You can find been a good offer of AI hype recently, but that isn’t going to imply the robots are right here to substitute us. This article sets the history straight and points out how businesses must approach AI.
From musing about self-driving automobiles to fearing AI bots that could damage the earth, there has been a great offer of AI hoopla in the earlier couple of many years. AI has captured our imaginations, goals, and sometimes, our nightmares. On the other hand, the truth is that AI is presently much significantly less innovative than we predicted it would be by now. Autonomous vehicles, for case in point, often regarded as the poster little one of AI’s limitless future, symbolize a narrow use situation and are not but a typical software throughout all transportation sectors.
In this report, we de-buzz AI, deliver instruments for enterprises approaching AI and share info to assistance stakeholders teach themselves.
AI Terminology De-Hyped
AI vs. ML
AI (Synthetic Intelligence) and ML (Equipment Mastering) are terms that are usually used interchangeably, but they symbolize different ideas. AI aims to build intelligence, which signifies cognitive capabilities and the capability to move the Turing test. It is effective by taking what it has acquired and elevating it to the following degree. The goal of employing AI is to replicate human steps, these kinds of as generating a cleaning robot that operates in a manner equivalent to a human cleaner.
ML is a subset of AI. It comprises mathematical types and its capabilities are centered on combining devices with facts. ML performs by understanding lessons from occasions and then prioritizing people lessons. As a outcome, ML can perform steps that humans simply cannot, like likely around broad reams of info, figuring out styles, predicting possibilities, and extra.
Slim vs. Typical AI
The concept of Normal AI is the just one that normally scares most men and women, because it truly is the epitome of our “robotic overlords” replacing human beings. Having said that, although this notion is technically possible, we are not at that stage correct now.
Unlike Typical AI, Slim AI is a specialised sort of AI that is tuned for incredibly precise responsibilities. This aim makes it possible for supporting people, relieving us from function that is far too demanding or likely dangerous. It is not supposed to swap us. Slender AI is now currently being used across industries, like for building autos or packaging boxes. In cybersecurity, Slender AI can examine action facts and logs, browsing for anomalies or symptoms of an attack.
AI and ML in the Wild
There are 3 frequent versions of AI and ML in the wild: generative AI, supervised ML and unsupervised ML.
Generative AI
Generative AI is a cutting-edge industry in AI, characterised by designs, like LLMs, that are skilled on a corpus of know-how. The generative AI technology has the potential to deliver new information based on the info contained inside of that corpus. Generative AI has been explained as a type of “autocorrect” or “form forward,” but on steroids. Examples of Generative AI apps include ChatGPT, Bing, Bard, Dall-E, and specialized cyber assistants, like IBM Security QRadar Advisor with Watson or MSFT Security CoPilot.
Generative AI is most effective suited for use instances like brainstorming, assisted copyediting and conducting research from a dependable corpus. Cybersecurity gurus, like SOC and fusion groups, can leverage Generative AI for study, to enable them fully grasp zero-day vulnerabilities, network topologies, or new indicators of compromise (IoC). It truly is essential to realize that Generative AI in some cases creates “hallucinations”, i.e. wrong answers.
Cyber Security Learn Class: Episode 13Anything You Needed To Know About AI Security But Were being Fearful To Question
In this session, we will go beyond the hype and discover out if and how AI impacts your cybersecurity tactic.
Check out Now
According to Etay Maor, Senior Director Security Approach at Cato Networks, “Generative AI can also assist criminals. For illustration, they can use it to compose phishing email messages. Prior to ChatGPT, just one of the standard detections of phishing email messages was spelling problems and undesirable grammar. All those ended up indicators that some thing was suspicious. Now, criminals can effortlessly compose a phishing email in several languages in fantastic grammar.”
Unsupervised Learning
Unsupervised learning in ML signifies that the instruction details and the results are not labeled. This method will allow algorithms to make inferences from details without human intervention, to come across styles, clusters and connections. Unsupervised understanding is usually employed for dynamic tips, like in retail internet websites.
In cybersecurity, unsupervised understanding can be utilised for clustering or grouping and for obtaining styles that were not clear before, for case in point it can help recognize all malware with a specific signature originating from a specific country-condition. It can also come across associations and back links amongst details sets. For illustration, deciding if people who simply click on phishing email messages are a lot more very likely to reuse passwords. A further use situation is anomaly detection, like detecting exercise that could suggest an attacker is making use of stolen qualifications.
Unsupervised learning is not constantly the ideal choice. When having the output incorrect has a quite large effects and extreme penalties, when short coaching occasions are desired, or when complete transparency is needed, it can be recommended to just take a distinct approach.
Supervised Discovering
In supervised discovering, the coaching information is labeled with enter/output pairs, and the model’s accuracy depends on the high quality of labeling and dataset completeness. Human intervention is frequently required to review the output, increase accuracy,and correct any bias drift. Supervised discovering is most effective suited for building predictions.
In cybersecurity, supervised understanding is applied for classification, which can enable identify phishing and malware. It can also be used for regression, like predicting the expense of a novel attack centered on previous incident expenditures.
Supervised finding out is not the most effective match if you will find no time to coach or no one to label or prepare the info. It is also not advised when there is a have to have to analyze massive quantities of info, when there is not plenty of knowledge, or when automated classification/clustering is the close intention.
Reinforcement Discovering (RL)
Reinforcement Learning (RL) occupies a room involving absolutely supervised and unsupervised finding out and is a special method to ML. It signifies retraining a product when present schooling fails to foresee certain use cases. Even deep understanding, with its obtain to substantial datasets, can continue to pass up outlier use cases that RL can address. The pretty existence of RL is an implicit admission that products can be flawed.
What Cybercriminals are Saying About Generative AI
Generative AI is of desire to cyber criminals. In accordance to Etay Maor “Cyber criminals have been conversing about how to use ChatGPT, Bard and other GenAI applications from the day they had been released, as very well as sharing their encounter and feelings about their capabilities. As it would seem, they consider that GenAI has restrictions and will likely be much more mature for attacker use in a few years.”
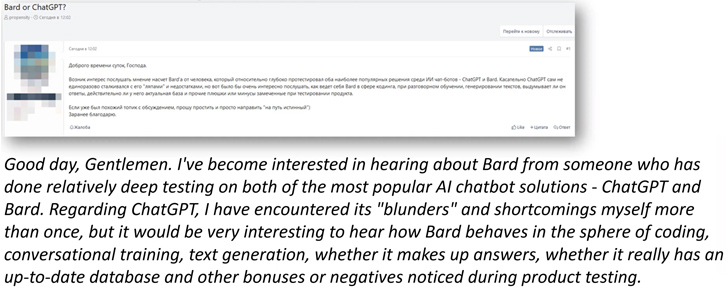
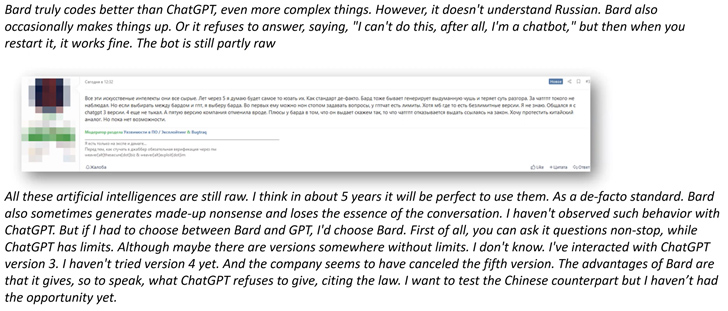
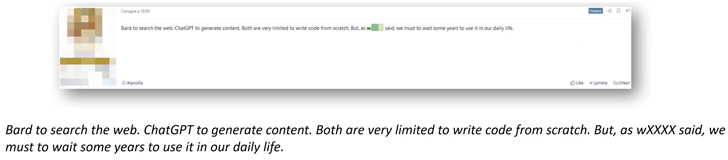
Some discussion illustrations incorporate:
The Artificial Intelligence Risk Administration Framework (AI RMF) by NIST
When engaging with AI and AI-centered alternatives, it really is critical to comprehend AI’s restrictions, pitfalls and vulnerabilities. The Synthetic Intelligence Risk Management Framework (AI RMF) by NIST is a established of pointers and most effective methods made to support businesses establish, evaluate and handle the challenges associated with the deployment and use of artificial intelligence technologies.
The framework is made up of 6 aspects:
Extra resources for managing AI risk involve the MITRE ATLAS (Adversarial Menace Landscape for Artificial-Intelligence Techniques), OWASP Prime 10 for ML and Google’s Protected AI Framework (SAIF).
Queries to Question Your Vendor
In the around potential, it will be really popular for distributors to offer you generative AI abilities. Right here is a listing of concerns to question to support your educated preference.
1. What and Why?
What are the AI capabilities and why are they essential? For example, GenAI is really very good at producing e-mails, so GenAI makes feeling for an email process. What is actually the use situation for the vendor?
2. Teaching knowledge
Teaching facts wants to be properly and accurately managed, otherwise it can generate bias. It can be vital to talk to about the styles of coaching information, how it has been cleaned, how it is managed, and so on.
3. Was resilience developed-in?
Has the vendor taken into consideration that cybercriminals are attacking the program alone and executed security controls?
4. Real ROI vs. Promises
What is the ROI and does the ROI justify utilizing AI or ML (or ended up they added due to the fact of the buzz and for product sales applications)?
5. Is it Genuinely Solving a Problem?
The most vital query – is the AI solving your difficulty and is it performing it well? There’s no place in paying out a high quality and incurring further overhead unless the AI is solving the challenge and working the way it really should.
AI can empower us and assist us perform superior, but it is not a silver bullet. That’s why it can be crucial for companies to make educated choices about equipment with AI they decide on to carry out internally.
To master much more about AI and ML use situations, pitfalls, apps, vulnerabilities and implications for security industry experts, look at the whole masterclass in this article.
Observed this post attention-grabbing? Adhere to us on Twitter and LinkedIn to study a lot more exclusive content we article.
Some parts of this article are sourced from:
thehackernews.com


 Vietnamese Cybercriminals Targeting Facebook Business Accounts with Malvertising
Vietnamese Cybercriminals Targeting Facebook Business Accounts with Malvertising