A new cyber attack marketing campaign is leveraging the PowerShell script affiliated with a legit crimson teaming device to plunder NTLMv2 hashes from compromised Windows devices largely found in Australia, Poland, and Belgium.
The action has been codenamed Steal-It by Zscaler ThreatLabz.
“In this campaign, the menace actors steal and exfiltrate NTLMv2 hashes applying custom-made variations of Nishang’s Commence-CaptureServer PowerShell script, executing many system commands, and exfiltrating the retrieved facts by using Mockbin APIs,” security scientists Niraj Shivtarkar and Avinash Kumar mentioned.

Nishang is a framework and collection of PowerShell scripts and payloads for offensive security, penetration testing, and pink teaming.

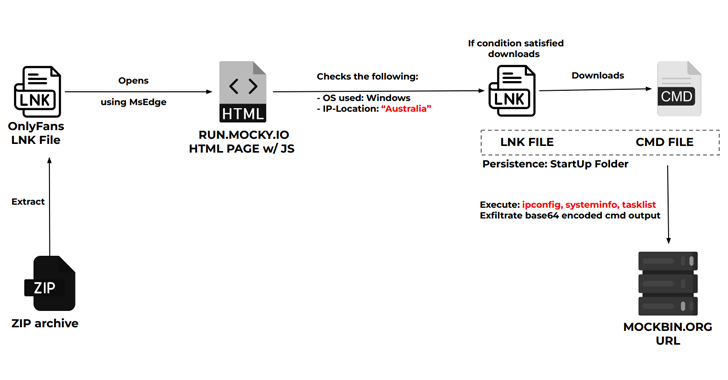
The assaults leverage as numerous as five distinct an infection chains, though they all leverage phishing e-mails made up of ZIP archives as the starting point to infiltrate precise targets applying geofencing strategies –
- NTLMv2 hash thieving infection chain, which employs a tailor made version of the aforementioned Get started-CaptureServer PowerShell script to harvest NTLMv2 hashes
- System info thieving infection chain, which OnlyFans lures to concentrate on Australian people into downloading a CMD file that pilfers procedure information
- Fansly whoami an infection chain, which makes use of explicit visuals of Ukrainian and Russian Fansly styles to entice Polish people into downloading a CMD file that exfiltrates the outcomes of the whoami command
- Windows update infection chain, which targets Belgium consumers with phony Windows update scripts designed to operate instructions like tasklist and systeminfo
It is worthy of noting that the very last attack sequence was highlighted by the Laptop Unexpected emergency Reaction Crew of Ukraine (CERT-UA) in May well 2023 as element of an APT28 marketing campaign directed versus federal government establishments in the country.
Future WEBINARWay Far too Vulnerable: Uncovering the State of the Identification Attack Area
Reached MFA? PAM? Support account defense? Discover out how nicely-outfitted your corporation certainly is against id threats
Supercharge Your Competencies
This raises the possibility that the Steal-It campaign could also be the work of the Russian state-sponsored menace actor.
“The danger actors’ custom PowerShell scripts and strategic use of LNK data files within just ZIP archives highlights their technological expertise,” the researchers reported. “The persistence managed by transferring information from the Downloads to Startup folder and renaming them underscores the menace actors’ dedication to prolonged access.”
Observed this article attention-grabbing? Stick to us on Twitter and LinkedIn to read through extra exclusive information we submit.
Some parts of this article are sourced from:
thehackernews.com

 New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World
New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World