Senior executives working in U.S.-dependent businesses are currently being focused by a new phishing marketing campaign that leverages a well-liked adversary-in-the-center (AiTM) phishing toolkit named EvilProxy to perform credential harvesting and account takeover attacks.
Menlo Security explained the action begun in July 2023, mainly singling out banking and economic providers, insurance, home management and authentic estate, and producing sectors.
“The danger actors leveraged an open redirection vulnerability on the occupation look for platform ‘indeed.com,’redirecting victims to destructive phishing pages impersonating Microsoft,” security researcher Ravisankar Ramprasad claimed in a report published last week.
EvilProxy, first documented by Resecurity in September 2022, functions as a reverse proxy which is set up in between the focus on and a authentic login web page to intercept credentials, two-variable authentication (2FA) codes, and session cookies to hijack accounts of fascination.

The risk actors powering the AiTM phishing kit are tracked by Microsoft underneath the moniker Storm-0835 and are estimated to have hundreds of buyers.
“These cyber criminals pay out monthly license service fees ranging from $200 to $1,000 USD and have out everyday phishing campaigns,” the tech huge explained. “Since so quite a few risk actors use these providers, it is impractical to attribute campaigns to unique actors.”
In the hottest set of attacks documented by Menlo Security, victims are sent phishing email messages with a misleading link pointing to In fact, which, in convert, redirects the person to an EvilProxy web page to harvest the credentials entered.
This is completed by getting advantage of an open up redirect flaw, which takes place when a failure to validate person enter causes a susceptible site to redirect people to arbitrary web pages, bypassing security guardrails.
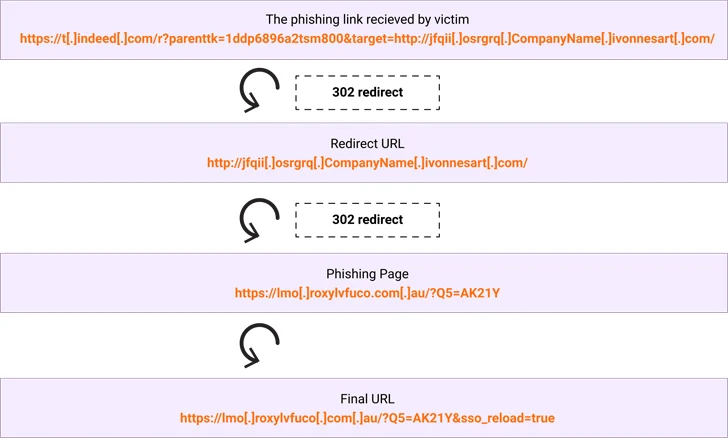
“The subdomain ‘t.without a doubt.com’ is supplied with parameters to redirect the customer to yet another focus on (illustration.com),” Ramprasad claimed.
“The parameters in the URL that stick to the ‘?’ are a combination of parameters unique to without a doubt.com and the focus on parameter whose argument is made up of the destination URL. As a result the person on clicking the URL ends up finding redirected to example.com. In an genuine attack, the consumer would be redirected to a phishing web page.”
The development comes as risk actors are leveraging Dropbox to build fake login pages with embedded URLs that, when clicked, redirect users to bogus web sites that are designed to steal Microsoft account credentials as portion of a small business email compromise (BEC) plan.

“It can be but another case in point of how hackers are using authentic solutions in what we contact BEC 3. attacks,” Look at Issue explained. “These attacks are exceptionally complicated to prevent and establish, for each security solutions and end consumers.”
Microsoft, in its Electronic Protection Report, mentioned how “menace actors are adapting their social engineering tactics and use of technology to have out much more sophisticated and expensive BEC attacks” by abusing cloud-centered infrastructure and exploiting dependable organization relationships.
It also will come as the Police Service of Northern Eire warned of an uptick in qishing e-mails, which entail sending an email with a PDF doc or a PNG graphic file containing a QR code in an endeavor to sidestep detection and trick victims into viewing malicious sites and credential harvesting pages.
Identified this short article fascinating? Abide by us on Twitter and LinkedIn to read through a lot more exceptional articles we post.
Some parts of this article are sourced from:
thehackernews.com


 Webinar: How vCISOs Can Navigating the Complex World of AI and LLM Security
Webinar: How vCISOs Can Navigating the Complex World of AI and LLM Security