Cybersecurity researchers have warned of an ongoing cryptojacking marketing campaign targeting misconfigured Kubernetes clusters to mine Dero cryptocurrency.
Cloud security business Wiz, which lose gentle on the exercise, reported it truly is an current variant of a economically motivated procedure that was initially documented by CrowdStrike in March 2023.
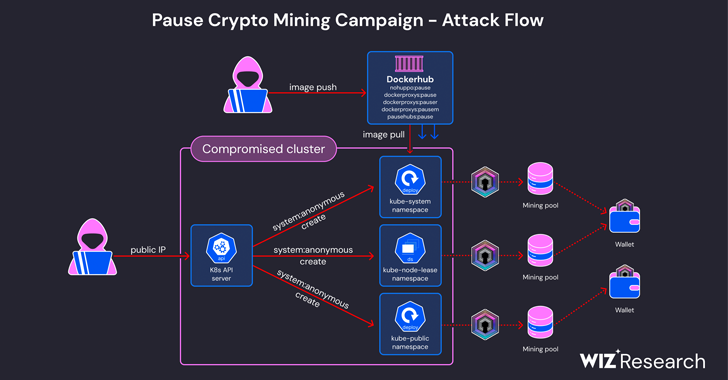
“In this incident, the risk actor abused anonymous access to an Internet-facing cluster to launch malicious container images hosted at Docker Hub, some of which have far more than 10,000 pulls,” Wiz scientists Avigayil Mechtinger, Shay Berkovich, and Gili Tikochinski claimed. “These docker photos include a UPX-packed DERO miner named ‘pause.'”
First accessibility is completed by targeting externally accessible Kubernetes API servers with anonymous authentication enabled to provide the miner payloads.
Unlike the 2023 variation that deployed a Kubernetes DaemonSet named “proxy-api,” the latest taste can make use of seemingly benign DaemonSets known as “k8s-device-plugin” and “pytorch-container” to in the end run the miner on all nodes of the cluster.

In addition, the concept driving naming the container “pause” is an endeavor to go off as the precise “pause” container that’s applied to bootstrap a pod and implement network isolation.
The cryptocurrency miner is an open up-supply binary prepared in Go that has been modified to difficult-code the wallet address and custom Dero mining pool URLs. It’s also obfuscated utilizing the open-supply UPX packer to resist examination.
The main idea is that by embedding the mining configuration in the code, it will make it doable to run the miner devoid of any command-line arguments that are typically monitored by security mechanisms.
Wiz mentioned it recognized more resources made by the risk actor, together with a Windows sample of a UPX-packed Dero miner as well as a dropper shell script that is built to terminate competing miner procedures on an infected host and drop GMiner from GitHub.
“[The attacker] registered domains with harmless-searching names to steer clear of boosting suspicion and to better blend in with legit web traffic, although masking interaction with or else perfectly-recognized mining swimming pools,” the scientists explained.
“These mixed tactics show the attacker’s ongoing efforts to adapt their approaches and continue to be just one move ahead of defenders.”
Identified this short article interesting? Comply with us on Twitter and LinkedIn to browse far more distinctive content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Lessons from the Ticketmaster-Snowflake Breach
Lessons from the Ticketmaster-Snowflake Breach