Introduction
The notorious Colonial pipeline ransomware attack (2021) and SolarWinds supply chain attack (2020) were additional than data leaks they were seismic shifts in cybersecurity. These assaults uncovered a critical problem for Main Data Security Officers (CISOs): keeping their floor even though preserving handle around cloud security in the accelerating entire world of DevOps. The trouble was emphasised by the Funds A person data breach (2019), Epsilon knowledge breach (2019), Magecart compromises (ongoing), and MongoDB breaches (2023-), the place hackers exploited a misconfigured AWS S3 bucket. Robust collaboration between CISOs and DevOps teams on right cloud security configurations could have prevented the breaches.
Additional than the fight in opposition to hackers and the consequences of their attacks, various crucial complications stand out —the evolution of CISO’s position and duties and the challenge of bettering cloud security, and how security operations teams collaborate with business models in the frenzy of digital transformation.
Observing SecOps vs. DevOps conflicts within companies of distinctive kinds, we’ll attempt to navigate a advanced landscape of cybersecurity leadership, notably their dynamic connection with the Main Technology Officer (CTO). As the job of CISO becomes more essential than at any time, we will concentrate on further empowering CISOs to come to be influential voices in conclusion-generating, making certain security is getting its rightful area in DevOps procedures.
We will also propose some techniques for CISOs to converse with IT leadership, in purchase to teach and maximize consciousness of pressing security issues. Ultimately, only robust partnerships between CISOs, DevOps groups, and IT administration can enhance enhancement processes that gas innovation without the need of compromising security.
The stakes for a CISO are greater than at any time
Visualize a race car or truck rushing down the progress keep track of. The CTO, at the wheel, pushes for breakneck innovation. But in the backseat, the CISO sweats, gripping the metaphorical handbrake of security. This is the at any time-present problem for CISOs in the age of DevOps: preserving command about security in a lightning-fast enhancement ecosystem.
We can concur that previously, security typically arrived as an afterthought, bolted onto applications extensive soon after they were created. DevOps, whilst selling agility, can introduce vulnerabilities if security is not taken treatment of from the begin. Effective development teams targeted on pace could unintentionally introduce security gaps. Legacy security approaches, reliant on guide processes and restricted sources, only won’t be able to preserve up with the breakneck rate of DevOps.
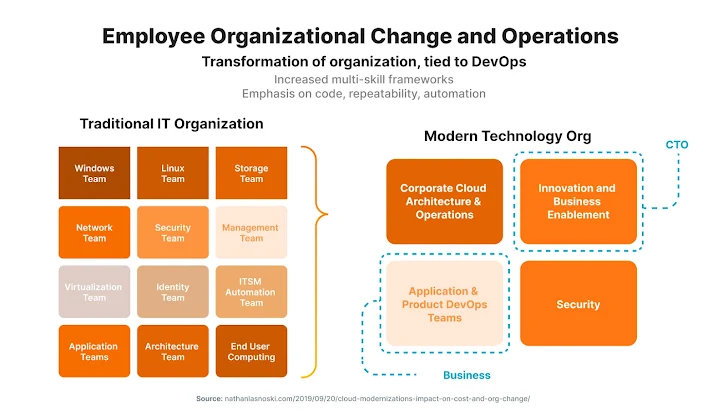
One particular view of the modern day look at of IT management destinations the CTO at the forefront of tech-linked company fears, which includes transferring all the infrastructure to the cloud, though the CISO focuses on security, and securing the cloud becomes a person of the top rated priorities. The tempo of modify and the entirely new architecture, in the case of the cloud, existing new issues for CISOs who encounter a frequently changing setting. It really is significant to adapt their communication style to properly collaborate with CTOs who are increasingly concentrated on bringing innovations and driving organization expansion.
Authentic-environment consequences for CISO
The Securities and Trade Commission (SEC) filing alleges that SolarWinds unsuccessful to disclose ample materials details to traders relating to cybersecurity threats. The filing states that the firm and its CISO Timothy Brown only disclosed generic and hypothetical threats irrespective of internal know-how of certain deficiencies in SolarWinds’ cybersecurity techniques and a heightened danger likelihood.
The most notorious conditions that every person really should be conscious of, SolarWinds and Uber breaches, were not just information breaches. They were wake-up calls. Legal repercussions for security failures are a expanding issue, with the SEC mandating community companies to disclose incidents within just 4 days and demanding detailed security plans. This places enormous strain on CISOs like Joe Sullivan (Uber’s former Chief Security Officer) and Timothy G. Brown (SolarWinds’ former CISO), who could confront felony fees for failing to implement sufficient safeguards.

These incidents underscore the delicate balancing act that CISOs facial area in the age of DevOps. DevOps methodologies prioritize pace and agility, which can be at odds with the need for arduous security procedures. Can CISOs navigate this tightrope far more properly whilst nevertheless ensuring innovation will not come at the price of security?
CISO wants to bridge the hole
In the early times of DevOps, CISOs frequently felt like passengers with no seatbelts in a new, rapid-paced globe, where speed reigned supreme and security lagged powering. Marketing security procedures devoid of impacting growth velocity can be hard. The CISO’s affect empowers them to collaborate successfully with DevOps teams and guarantee security is not an afterthought.
In this article are the prime activities that a CISO can engage in to bridge the gap:

Carried out regularly, these things to do will reveal how security can proactively decrease risk, making the reliability of the CISO and the group he engages to establish a bridge amongst security and growth. These pursuits travel collaboration and data sharing so that as teams operate alongside one another, they will begin to share duty for keeping matters protected. So, rather of experience like a passenger, the CISO will become a proactive companion, ensuring security is considered from the beginning, enabling innovation to thrive on a secure foundation within the IT office.
How a CISO can amplify their voice in the DevOps сonversation
When CISOs won’t be able to amplify their voice, the implications can be dire. Inadequate security tactics expose the organization to authorized and regulatory hazards. Far more importantly, they leave the door open up for highly-priced breaches, as occurred with SolarWinds, that stifle innovation and erode purchaser trust.
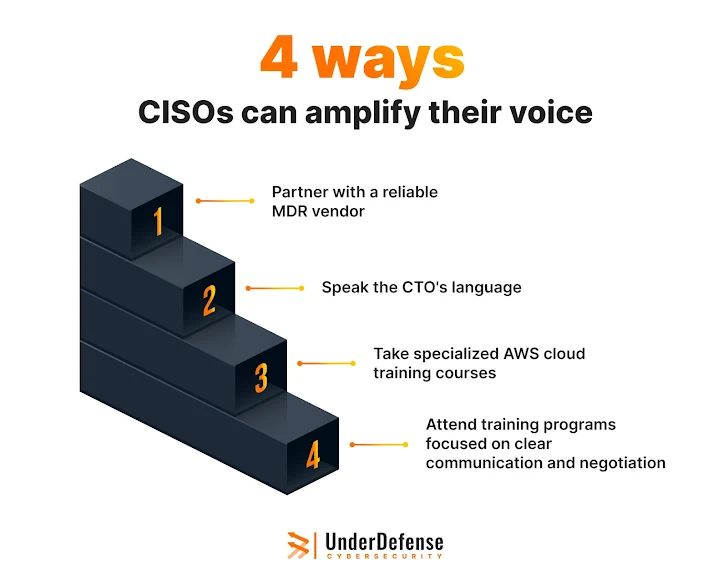
Here is how MDR empowers CISOs to affect protected enhancement:
- 24/7 View Compliance and Proactive Menace Detection: MDR companies give continual checking and innovative risk intelligence, letting CISOs to proactively handle security problems prior to they develop into troubles. This frees security groups to concentrate on strategic initiatives and fosters a collaborative environment exactly where security is preventative, not reactive.
- Early Warning System for Security Gaps: MDR goes beyond classic monitoring by detecting anomalies in entry designs, person actions, and procedure configurations. This makes it possible for for determining potential insider threats or misconfigurations launched by DevOps groups. By providing serious-time alerts of opportunity security challenges, CISOs can do the job with improvement groups to tackle them before they develop into exploitable vulnerabilities.
Assessments, tabletop routines, and the ability to deliver in outside gurus, these as an MDR group, will emphasize any conversation gaps within the corporation. Choosing what desires to be communicated and escalated to whom is incredibly critical to use sources efficiently and increase visibility to essential security considerations. Pinpointing the crucial classes of concern and who requirements to be informed and involved is essential to thriving security operations and a thriving enterprise. Reviewing and formalizing communications can preserve time during an crisis such as a breach.

The RACI matrix is just one particular instance, highlighting the great importance of establishing apparent interaction styles inside DevOps. By utilizing these types of designs and integrating them into security policies, CISOs can achieve major leverage, ensuring security is woven into the material of DevOps, not bolted on as an afterthought.
Ultimately, the matrix emphasizes a critical part of a CISO’s position: setting up strong assistance by the Board. This alignment is critical for developing security as a strategic priority and securing the resources wanted for a strong security posture.
A Robust security team is even now essential
The speedy pace of DevOps can go away even the most expert CISOs battling to retain tempo with threats. MDR empowers CISOs to changeover from reactive firefighting to proactive risk looking. Instead of patching vulnerabilities following a breach, MDR allows recognize and remediate them right before they can be exploited. This proactive strategy minimizes security threats and fosters a culture of “security by layout” in just the DevOps pipeline.
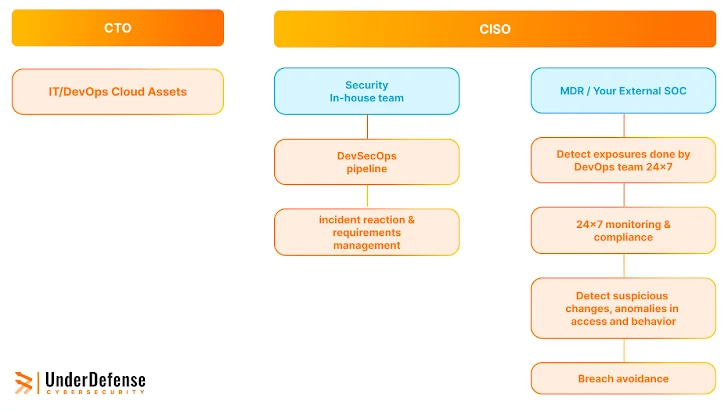
Though MDR provides sizeable price, it will not switch a solid internal security staff. Security specialists keep on being essential for:
- Maintaining Situational Recognition: The security staff interprets knowledge and alerts produced by MDR, furnishing context and prioritizing threats.
- Responding to Incidents: Security staff with deep incident reaction know-how are essential for correctly containing and remediating security breaches.
- Handling Security Needs: The security group makes sure that security demands are integrated into the DevSecOps pipeline, fostering a society of “security by layout.”
We’ve also ready the most in depth MDR Buyer’s Information by UnderDefense for your attention, which equips you to pick out the great MDR lover, safeguarding your knowledge and company functions. It presents seller-agnostic expert insights to support you make knowledgeable choices.
The primary takeaway: collaboration is a essential
When the CISO’s influence engine equips them with effective equipment, security continues to be a collaborative energy. Creating bridges with the CTO and fostering open up interaction with improvement teams are the cornerstones of a truly protected DevOps environment. By wielding their influence correctly and collaborating throughout departments, CISOs can assure security gets an integral component of the DevOps procedure, enabling innovation to prosper devoid of sacrificing basic safety on the security highway.
The breakneck pace of DevOps can make a security problem – a pace bump on the security highway. Below, the CISO plays a critical job as an architect, not an enforcer. Their increasing influence engine equips them with the instruments to navigate this complex landscape. Security assessments, pink teaming exercise routines, and collaboration with security consultants empower CISOs to advocate for sturdy security actions with no hindering innovation.
Nonetheless, the real recreation-changer in this situation is MDR. It acts as a force multiplier for the CISO inside the DevOps discussion. By supplying 24/7 monitoring, proactive danger detection, and early warnings of security gaps, MDR empowers CISOs to shift from reactive firefighting to proactive threat looking. This not only safeguards the corporation but also fosters a lifestyle of “security by layout” inside of the DevOps pipeline.
In essence, the alternative to the DevOps predicament lies in a strong blend: the evolving function of the CISO, wielding an expanded affect engine, and the drive-multiplying capabilities of MDR. UnderDefense provides a chopping-edge MDR answer that gives real-time visibility into your security posture, equipping you to proactively detect and respond to security incidents and finally safeguarding your business.
By embracing collaboration and leveraging these applications, CISOs can make sure security seamlessly integrates with DevOps, enabling innovation to speed down the freeway without the need of encountering security roadblocks.

Identified this write-up exciting? This report is a contributed piece from 1 of our valued companions. Follow us on Twitter and LinkedIn to read through far more special written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Google Detects 4th Chrome Zero-Day in May Actively Under Attack – Update ASAP
Google Detects 4th Chrome Zero-Day in May Actively Under Attack – Update ASAP