Risk actors are actively exploiting a just lately disclosed critical security flaw in the WooCommerce Payments WordPress plugin as component of a massive targeted campaign.
The flaw, tracked as CVE-2023-28121 (CVSS score: 9.8), is a case of authentication bypass that enables unauthenticated attackers to impersonate arbitrary consumers and perform some actions as the impersonated person, together with an administrator, most likely main to web-site takeover.
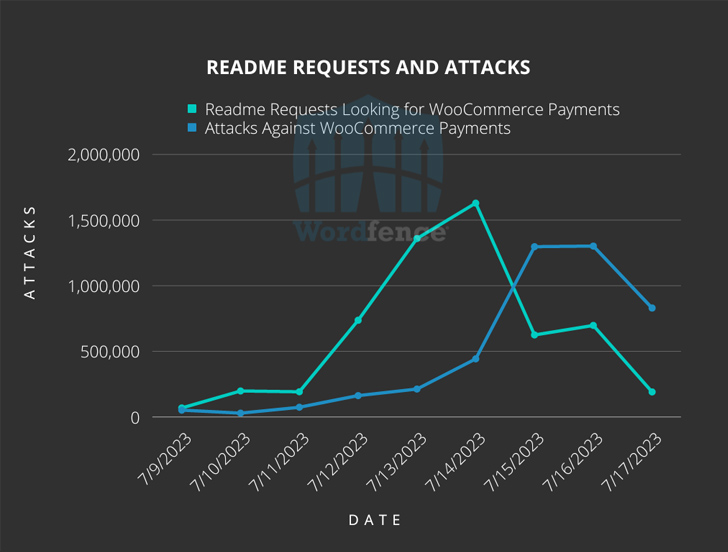
“Large-scale attacks versus the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks versus 157,000 web-sites on Saturday, July 16, 2023,” Wordfence security researcher Ram Gall explained in a Monday article.
Versions 4.8. by way of 5.6.1 of WooCommerce Payments are vulnerable. The plugin is set up on about 600,000 web sites. Patches for the bug had been unveiled by WooCommerce back again in March 2023, with WordPress issuing automobile-updates to websites utilizing impacted variations of the computer software.
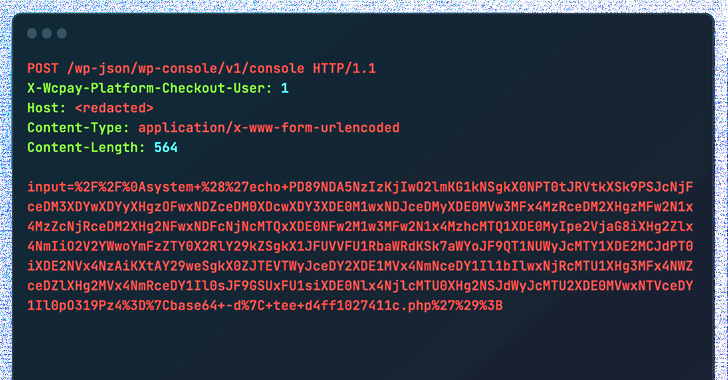
A typical denominator noticed in the assaults entails the use of the HTTP request header “X-Wcpay-System-Checkout-User: 1” that triggers prone web pages to deal with any further payloads as coming from an administrative consumer.
Wordfence explained the aforementioned loophole is becoming weaponized to deploy the WP Console plugin, which can be made use of by an administrator to execute malicious code and set up a file uploader to established up persistence and backdoor the compromised internet site.
Adobe ColdFusion Flaws Exploited in the Wild
The disclosure arrives as Immediate7 documented that it noticed active exploitation of Adobe ColdFusion flaws in several shopper environments commencing July 13, 2023, to deploy web shells on contaminated endpoints.
“Risk actors show up to be exploiting CVE-2023-29298 in conjunction with a secondary vulnerability,” Swift7 security researcher Caitlin Condon mentioned. The further flaw seems to be CVE-2023-38203 (CVSS rating: 9.8), a deserialization flaw that was dealt with in an out-of-band update unveiled on July 14.
Forthcoming WEBINARShield Towards Insider Threats: Master SaaS Security Posture Management
Concerned about insider threats? We have obtained you included! Be part of this webinar to take a look at practical approaches and the strategies of proactive security with SaaS Security Posture Administration.
Sign up for Today
CVE-2023-29298 (CVSS score: 7.5) worries an accessibility manage bypass vulnerability impacting ColdFusion 2023, ColdFusion 2021 Update 6 and beneath, and ColdFusion 2018 Update 16 and down below.
“The vulnerability permits an attacker to entry the administration endpoints by inserting an surprising supplemental ahead slash character in the asked for URL,” Swift7 disclosed previous week.
Quick7, having said that, warned that the resolve for CVE-2023-29298 is incomplete and that it could be trivially modified to bypass the patches produced by Adobe.
End users are encouraged to update to the hottest edition of Adobe ColdFusion to safe against opportunity threats, due to the fact the fixes put in put to resolve CVE-2023-38203 breaks the exploit chain.
Identified this write-up intriguing? Follow us on Twitter and LinkedIn to browse a lot more exceptional articles we post.
Some parts of this article are sourced from:
thehackernews.com

 JumpCloud Blames ‘Sophisticated Nation-State’ Actor for Security Breach
JumpCloud Blames ‘Sophisticated Nation-State’ Actor for Security Breach