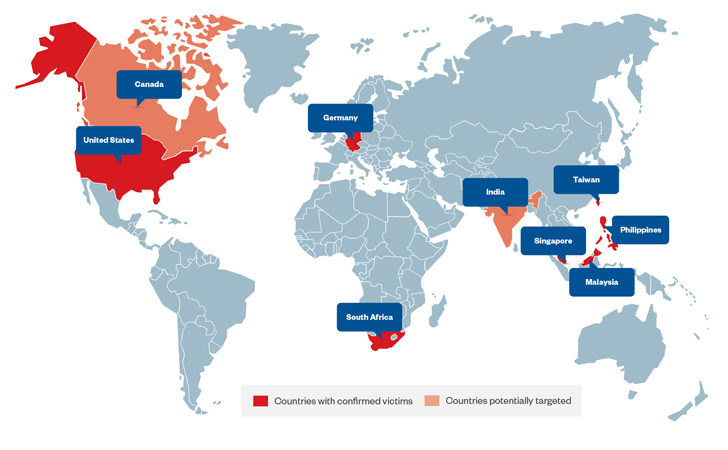
A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage campaign targeting federal government and technology industries based in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the U.S.
“The danger actors powering Earth Estries are functioning with higher-degree assets and working with refined capabilities and encounter in cyber espionage and illicit pursuits,” Trend Micro researchers Ted Lee, Lenart Bermejo, Hara Hiroaki, Leon M Chang, and Gilbert Sison reported.
Active due to the fact at least 2020, Earth Estries is reported to share tactical overlaps with one more country-point out group tracked as FamousSparrow, which was to start with exposed by ESET in 2021 as exploiting ProxyLogon flaws in Microsoft Exchange Server to penetrate hospitality, governing administration, engineering, and authorized sectors.

It’s well worth pointing out that commonalities have also been unearthed involving FamousSparrow and UNC4841, a categorized action cluster held responsible for the weaponization of a just lately disclosed zero-day flaw in Barracuda Networks Email Security Gateway (ESG) appliances.
Attack chains documented by Trend Micro present that the adversary is leveraging Cobalt Strike to carry out publish-exploitation of compromised environments, pursuing which it moves speedily to deploy additional malware and broaden the foothold.
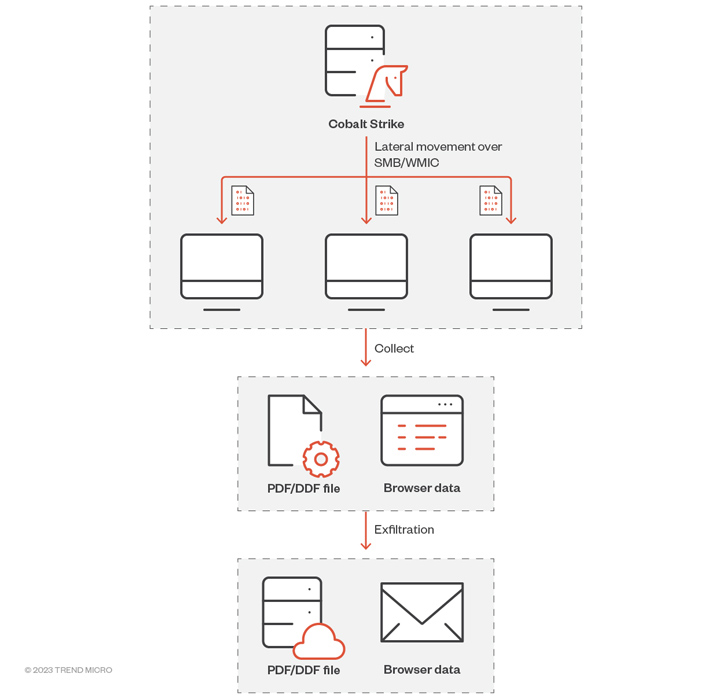
The adversary has been observed utilizing an arsenal of backdoors and hacking tools, which includes backdoors, browser info stealers, and port scanners to boost info selection.
This encompasses Zingdoor, a Go-based mostly implant to capture process information, enumerate and regulate documents, and operate arbitrary commands TrillClient, a custom made stealer prepared in Go to siphon details from web browsers and HemiGate, a backdoor that can log keystrokes, acquire screenshots, carry out file operations, and check procedures.

Further more lending legitimacy to the adversary’s espionage motives is its proclivity in the direction of frequently cleansing and redeploying its backdoors on the contaminated host in an attempt to minimize the risk of publicity and detection.
“Earth Estries depends closely on DLL facet-loading to load different instruments within just its arsenal,” the scientists said. “To go away as small footprint as achievable, they use PowerShell downgrade attacks to keep away from detection from Windows Antimalware Scan Interface’s (AMSI) logging system.”
One more major element of the modus operandi is the abuse of community products and services such as Github, Gmail, AnonFiles, and File.io to exchange or transfer instructions and stolen data. A the vast majority of the command-and-command (C2) servers are found in the U.S., India, Australia, Canada, China, Japan, Finland, South Africa, and the U.K.
“By compromising internal servers and valid accounts, the threat actors can accomplish lateral movement inside the victim’s network and carry out their malicious pursuits covertly,” the researchers reported. “They also use tactics like PowerShell downgrade assaults and novel DLL facet-loading combinations to evade detection.”
Observed this short article appealing? Stick to us on Twitter and LinkedIn to study additional special content we post.
Some parts of this article are sourced from:
thehackernews.com

 Hackers Can Exploit Windows Container Isolation Framework to Bypass Endpoint Security
Hackers Can Exploit Windows Container Isolation Framework to Bypass Endpoint Security