Just one of the most popular misconceptions in file upload cybersecurity is that selected tools are “sufficient” on their own—this is just not the case. In our most current whitepaper OPSWAT CEO and Founder, Benny Czarny, requires a complete glimpse at what it can take to protect against malware threats in modern at any time-evolving file upload security landscape, and a huge portion of that is understanding in which the pitfalls are, and how to prevent them.
The first action in that method is comprehension that three normally utilised resources or solutions are not plenty of on their individual. Let’s examine this concept and just take a nearer appear at a superior resolution.
Knowledge the Obstacle
Contemporary web programs are intricate, making use of internet-connected IT techniques that interface with critical OT units, as well as leveraging a large array of cloud providers and protocols. All these systems transfer and retail store extremely sensitive and valuable knowledge throughout govt, health care, electric power, economic, and other critical sectors the planet more than, carrying with them threats able of causing critical destruction.
Securing file uploads to detect and avert malware infiltration is critical. As this threat vector grows and the attack area spreads, making certain that these sectors continue to be safe will become of the utmost significance. This is why building—and enforcing—a responsible and tested security tactic is paramount transferring forward.
Applications of the Trade
A single instrument on its individual is only not sufficient. Right here are a few usually employed instruments that, when employed on their own to secure file uploads, do not supply sufficient protection and why that is the case:
1. Anti-Malware File Scanning
Everybody is acquainted with anti-malware, but not all anti-malware engines—or scanning modes—are designed equal. It’s intriguing that there is nonetheless so much confusion in excess of the efficacy prices when it comes to the “generally-on” real-time protection that is checking an entire process versus, say, static file scanning methods that require to be operate manually or scheduled. Genuine-time scanning can show just about 100% efficacy rates, though in distinction, static scanning is significantly reduce with fees that array in between 6-76%. To stay clear of a bogus feeling of security, corporations ought to know particularly what they are finding with each deployment manner.
2. Web Application Firewalls
Quite a few authorities believe that by installing a web application firewall (WAF) they are secured towards malicious file uploads. The actuality is that it is quite significantly not the case, as web application firewalls principally safeguard versus attacks at the application layer (OSI Layer 7). They do not have a unique structure to avoid malware infections that might goal other layers or unfold by way of distinctive channels, these types of as email attachments or detachable media. Also, they battle with encrypted traffic (like https) and typically depend on a solitary anti-malware alternative for threat detection.
3. Sandboxing
Sandboxing is a technique that was initially made use of to analyze malware by isolating and executing suspicious information in a managed ecosystem to understand their behavior and detect opportunity signals of malware. By yourself, sandboxes deal with constraints these types of as weakness to advanced and time-based mostly evasion strategies that obfuscate or delay malicious functions and ecosystem-unique triggers in adaptive malware. They are source-intense, prone to phony positives and negatives, and supply limited coverage distinct to file-based malware.
Defense-in-Depth Cybersecurity
So, if you won’t be able to depend on these strategies on your own, what is the solution? This is a person of the areas OPSWAT has put in the past 20 several years innovating in. Our MetaDefender System layers in sector-primary and globally trusted systems to type an uncomplicated to deploy, integrated-by-structure, protection-in-depth cybersecurity technique for securing file uploads.
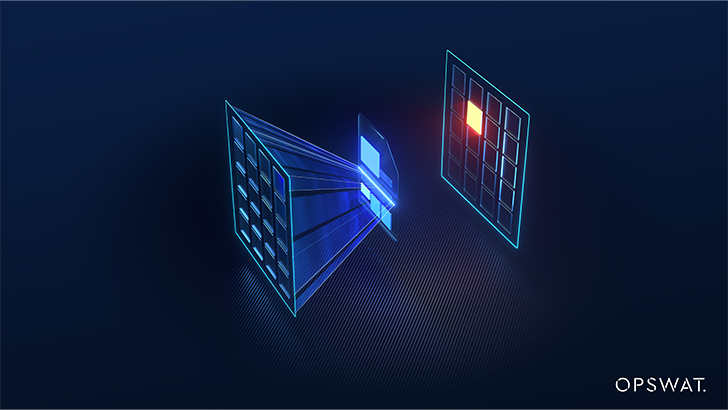 Multiscanning: Make use of above 30 of the world’s greatest antivirus engines to detect approximately 100% of threats
Multiscanning: Make use of above 30 of the world’s greatest antivirus engines to detect approximately 100% of threats
Multiscanning
As the usefulness of solitary anti-malware answers for static assessment differs any place from 6% to 76%, we made a decision to combine numerous commercially available kinds into our solution and advantage from their blended electrical power. With more than 30 main anti-malware engines operating at the same time, our efficacy charges are just shy of 100% when getting optimized for velocity.
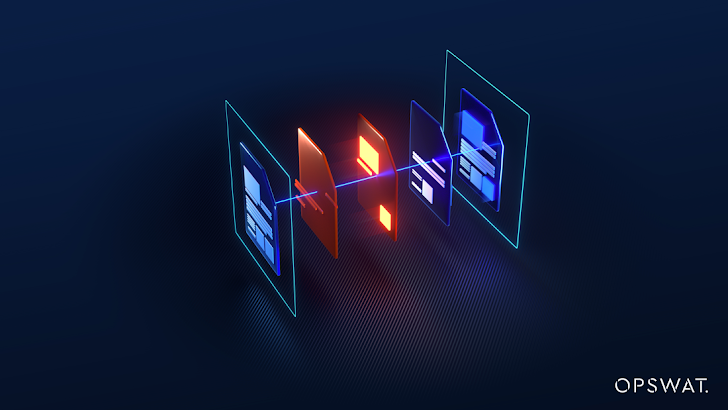 Deep Content material Disarm and Reconstruction: Sanitize, block, and take away file objects and regenerate a risk-free copy
Deep Content material Disarm and Reconstruction: Sanitize, block, and take away file objects and regenerate a risk-free copy
Deep Information Disarm and Reconstruction (Deep CDR)
To further more bolster our defenses, we pioneered a exclusive methodology, referred to as Deep Content Disarm and Reconstruction (Deep CDR). Awarded a AAA, 100% Security rating from SE Labs, our special technology delivers thorough prevention-centered security for file uploads by neutralizing possible threats right before they can cause harm. It evaluates and verifies the file type and regularity and validates file extensions to avert masquerading and alerts businesses if they are beneath attack. Then it separates data files into discrete parts and removes potentially hazardous objects and rebuilds usable information, reconstructing metadata, preserving all file features.
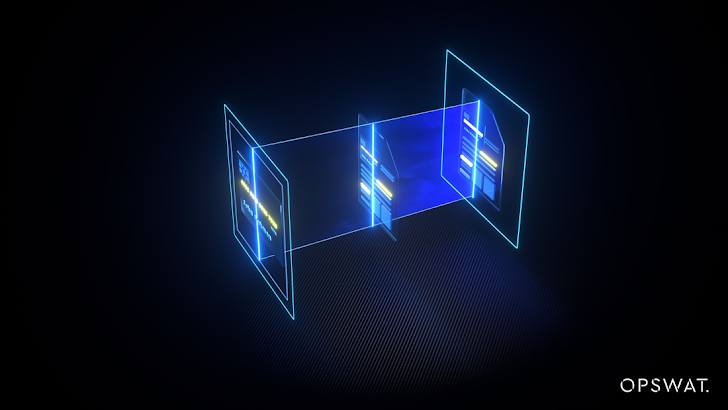 Proactive Information Decline Prevention: Lower warn fatigue by redacting delicate facts
Proactive Information Decline Prevention: Lower warn fatigue by redacting delicate facts
Proactive Info Loss Avoidance (Proactive DLP)
OPSWAT’s Proactive Knowledge Loss Avoidance (DLP) module was produced exclusively to deal with the expanding problems of compliance and regulation, details leakage and pitfalls associated with file uploads. Our solution detects and guards delicate information and facts inside of a variety of file forms, such as textual content, picture, and online video-based mostly patterns.
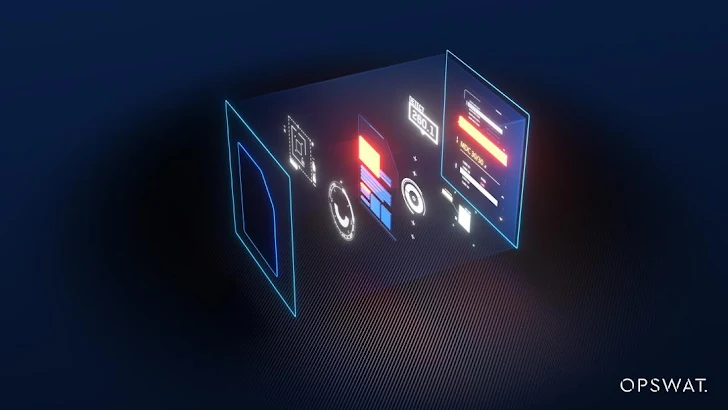 Adaptive Sandbox: Adaptive threat examination technology permits zero-day malware detection and extracts additional indicators of compromise.
Adaptive Sandbox: Adaptive threat examination technology permits zero-day malware detection and extracts additional indicators of compromise.
True-Time Adaptive Sandbox
To overcome the restrictions of traditional sandboxing, OPSWAT formulated a one of a kind emulation-centered sandbox with adaptive menace investigation. By pairing it with our Multiscanning and Deep CDR technologies it supplies a detailed multi-layered method to malware detection and prevention. Our emulation-centered solution can swiftly de-obfuscate and dissect even the most complex, condition-of-the-artwork, and atmosphere-conscious malware in below 15 seconds.
What is actually Upcoming?
These are only some of the technologies that electrical power the MetaDefender Platform. Like the modules detailed in this article, there are much more that are goal-created to satisfy the diverse use-conditions and wants of critical infrastructure defense. Like the threat landscape all over us, we are driving innovation forward to move up and continue to be ahead of the most up-to-date threats.
We encourage you to study the complete whitepaper listed here, and when you happen to be prepared to find why OPSWAT is the critical benefit in file add cybersecurity, converse to one particular of our authorities for a free of charge demo.
Identified this posting interesting? This article is a contributed piece from 1 of our valued associates. Adhere to us on Twitter and LinkedIn to read through additional distinctive information we publish.
Some parts of this article are sourced from:
thehackernews.com


 PixPirate Android Banking Trojan Using New Evasion Tactic to Target Brazilian Users
PixPirate Android Banking Trojan Using New Evasion Tactic to Target Brazilian Users