A piece of malware recognized as DarkGate has been observed being unfold through prompt messaging platforms such as Skype and Microsoft Groups.
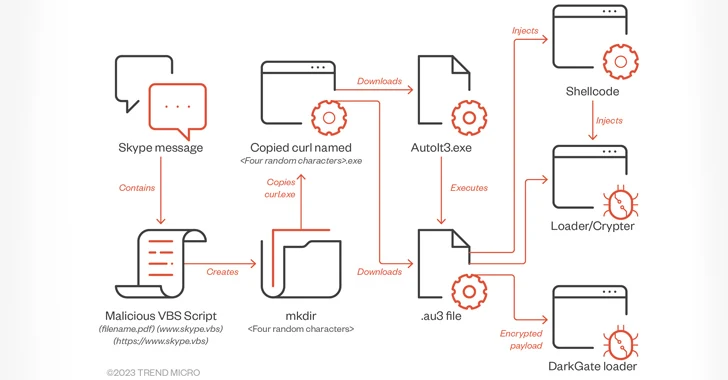
In these attacks, the messaging apps are used to provide a Visual Simple for Programs (VBA) loader script that masquerades as a PDF document, which, when opened, triggers the obtain and execution of an AutoIt script developed to start the malware.
“It is unclear how the originating accounts of the prompt messaging programs ended up compromised, however it is hypothesized to be both through leaked qualifications accessible through underground community forums or the preceding compromise of the dad or mum organization,” Trend Micro said in a new evaluation posted Thursday.

DarkGate, initially documented by Fortinet in November 2018, is a commodity malware that incorporates a huge array of characteristics to harvest sensitive data from web browsers, carry out cryptocurrency mining, and let its operators to remotely handle the infected hosts. It also functions as a downloader of further payloads such as Remcos RAT.
Social engineering strategies distributing the malware have witnessed a surge in current months, leveraging original entry techniques such as phishing emails and research engine optimization (Search engine optimization) poisoning to entice unwitting people into setting up it.
The uptick follows the malware author’s final decision to promote the malware on underground boards and hire it out on a malware-as-a-service basis to other danger actors right after years of utilizing it privately.
The use of Microsoft Teams chat concept as a propagation vector for DarkGate was formerly highlighted by Truesec early previous month, indicating that it truly is very likely remaining set to use by quite a few threat actors.

A greater part of the assaults have been detected in the Americas, followed closely by Asia, the Middle East, and Africa, for each Trend Micro.
The total infection technique abusing Skype and Groups intently resembles a malspam campaign claimed by Telekom Security in late August 2023, help save for the modify in the first access route.
“The danger actor abused a reliable romantic relationship amongst the two businesses to deceive the receiver into executing the connected VBA script,” Pattern Micro researchers Trent Bessell, Ryan Maglaque, Aira Marcelo, Jack Walsh, and David Walsh explained.

“Access to the victim’s Skype account allowed the actor to hijack an current messaging thread and craft the naming convention of the files to relate to the context of the chat historical past.”
The VBA script serves as a conduit to fetch the respectable AutoIt application (AutoIt3.exe) and an associated AutoIT script accountable for launching the DarkGate malware.
An alternate attack sequence entails the attackers sending a Microsoft Groups information that contains a ZIP archive attachment bearing an LNK file that, in change, is developed to run a VBA script to retrieve AutoIt3.exe and the DarkGate artifact.
“Cybercriminals can use these payloads to infect systems with numerous sorts of malware, together with facts stealers, ransomware, malicious and/or abused distant management tools, and cryptocurrency miners,” the researchers explained.
“As prolonged as external messaging is allowed, or abuse of trusted interactions via compromised accounts is unchecked, then this method for first entry can be done to and with any instant messaging (IM) applications.”
Located this article interesting? Observe us on Twitter and LinkedIn to study much more unique material we publish.
Some parts of this article are sourced from:
thehackernews.com

 FBI, CISA Warn of Rising AvosLocker Ransomware Attacks Against Critical Infrastructure
FBI, CISA Warn of Rising AvosLocker Ransomware Attacks Against Critical Infrastructure