A economically determined danger actor has been outed as an first entry broker (IAB) that sells accessibility to compromised companies for other adversaries to conduct comply with-on attacks these kinds of as ransomware.
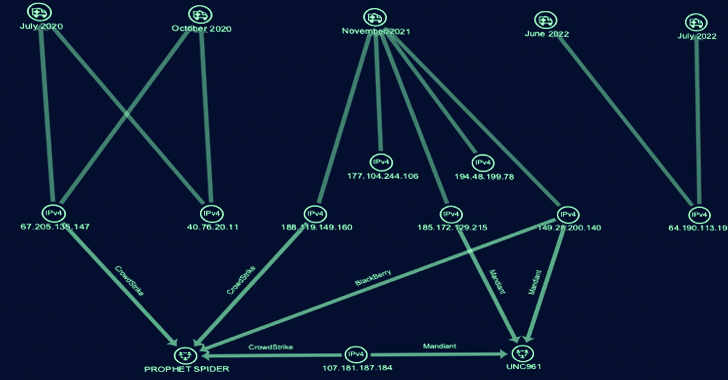
SecureWorks Counter Menace Unit (CTU) has dubbed the e-crime group Gold Melody, which is also known by the names Prophet Spider (CrowdStrike) and UNC961 (Mandiant).
“This fiscally enthusiastic group has been lively considering that at minimum 2017, compromising corporations by exploiting vulnerabilities in unpatched internet-struggling with servers,” the cybersecurity enterprise stated.
“The victimology suggests opportunistic attacks for fiscal acquire fairly than a targeted campaign conducted by a state-sponsored menace group for espionage, destruction, or disruption.”

Gold Melody has been previously connected to attacks exploiting security flaws in JBoss Messaging (CVE-2017-7504), Citrix ADC (CVE-2019-19781), Oracle WebLogic (CVE-2020-14750 and CVE-2020-14882), GitLab (CVE-2021-22205), Citrix ShareFile Storage Zones Controller (CVE-2021-22941), Atlassian Confluence (CVE-2021-26084), ForgeRock AM (CVE-2021-35464), and Apache Log4j (CVE-2021-44228) servers.
The cybercrime team has been observed increasing its victimology footprint to strike retail, wellbeing care, electrical power, fiscal transactions, and substantial-tech organizations in North The usa, Northern Europe, and Western Asia as of mid-2020.
Mandiant, in an examination printed in March 2023, reported that “in several scenarios, UNC961 intrusion action has preceded the deployment of Maze and Egregor ransomware from distinctive abide by-on actors.”
It even further described the group as “resourceful in their opportunistic angle to original entry operations” and famous it “employs a value-successful approach to attain first accessibility by exploiting not too long ago disclosed vulnerabilities employing publicly out there exploit code.”
Aside from relying on a varied arsenal comprising web shells, designed-in operating system software, and publicly available utilities, it’s recognised to use proprietary distant obtain trojans (RATs) and tunneling equipment these kinds of as GOTROJ (aka MUTEPUT), BARNWORK, HOLEDOOR, DARKDOOR, AUDITUNNEL, HOLEPUNCH, LIGHTBUNNY, and HOLERUN to execute arbitrary commands, acquire program data, and build a reverse tunnel with a tough-coded IP deal with.
Secureworks, which joined Gold Melody to five intrusions concerning July 2020 and July 2022, mentioned these attacks entailed the abuse of a unique set of flaws, which includes those impacting Oracle E-Business Suite (CVE-2016-0545), Apache Struts (CVE-2017-5638), Sitecore XP (CVE-2021-42237), and Flexera FlexNet (CVE-2021-4104) to get original access.
Impending WEBINARLevel-Up SaaS Security: A In depth Guidebook to ITDR and SSPM
Continue to be forward with actionable insights on how ITDR identifies and mitigates threats. Discover about the indispensable position of SSPM in making sure your identity stays unbreachable.
Supercharge Your Capabilities
A profitable foothold is succeeded by the deployment of web shells for persistence, adopted by creating directories in the compromised host to stage the instruments used in the an infection chain.
“Gold Melody conducts a substantial amount of scanning to comprehend a victim’s setting,” the business said. “Scanning starts shortly soon after getting obtain but is recurring and ongoing through the intrusion.”
The reconnaissance phase paves the way for credential harvesting, lateral motion, and knowledge exfiltration. That said, all five attacks in the end proved to be unsuccessful.
“Gold Melody functions as a financially enthusiastic IAB, marketing access to other risk actors,” the business concluded. “The buyers subsequently monetize the obtain, possible via extortion by way of ransomware deployment.”
“Its reliance on exploiting vulnerabilities in unpatched internet-dealing with servers for entry reinforces the worth of robust patch administration.”
Observed this short article intriguing? Observe us on Twitter and LinkedIn to read through additional exclusive content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Ukrainian Hacker Suspected to be Behind “Free Download Manager” Malware Attack
Ukrainian Hacker Suspected to be Behind “Free Download Manager” Malware Attack