In what is the latest evolution of risk actors abusing legit infrastructure for nefarious ends, new findings clearly show that nation-condition hacking teams have entered the fray in leveraging the social system for focusing on critical infrastructure.
Discord, in the latest a long time, has come to be a rewarding concentrate on, performing as a fertile ground for hosting malware utilizing its written content supply network (CDN) as perfectly as permitting details stealers to siphon delicate data off the application and facilitating facts exfiltration by usually means of webhooks.
“The utilization of Discord is mainly limited to information and facts stealers and grabbers that anyone can purchase or down load from the Internet,” Trellix researchers Ernesto Fernández Provecho and David Pastor Sanz stated in a Monday report.

But that may perhaps be switching, for the cybersecurity agency reported it uncovered evidence of an artifact focusing on Ukrainian critical infrastructures. There is currently no evidence linking it to a known risk group.
“”The likely emergence of APT malware campaigns exploiting Discord’s functionalities introduces a new layer of complexity to the danger landscape,” the researchers noted.
The sample is a Microsoft OneNote file distributed by using an email concept impersonating the non-income dobro.ua.
The file, at the time opened, is made up of references to Ukrainian soldiers to trick recipients into donating by clicking on a booby-trapped button, ensuing in the execution of Visible Fundamental Script (VBS) designed to extract and run a PowerShell script in order to down load yet another PowerShell script from a GitHub repository.
For its section, in the closing phase, PowerShell can take benefit of a Discord webhook to exfiltrate procedure metadata.
“The actuality that the only aim of the last payload is acquiring information and facts about the technique suggests that the campaign is nonetheless in an early stage, which also matches with the utilization of Discord as [command-and-control],” the scientists said.
“Having said that, it is critical to spotlight that the actor could supply a additional subtle piece of malware to the compromised units in the future by modifying the file stored in the GitHub repository.”

Trellix’s analysis even more uncovered that loaders these as SmokeLoader, PrivateLoader, and GuLoader are amid the most prevalent malware households that use Discord’s CDN to obtain a future-stage payload, together with stealers like RedLine, Vidar, Agent Tesla, and Umbral.
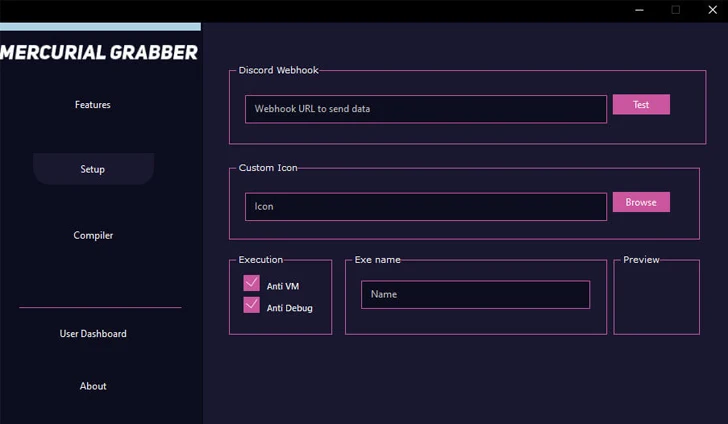
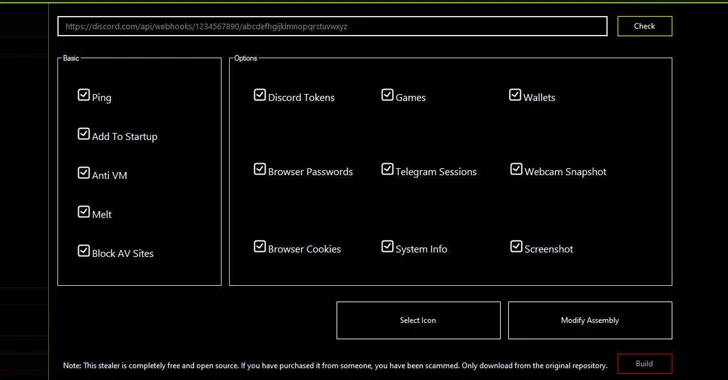
On prime of that, some of the prevalent malware families that have been noticed applying Discord webhooks are Mercurial Grabber, Stealerium, Typhon Stealer, and Venom RAT.
“The abuse of Discord’s CDN as a distribution mechanism for additional malware payloads showcases the adaptability of cybercriminals to exploit collaborative applications for their achieve,” the researchers said.
“APTs are known for their advanced and specific assaults, and by infiltrating widely applied communication platforms like Discord, they can proficiently set up extended-phrase footholds within networks, putting critical infrastructure and delicate information at risk.”
Identified this report fascinating? Abide by us on Twitter and LinkedIn to study extra exclusive content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Critical Vulnerabilities Uncovered in Open Source CasaOS Cloud Software
Critical Vulnerabilities Uncovered in Open Source CasaOS Cloud Software