A malware botnet identified as Ebury is estimated to have compromised 400,000 Linux servers given that 2009, out of which much more than 100,000 have been however compromised as of late 2023.
The results appear from Slovak cybersecurity organization ESET, which characterized it as just one of the most advanced server-facet malware strategies for money attain.
“Ebury actors have been pursuing monetization functions […], including the unfold of spam, web site visitors redirections, and credential thieving,” security researcher Marc-Etienne M.Léveillé reported in a deep dive investigation.
“[The] operators are also associated in cryptocurrency heists by making use of AitM and credit card stealing by means of network website traffic eavesdropping, frequently identified as server-side web skimming.”
Ebury was to start with documented over a 10 years back as component of a campaign codenamed Operation Windigo that qualified Linux servers to deploy the malware, alongside other backdoors and scripts like Cdorked and Calfbot to redirect web visitors and send out spam, respectively.

Subsequently, in August 2017, a Russian countrywide named Maxim Senakh was sentenced to almost 4 a long time in jail in the U.S. for his function in the enhancement and maintenance of the botnet malware.
“Senakh and his co-conspirators applied the Ebury botnet to create and redirect internet traffic in furtherance of a variety of click on-fraud and spam email techniques, which fraudulently created tens of millions of bucks in profits,” the U.S. Justice Division said at the time.
“As aspect of his plea, Senakh admitted that he supported the felony enterprise by building accounts with area registrars that helped develop the Ebury botnet infrastructure and personally profited from site visitors produced by the Ebury botnet.”
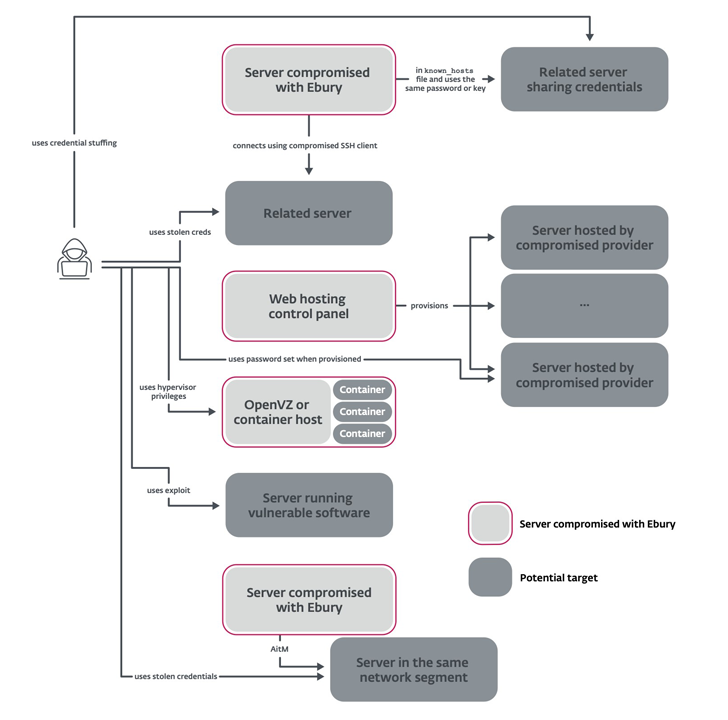
ESET’s investigation has unearthed different methods the attackers use to provide Ebury, such as procedures these kinds of as theft of SSH credentials, credential stuffing, infiltrating hosting service provider infrastructure, exploitation of flaws in Handle Web Panel (e.g., CVE-2021-45467), and SSH adversary-in-the-middle (AitM) assaults.
The threat actors have also been noticed applying pretend or stolen identities to include their tracks, not to mention compromising infrastructure used by other perpetrators with the malware in get to meet up with their objectives and confuse attribution attempts.
“An instance is the compromise of servers accountable for gathering info from Vidar Stealer,” ESET mentioned. “Ebury actors utilised the stolen identities attained through Vidar Stealer for renting server infrastructure and in their functions, sending law enforcement bodies in the erroneous instructions.”
In another occasion, Ebury is reported to have been utilized to breach just one of the Mirai botnet author’s devices and steal the code substantially ahead of it was built public.
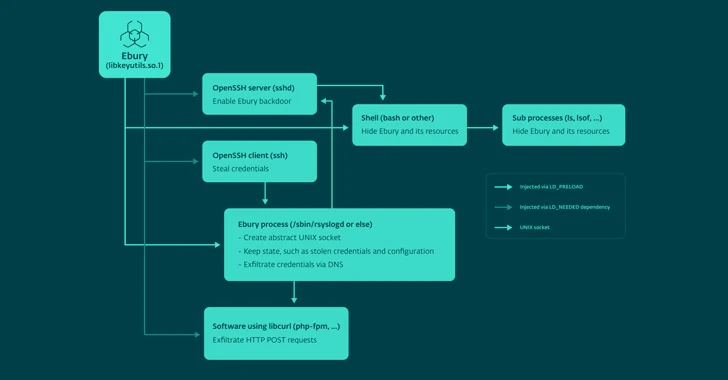
The malware also acts as a backdoor and SSH credential stealer, offering attackers the capacity to deploy more payloads like HelimodSteal, HelimodProxy, and HelimodRedirect, and extend their existence inside a compromised network. The most current variation of Ebury recognised to day is 1.8.2.

“All those resources have the widespread aim of monetizing, by way of several techniques, the servers they compromise,” ESET claimed. “The way servers are monetized array from credit history card information and facts theft and cryptocurrency stealing to site visitors redirection, spam sending, and credential stealing.”
Though HelimodSteal, HelimodRedirect, and HelimodProxy are all HTTP server modules applied for intercepting HTTP Write-up requests produced to the web server, redirect HTTP requests to ads, and proxy traffic to send out spam, the team also employs a kernel module known as KernelRedirect that implements a Netfilter hook to modify HTTP website traffic to execute redirection.
Also used are software program to hide and permit destructive visitors by means of the firewall, as perfectly as Perl scripts to have out massive-scale AitM attacks inside of hosting providers’ info facilities to breach worthwhile targets and steal cryptocurrency from their wallets.
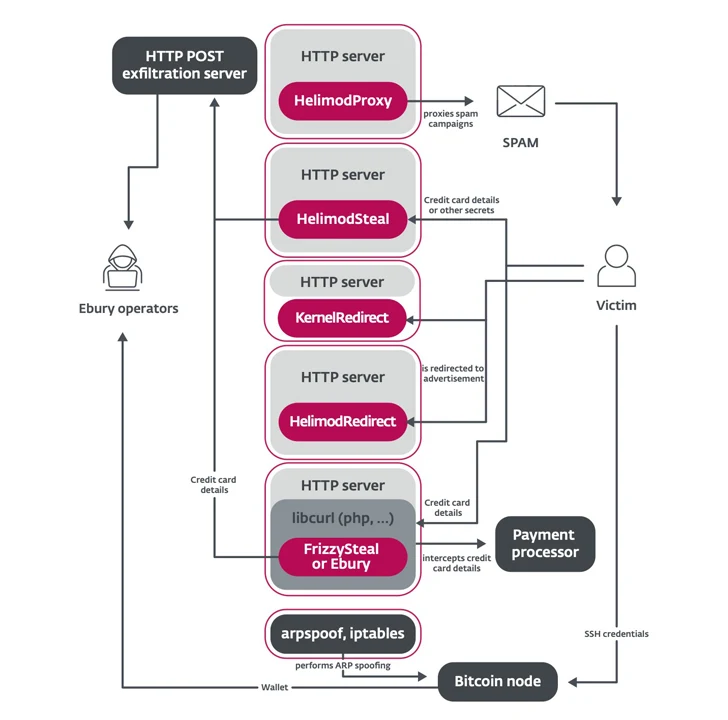
HelimodSteal is also created to seize credit card details that is submitted by a victim to an on the web keep, correctly as a server-side web skimmer to extract the info gained by the contaminated server.
In an alternate chain of gatherings, the fiscal information can be attained by implies of Ebury or FrizzySteal, a destructive shared library that’s injected into libcurl and can exfiltrate requests manufactured by the compromised server to external HTTP servers, these types of as a payment processor.
“Because the two are operating inside of the web server or application, conclude-to-conclude encryption (HTTPS) are not able to guard against this threat,” ESET noted.
“Access to servers made use of for shared hosting grants them accessibility to a good deal of unencrypted web site visitors, which they leverage for stealthy redirection or capturing facts submitted in online types.”
Uncovered this posting fascinating? Abide by us on Twitter and LinkedIn to read through more unique content material we post.
Some parts of this article are sourced from:
thehackernews.com

 It’s Time to Master the Lift & Shift: Migrating from VMware vSphere to Microsoft Azure
It’s Time to Master the Lift & Shift: Migrating from VMware vSphere to Microsoft Azure