Threat actors are more and more utilizing a phishing-as-a-company (PhaaS) toolkit dubbed EvilProxy to pull off account takeover assaults aimed at higher-ranking executives at notable organizations.
In accordance to Proofpoint, an ongoing hybrid campaign has leveraged the support to target hundreds of Microsoft 365 consumer accounts, sending about 120,000 phishing e-mails to hundreds of organizations around the world amongst March and June 2023.
Almost 39% of the hundreds of compromised customers are claimed to be C-level executives, which includes CEOs (9%) and CFOs (17%). The assaults have also singled out personnel with accessibility to economical assets or delicate details. At the very least 35% of all compromised buyers had extra account protections enabled.
The strategies are noticed as a reaction to the enhanced adoption of multi-aspect authentication (MFA) in enterprises, prompting risk actors to evolve their ways to bypass new security levels by incorporating adversary-in-the-center (AitM) phishing kits to siphon qualifications, session cookies, and a person-time passwords.
“Attackers use new sophisticated automation to precisely figure out in genuine-time whether or not a phished consumer is a large-level profile, and straight away acquire accessibility to the account, though disregarding much less worthwhile phished profiles,” the company security agency mentioned.
EvilProxy was to start with documented by Resecurity in September 2022, detailing its means to compromise consumer accounts connected with Apple iCloud, Fb, GoDaddy, GitHub, Google, Dropbox, Instagram, Microsoft, NPM, PyPI, RubyGems, Twitter, Yahoo, and Yandex, amongst some others.
It is sold as a subscription for $400 a month, a determine that can climb up to $600 for Google accounts.

PhaaS toolkits are an evolution of the cybercrime financial system, reducing the barrier for criminals with reduced technological techniques to have out complex phishing attacks at scale in a seamless and cost-effective manner.
“At present, all an attacker requires is to set up a campaign applying a stage-and-click interface with customizable choices, these types of as bot detection, proxy detection, and geofencing,” security researchers Shachar Gritzman, Moshe Avraham, Tim Kromphardt, Jake Gionet, and Eilon Bendet mentioned.
“This somewhat straightforward and minimal-expense interface has opened a floodgate of profitable MFA phishing action.”
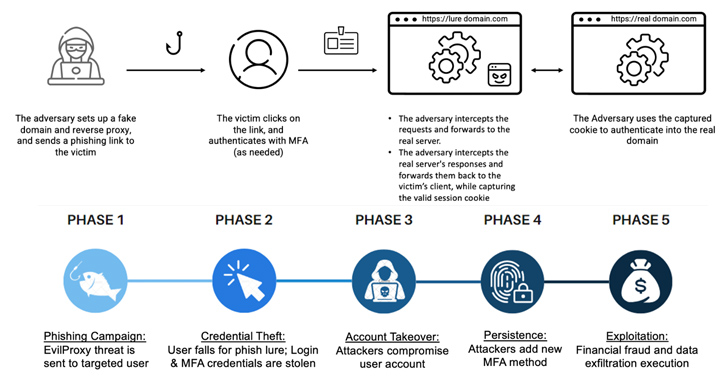
The newest wave of attacks commences with phishing e-mails that masquerade as trustworthy services like Adobe and DocuSign to trick recipients into clicking on malicious URLs that activate a multi-stage redirection chain to take them to a lookalike Microsoft 365 login page, which capabilities as a reverse proxy to stealthily capture the data entered in the sort.
But in a curious twist, the assaults deliberately skip user targeted visitors originating from Turkish IP addresses by redirecting them to legitimate sites, indicating that the campaign operators could be dependent out of the nation.

A profitable account takeover is adopted by the risk actor taking ways to “cement their foothold” in the organization’s cloud surroundings by adding their very own MFA approach, such as a two-factor authenticator application, so as to get hold of persistent distant obtain and conduct lateral movement and malware proliferation.
The accessibility is even more monetized to possibly carry out financial fraud, exfiltrate confidential info, or sell the compromised user accounts to other attackers.
“Reverse proxy threats (and EvilProxy in unique) are a potent danger in modern dynamic landscape and are outcompeting the significantly less capable phish kits of the earlier,” the researchers said, pointing out that “not even MFA is a silver bullet versus sophisticated cloud-based mostly threats.”
“Though these attacks’ first danger vector is email-primarily based, their final goal is to compromise and exploit valuable cloud person accounts, assets, and details.”

The progress comes as Imperva revealed particulars of an ongoing Russian-origin phishing marketing campaign that aims to deceive prospective targets and steal their credit rating card and bank info considering the fact that at the very least May well 2022 via booby-trapped backlinks shared through WhatsApp messages.
The activity spans 800 distinct fraud domains, impersonating far more than 340 organizations throughout 48 languages. This includes properly-recognised financial institutions, postal solutions, bundle supply expert services, social media, and e-commerce web sites.
“By leveraging a large-good quality, single-site application, the scammers were equipped to dynamically develop a convincing web site that impersonated a respectable site, fooling buyers into a untrue sense of security,” Imperva said.
In nevertheless an additional variation of a social engineering attack identified by eSentire, destructive actors have been noticed speaking to advertising professionals on LinkedIn in an try to distribute a .NET-primarily based loader malware codenamed HawkEyes that, in transform, is utilized to launch Ducktail, an data stealer with a unique emphasis on accumulating Facebook Company account data.
“Ducktail is known to concentrate on Fb Ad and Business accounts,” eSentire researchers explained. “Operators will use stolen login data to increase email addresses to Fb Business accounts. When e-mail are added, a registration backlink is created by which the threat actor can grant them selves access.”
Located this post attention-grabbing? Stick to us on Twitter and LinkedIn to examine additional exceptional information we put up.
Some parts of this article are sourced from:
thehackernews.com

 Interpol Busts Phishing-as-a-Service Platform ’16Shop,’ Leading to 3 Arrests
Interpol Busts Phishing-as-a-Service Platform ’16Shop,’ Leading to 3 Arrests