An investigation of firmware visuals throughout units from Dell, HP, and Lenovo has discovered the existence of out-of-date versions of the OpenSSL cryptographic library, underscoring a provide chain risk.
EFI Enhancement Package, aka EDK, is an open up source implementation of the Unified Extensible Firmware Interface (UEFI), which functions as an interface amongst the functioning technique and the firmware embedded in the device’s hardware.
The firmware growth surroundings, which is in its 2nd iteration (EDK II), will come with its possess cryptographic package deal named CryptoPkg that, in flip, helps make use of products and services from the OpenSSL undertaking.
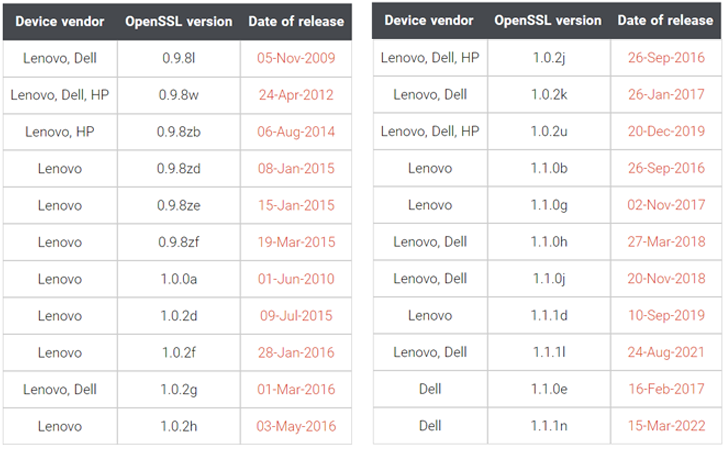
Per firmware security firm Binarly, the firmware image linked with Lenovo Thinkpad business gadgets was identified to use three distinct variations of OpenSSL: .9.8zb, 1..0a, and 1..2j, the past of which was launched in 2018.
What is actually a lot more, one of the firmware modules named InfineonTpmUpdateDxe relied on OpenSSL variation .9.8zb that was shipped on August 4, 2014.
“The InfineonTpmUpdateDxe module is liable for updating the firmware of Dependable Platform Module (TPM) on the Infineon chip,” Binarly defined in a technological compose-up very last 7 days.
“This plainly suggests the supply chain problem with 3rd-celebration dependencies when it looks like these dependencies under no circumstances obtained an update, even for critical security issues.”
The variety of OpenSSL variations apart, some of the firmware offers from Lenovo and Dell used an even older variation (.9.8l), which came out on November 5, 2009. HP’s firmware code, likewise, utilized a 10-yr-outdated version of the library (.9.8w).
The point that the system firmware takes advantage of many variations of OpenSSL in the similar binary bundle highlights how 3rd-get together code dependencies can introduce far more complexities in the source chain ecosystem.
Binarly further pointed out the weaknesses in what is actually called a Application Bill of Materials (SBOM) that arises as a result of integrating compiled binary modules (aka shut supply) in the firmware.
“We see an urgent require for an further layer of SBOM Validation when it will come to compiled code to validate on the binary amount, the list of 3rd-celebration dependency information that matches the true SBOM provided by the vendor,” the firm explained.
“A ‘trust-but-verify’ approach is the finest way to deal with SBOM failures and minimize offer chain dangers.”
Located this posting fascinating? Comply with THN on Facebook, Twitter and LinkedIn to examine far more distinctive written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Global Police Celebrate $130m Cyber Busts
Global Police Celebrate $130m Cyber Busts