A DarkGate malware campaign observed in mid-January 2024 leveraged a lately patched security flaw in Microsoft Windows as a zero-day utilizing bogus software program installers.
“During this campaign, end users were being lured employing PDFs that contained Google DoubleClick Digital Marketing and advertising (DDM) open up redirects that led unsuspecting victims to compromised web-sites hosting the Microsoft Windows SmartScreen bypass CVE-2024-21412 that led to destructive Microsoft (.MSI) installers,” Development Micro mentioned.
CVE-2024-21412 (CVSS rating: 8.1) problems an internet shortcut documents security attribute bypass vulnerability that permits an unauthenticated attacker to circumvent SmartScreen protections by tricking a sufferer into clicking on a specially crafted file.
It was mounted by Microsoft as part of its Patch Tuesday updates for February 2024, but not right before it was weaponized by a risk actor identified as Water Hydra (aka DarkCasino) to deliver the DarkMe malware in attacks focusing on money institutions.
The most current results from Pattern Micro display that the vulnerability has appear underneath broader exploitation than beforehand imagined, with the DarkGate marketing campaign leveraging it in conjunction with open redirects from Google Ads to proliferate the malware.

The complex attack chain commences with victims clicking on a connection embedded within a PDF attachment despatched by means of a phishing email. The connection deploys an open redirect from Google’s doubleclick[.]net area to a compromised web server hosting a destructive .URL internet shortcut file that exploits CVE-2024-21412.
Especially, the open up redirects are built to distribute pretend Microsoft software program installers (.MSI) masquerading as respectable computer software, such as Apple iTunes, Notion, NVIDIA, which arrive equipped with a facet-loaded DLL file that decrypted and contaminated customers with DarkGate (model 6.1.7).
It’s well worth noting that yet another now-fastened bypass flaw in Windows SmartScreen (CVE-2023-36025, CVSS score: 8.8) has been used by danger actors to produce DarkGate, Phemedrone Stealer, and Mispadu in excess of the earlier couple of months.
The abuse of Google Adverts systems allows risk actors to maximize the get to and scale of their attacks as a result of diverse ad strategies that are tailored for specific audiences.
“Employing faux software program installers, together with open redirects, is a strong mix and can direct to lots of infections,” security scientists Peter Girnus, Aliakbar Zahravi, and Simon Zuckerbraun said. “It is critical to keep on being vigilant and to instruct customers not to believe in any software program installer that they receive outside the house of formal channels.”
The advancement arrives as the AhnLab Security Intelligence Heart (ASEC) and eSentire revealed that counterfeit installers for Adobe Reader, Idea and Synaptics are staying distributed via phony PDF information and seemingly genuine websites to deploy details stealers like LummaC2 and the XRed backdoor.
It also follows the discovery of new stealer malware people like Planet Stealer, Rage Stealer (aka xStealer), and Tweaks (aka Tweaker), adding to the myriad of cyber threats that are able of harvesting delicate information and facts from compromised hosts.
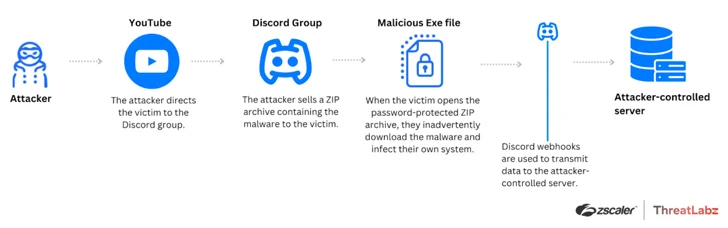
“Attackers are exploiting well-liked platforms, like YouTube and Discord, to distribute Tweaks to Roblox buyers, capitalizing on the capability of legit platforms to evade detection by web filter block lists that generally block regarded destructive servers,” Zscaler ThreatLabz claimed.
“Attackers share destructive files disguised as Frames Per Next (FPS) optimization deals with customers and, in flip, consumers infect their very own devices with Tweaks malware.”

The PowerShell-primarily based stealer is equipped to exfiltrate delicate details, which include consumer details, area, Wi-Fi profiles, passwords, Roblox IDs, and in-video game forex aspects, to an attacker-managed server via a Discord webhook.
Malvertising and social engineering strategies have also been noticed acting as an first obtain vector to disseminate a huge selection of stealer and distant accessibility trojans like Agent Tesla, CyberGate RAT, Fenix botnet, Matanbuchus, NarniaRAT, Remcos RAT, Rhadamanthys, SapphireStealer, and zgRAT.
Identified this report fascinating? Observe us on Twitter and LinkedIn to study additional distinctive content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Fortinet Warns of Severe SQLi Vulnerability in FortiClientEMS Software
Fortinet Warns of Severe SQLi Vulnerability in FortiClientEMS Software