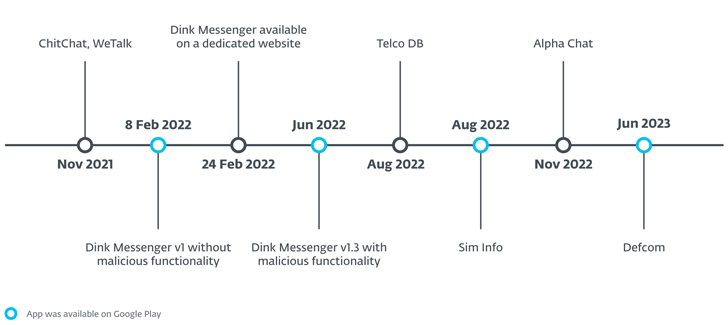
The fake-but-practical apps primarily masquerade as messaging products and services like Alpha Chat, ChitChat, Defcom, Dink Messenger, Signal Lite, TalkU, WeTalk, Wicker Messenger, and Zaangi Chat. Somewhere around 380 victims are said to have downloaded the applications and produced accounts to use them for messaging applications.
Also employed as component of Unique Take a look at are applications these as Sim Facts and Telco DB, both of those of which claim to present specifics about SIM entrepreneurs just by moving into a Pakistan-primarily based phone range. Other apps move off as a meals purchasing company in Pakistan as perfectly as a genuine Indian healthcare facility referred to as Expert Clinic (now rebranded as Trilife Medical center).
XploitSPY, uploaded to GitHub as early as April 2020 by a user named RaoMK, is affiliated with an Indian cyber security solutions company referred to as XploitWizer. It has also been described as a fork of a further open-supply Android trojan identified as L3MON, which, in switch, attracts inspiration from AhMyth.
It comes with a wide gamut of functions that will allow it to get sensitive info from contaminated units, this sort of as GPS spots, microphone recordings, contacts, SMS messages, connect with logs, and clipboard articles extract notification specifics from apps like WhatsApp, Facebook, Instagram, and Gmail download and add documents perspective put in applications and queue commands.
On leading of that, the malicious apps are designed to get photos and enumerate files in a number of directories associated to screenshots, WhatApp, WhatsApp Organization, Telegram, and an unofficial WhatsApp mod regarded as GBWhatsApp.

“All through the a long time, these threat actors have custom-made their destructive code by including obfuscation, emulator detection, hiding of [command-and-control] addresses, and use of a native library,” Štefanko stated.
The key reason of the native library (“defcome-lib.so”) is to continue to keep the C2 server facts encoded and concealed from static analysis tools. If an emulator is detected, the app will make use of a fake C2 server to evade detection.
Some of the applications have been propagated by means of web-sites specially created for this function (“chitchat.ngrok[.]io”) that give a website link to an Android bundle file (“ChitChat.apk”) hosted on GitHub. It is really presently not crystal clear how victims are directed to these applications.
“Distribution started on committed websites and then even moved to the formal Google Perform retail store,” Štefanko concluded. “The intent of the marketing campaign is espionage and probably is focusing on victims in Pakistan and India.”
Observed this post exciting? Comply with us on Twitter and LinkedIn to go through much more exceptional content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Raspberry Robin Returns: New Malware Campaign Spreading Through WSF Files
Raspberry Robin Returns: New Malware Campaign Spreading Through WSF Files