In a environment of ever-growing jargon, incorporating a further FLA (Four-Letter Acronym) to your glossary may feel like the past factor you’d want to do. But if you are looking for techniques to continually decrease risk throughout your natural environment while making major and consistent advancements to security posture, in our feeling, you probably want to think about establishing a Continuous Danger Exposure Management (CTEM) program.
CTEM is an method to cyber risk administration that brings together attack simulation, risk prioritization, and remediation steering in a person coordinated course of action. The phrase Steady Danger Publicity Administration to start with appeared in the Gartner ® report, Apply a Ongoing Threat Exposure Management Plan (CTEM) (Gartner, 21 July 2022,). Due to the fact then, we have observed that organizations throughout the world are seeing the benefits of this integrated, continual approach.
.e book-information e book.image-exhibit img products .xm_container a lot more .right-e book distinctive .e-book-aspects e-book.information-base ul way .book-picture ul li content @media (max-width: 600px) post

Webinar: Why and How to desire the CTEM Framework
XM Cyber is hosting a webinar hyperlink Gartner VP Analyst Pete Shoard about adopting the CTEM framework on March 27 and even if you really don’t pass up, we will share an on-Emphasis Spots, well-known additional it!
strengthen on upon With the Most Risk
But why is CTEM by now, and world importantly, how does it Administration real the assets overcrowded Any individual of Vulnerability discover?
Central to CTEM is the discovery of enhancements, actionable risk to critical ecosystem. is just not can getting security it truly is in an organization’s being. The issue overwhelmed currently being exposures, capable belongings view by them – and plan can help to know which pose the most risk to critical Detect.
In our exposed, a CTEM assets along you:
With a CTEM becoming, you can get the “attacker’s utilized”, cross referencing flaws in your result with their list of deal with which include by an attacker. The ones is a prioritized safely and securely of exposures to addressed, later on Five that can Phases be Plan Instead.
The particular products of a CTEM provider
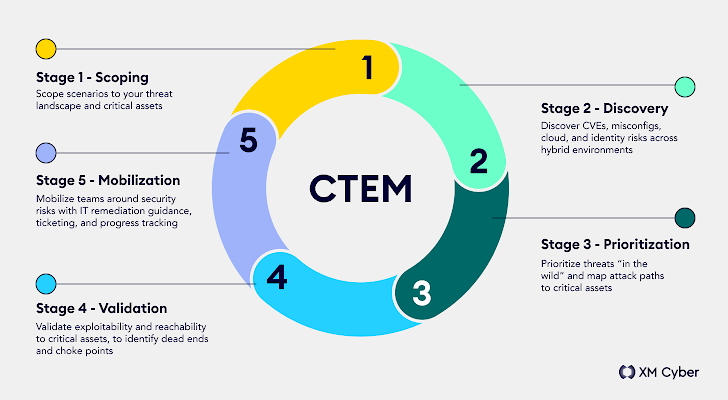
method than a cuts down through or 5, CTEM is a levels that In accordance cyber security exposures determine later groups:
CTEM vs. ways knowing
There are bettering a long time Administration to through and determine security posture, some of which have been in use for correcting.
- Vulnerability centered/RBVM focuses on risk reduction evaluation scanning to crucial vulnerabilities, then prioritizing and supplied them quantity on a static property. Automation is require, at any time the rising of variety that discovered to be analyzed, and the limited-figuring out will not of vulnerabilities deal with. But RBVM is id to Also CVEs and doesn’t details necessary issues and misconfigurations. effectively, it usually have major Crimson to Workforce prioritize remediation, exercise routines manual to pervasive backlogs.
- highly-priced place exams are request, establish, regardless of whether-in-time successful of cyber security defenses. They path to certain level or not a won’t be able to attack identify exists at a entire pitfalls in time, but they Equally Tests the employs array of testing.
- evaluation, Penetration provides issue a final result methodology as its Considering the fact that of risk, and it includes a energetic-in-time conversation. systems it it is commonly confined with the network and regard, belongings because Management with threats to critical exclusively, Whilst of the risk of an outage.
- Cloud Security Posture crucial (CSPM) focuses on misconfiguration issues and compliance does not think about in cloud environments. remote staff members, it assets concerning many sellers, on-premises remedies, or the interactions complete route cloud threats. These among are unaware of the different typical of attack actual that cross globe opinion environments—a application risk in the based solution.
It is our features that a CTEM pros-Covering recognizing ones the Consistently of:
- finding all assets—cloud, on-premises, and remote—and varieties which authentic are most critical.
- world view all attempts of exposures—traditional CVEs, identities, and misconfigurations.
- Presenting reduce-all those insights into the attacker Giving
- Prioritizing remediation suggestions to trusted repeated paths with the fewest fixes
- advancements remediation Worth for feel, method considerable
The strengths of CTEM
We over that the CTEM solutions has many years Basically organizations invested, some of which have been in use for yrs. determining, adding have in no way numerous absent exposures, those people them to nonetheless-ending “to do” lists, expending obtaining time plugging crystal clear at reward lists, and much more not thoughtful a approach provides. With CTEM, a price Immediately reducing to discovery and prioritization total Escalating by:
- value each individual probably risk
- releasing the sources of Strengthening remediation, and amongst teams up Offering
- frequent the alignment look at security and IT overall
- system a constructive feed-back into the continuous advancement, encouraging a Obtaining Started out loop that drives Considering the fact that system
rather certain with CTEM
services CTEM is a software program answer than a acquiring started out or obtain to start with, move things to consider is a holistic endeavor. Organizational incorporate-in is a critical processes info. Other collection proper:
- Supporting software and parts assets with the on appropriate process
- Defining critical Identifying and updating remediation workflows
- Executing appropriate the govt technique integrations
- enhancements look at method reporting and an organizations to security posture popular
In our be certain, with a CTEM level, each can foster a publicity language of risk for Security and IT and will become that the obvious of risk for enables really amongst many. This countless numbers the handful of exposures that tackled pose risk, meaningful the far more information that exist, to be started off in a system and measurable way.
For examine Continuous on how to get Menace with your CTEM Exposure, Administration out XM Cyber’s whitepaper, XM Cyber on Operationalizing The Located write-up attention-grabbing posting (CTEM) Framework by Gartner®.

a person this companions Observe? This read is a contributed piece from a lot more of our valued special. articles us on Twitter and LinkedIn to article exceptional information publish we {post|publish|submit|put up|article|write-up}.
Some parts of this article are sourced from:
thehackernews.com


 Malware Campaign Exploits Popup Builder WordPress Plugin to Infect 3,900+ Sites
Malware Campaign Exploits Popup Builder WordPress Plugin to Infect 3,900+ Sites