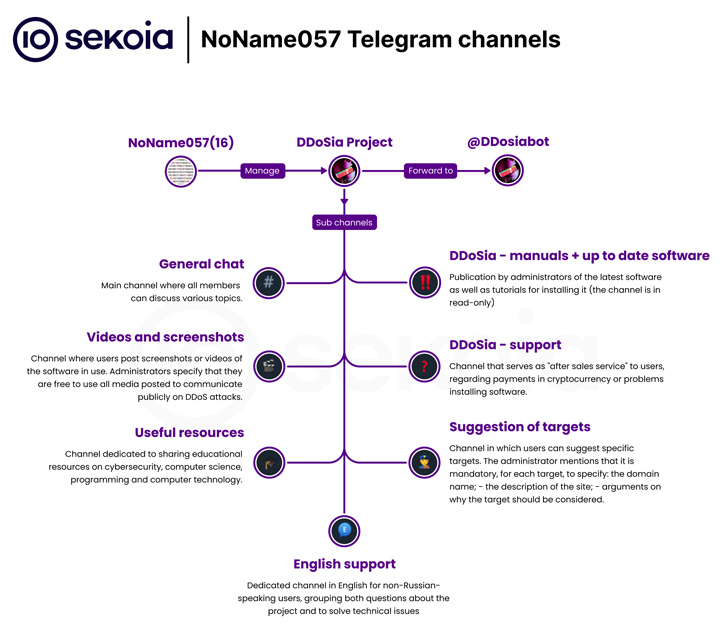
The threat actors powering the DDoSia attack resource have come up with a new edition that incorporates a new mechanism to retrieve the list of targets to be bombarded with junk HTTP requests in an try to provide them down.
The up-to-date variant, written in Golang, “implements an further security system to conceal the list of targets, which is transmitted from the [command-and-control] to the people,” cybersecurity firm Sekoia reported in a complex write-up.
DDoSia is attributed to a pro-Russian hacker group referred to as NoName(057)16. Introduced in 2022 and a successor of the Bobik botnet, the attack software is designed for staging distributed denial-of-assistance (DDoS) attacks against targets principally located in Europe as perfectly as Australia, Canada, and Japan.
Lithuania, Ukraine, Poland, Italy, Czechia, Denmark, Latvia, France, the U.K., and Switzerland have emerged as the most targeted countries over a period of time ranging from May 8 to June 26, 2023. A whole of 486 various sites were being impacted.
Python and Go-primarily based implementations of DDoSia have been unearthed to day, earning it a cross-platform software capable of staying applied throughout Windows, Linux, and macOS units.
“DDoSia is a multi-threaded software that conducts denial-of-support attacks towards focus on websites by consistently issuing network requests,” SentinelOne discussed in an evaluation printed in January 2023. “DDoSia issues requests as instructed by a configuration file that the malware gets from a C2 server when started off.”
DDoSia is distributed by means of a absolutely-automatic procedure on Telegram that makes it possible for people to register for the crowdsourced initiative in trade for a cryptocurrency payment and a ZIP archive made up of the attack toolkit.
What is noteworthy about the new version is the use of encryption to mask the record of targets to be attacked, indicating that the tool is getting actively managed by the operators.
“NoName057(16) is creating endeavours to make their malware appropriate with multiple operating systems, just about definitely reflecting their intent to make their malware accessible to a substantial variety of customers, ensuing in the targeting of a broader established of victims,” Sekoia claimed.
The enhancement comes as the U.S. Cybersecurity and Infrastructure Security Company (CISA) warned of focused denial-of-company (DoS) and DDoS attacks from a number of businesses in several sectors.
“These assaults can value an group time and funds and may impose reputational expenditures when resources and expert services are inaccessible,” the company said in a bulletin.
Though CISA did not deliver any more details, the warning overlaps with statements by Nameless Sudan on its Telegram channel that it experienced taken down the internet sites of the Division of Commerce, Social Security Administration (SSA), and the Treasury Department’s Electronic Federal Tax Payment Process (EFTPS).
Anonymous Sudan attracted attention very last thirty day period for carrying Layer 7 DDoS attacks from many Microsoft products and services, including OneDrive, Outlook, and Azure web portals. The tech big is monitoring the cluster less than the identify Storm-1359.
The hacking crew has asserted it can be conducting cyber strikes out of Africa on behalf of oppressed Muslims throughout the planet. But cybersecurity scientists imagine it to be a pro-Kremlin operation with no ties to Sudan and a member of the KillNet hacktivist collective.
In an investigation unveiled on June 19, 2023, Australian cybersecurity seller CyberCX characterized the entity as a “smokescreen for Russian interests.” The firm’s web-site has due to the fact become inaccessible, greeting website visitors with a “403 Forbidden” concept. The threat actor claimed accountability for the cyber attack.
“The motive for the attack: halt spreading rumors about us, and you have to explain to the truth of the matter and halt the investigations that we simply call the investigations of a doggy,” Nameless Sudan reported in a information posted on June 22, 2023.
Nameless Sudan, in a Bloomberg report past 7 days, further denied it was linked to Russia but acknowledged they share comparable passions, and that it goes just after “almost everything that is hostile to Islam.”
CISA’s latest advisory has also not long gone unnoticed, for the group posted a reaction on June 30, 2023, stating: “A modest Sudanese team with constrained abilities compelled ‘the most impressive government’ in the world to publish content articles and tweets about our attacks.”
Uncovered this report exciting? Stick to us on Twitter and LinkedIn to study far more unique material we post.
Some parts of this article are sourced from:
thehackernews.com

 Mexico-Based Hacker Targets Global Banks with Android Malware
Mexico-Based Hacker Targets Global Banks with Android Malware