A new info stealer named ExelaStealer has develop into the most current entrant to an presently crowded landscape stuffed with different off-the-shelf malware created to capture delicate details from compromised Windows techniques.
“ExelaStealer is a mainly open up-source infostealer with paid customizations available from the risk actor,” Fortinet FortiGuard Labs researcher James Slaughter reported in a complex report.
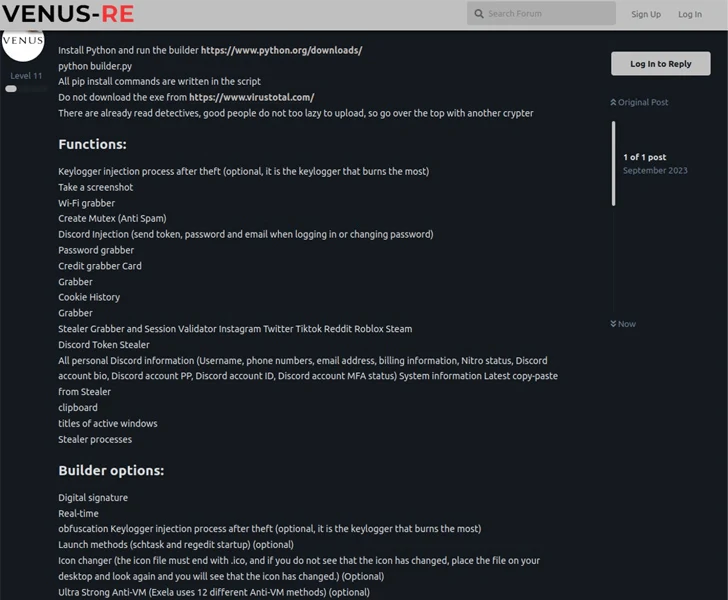
Composed in Python and incorporating guidance for JavaScript, it comes fitted with capabilities to siphon passwords, Discord tokens, credit score cards, cookies and session info, keystrokes, screenshots, and clipboard written content.
ExelaStealer is offered for sale via cybercrime boards as very well as a dedicated Telegram channel established up by its operators who go by the on the internet alias quicaxd. The compensated-for model prices $20 a thirty day period, $45 for a few months, or $120 for a life span license.

The reduced price of the commodity malware makes it a ideal hacking device for newcomers, properly reducing the barrier to entry for pulling off destructive attacks.
The stealer binary, in its latest variety, can only be compiled and packaged on a Windows-centered method using a builder Python script, which throws required supply code obfuscation to the mix in an attempt to resist evaluation.
There is evidence to propose that ExelaStealer is remaining dispersed by using an executable that masquerades as a PDF document, indicating that the initial intrusion vector could be anything at all ranging from phishing to watering holes.
Launching the binary shows a entice document – a Turkish car or truck registration certificate for a Dacia Duster – though stealthily activating the stealer in the history.
“Details has turn out to be a precious forex, and mainly because of this, makes an attempt to gather it will most likely never ever cease,” Slaughter stated.
“Infostealer malware exfiltrates information belonging to businesses and people today that can be applied for blackmail, espionage, or ransom. In spite of the range of infostealers in the wild, ExelaStealer demonstrates there is however room for new gamers to arise and achieve traction.”

The disclosure comes as Kaspersky disclosed information of a campaign that targets govt, law enforcement, and non-revenue corporations to fall numerous scripts and executables at the moment to perform cryptocurrency mining, steal data working with keyloggers, and attain backdoor access to systems.
“The B2B sector continues to be appealing to cybercriminals, who search for to exploit its methods for funds-building needs,” the Russian cybersecurity company claimed, noting that most of the attacks ended up aimed at companies in Russia, Saudi Arabia, Vietnam, Brazil, Romania, the U.S., India, Morocco, and Greece.
Previously this 7 days, U.S. cybersecurity and intelligence organizations released a joint advisory outlining the phishing techniques destructive actors typically use to obtain login credentials and deploy malware, highlighting their tries to impersonate a trustworthy supply to realize their goals.
Identified this posting interesting? Comply with us on Twitter and LinkedIn to read extra special articles we article.
Some parts of this article are sourced from:
thehackernews.com

 OnePlus Open review: A thinner and more affordable flagship foldable
OnePlus Open review: A thinner and more affordable flagship foldable