The menace actors at the rear of the BlackCat ransomware have shut down their darknet site and most likely pulled an exit scam after uploading a bogus law enforcement seizure banner.
“ALPHV/BlackCat did not get seized. They are exit scamming their affiliates,” security researcher Fabian Wosar reported. “It is blatantly evident when you verify the supply code of the new takedown observe.”
“There is unquestionably zero purpose why legislation enforcement would just set a saved edition of the takedown recognize up in the course of a seizure as a substitute of the primary takedown recognize.”
The U.K.’s Countrywide Criminal offense Company (NCA) instructed Reuters that it experienced no link to any disruptions to the BlackCat infrastructure.
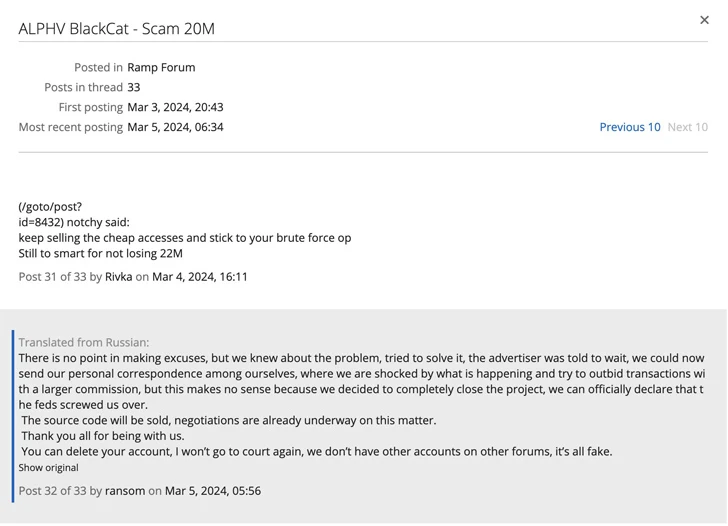
Recorded Long term security researcher Dmitry Smilyanets posted screenshots on the social media system X in which the BlackCat actors claimed that the “feds screwed us more than” and that they supposed to market the ransomware’s source code for $5 million.
The disappearing act comes after it allegedly acquired a $22 million ransom payment from UnitedHealth’s Change Health care device (Optum) and refused to share the proceeds with an affiliate that had carried out the attack.

The business has not commented on the alleged ransom payment, in its place stating it is only targeted on investigation and restoration features of the incident.
In accordance to DataBreaches, the disgruntled affiliate – which experienced its account suspended by the administrative personnel – created the allegations on the RAMP cybercrime discussion board. “They emptied the wallet and took all the income,” they claimed.
This has lifted speculations that BlackCat has staged an exit rip-off to evade scrutiny and resurface in the future underneath a new model. “A re-branding is pending,” a now-previous admin of the ransomware group was quoted as saying.
BlackCat experienced its infrastructure seized by legislation enforcement in December 2023, but the e-crime gang managed to wrest control of their servers and restart its functions without the need of any main implications. The group previously operated below the monikers DarkSide and BlackMatter.
“Internally, BlackCat may perhaps be nervous about moles in their group, and closing up shop preemptively could halt a takedown before it occurs,” Malachi Walker, a security advisor with DomainTools, explained.
“On the other hand, this exit scam may possibly basically be an opportunity for BlackCat to take the money and operate. Considering that crypto is after all over again at an all-time significant, the gang can get absent with selling their product or service ‘high.’ In the cybercrime earth, status is everything, and BlackCat appears to be to be burning bridges with its affiliates with these steps.”
The group’s evident demise and the abandonment of its infrastructure occur as malware exploration team VX-Underground claimed that the LockBit ransomware procedure no for a longer period supports Lockbit Red (aka Lockbit 2.) and StealBit, a customized software utilised by the danger actor for facts exfiltration.

LockBit has also tried to help you save experience by relocating some of its pursuits to a new dark web portal after a coordinated regulation enforcement operation took down its infrastructure final month following a months-very long investigation.
It also arrives as Pattern Micro unveiled that the ransomware family members regarded as RA Earth (formerly RA Group) has effectively infiltrated healthcare, finance, and insurance policy corporations in the U.S., Germany, India, Taiwan, and other international locations considering the fact that emerging in April 2023.
Assaults mounted by the team “entail multi-phase factors developed to make certain maximum affect and results in the group’s operations,” the cybersecurity firm mentioned.
Uncovered this short article interesting? Adhere to us on Twitter and LinkedIn to go through extra special articles we submit.
Some parts of this article are sourced from:
thehackernews.com


 A New Way To Manage Your Web Exposure: The Reflectiz Product Explained
A New Way To Manage Your Web Exposure: The Reflectiz Product Explained