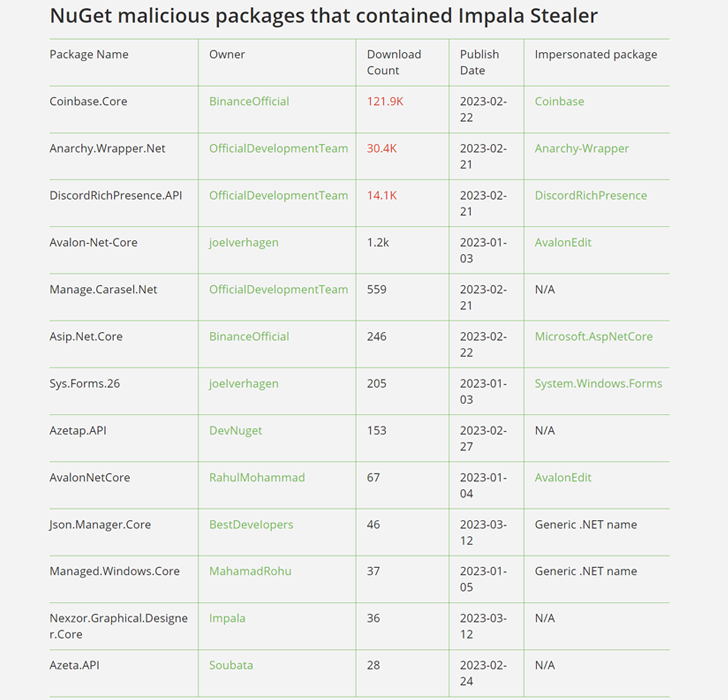
Cybersecurity scientists have comprehensive the interior workings of the cryptocurrency stealer malware that was distributed by way of 13 malicious NuGet deals as part of a source chain attack targeting .NET developers.
The complex typosquatting campaign, which was specific by JFrog late final thirty day period, impersonated respectable offers to execute PowerShell code built to retrieve a follow-on binary from a challenging-coded server.
The two-stage attack culminates in the deployment of a .NET-centered persistent backdoor, called Impala Stealer, which is capable of getting unauthorized obtain to users’ cryptocurrency accounts.
“The payload applied a extremely rare obfuscation strategy, named ‘.NET AoT compilation,’ which is a ton a lot more stealthy than making use of ‘off the shelf’ obfuscators although continue to creating the binary really hard to reverse engineer,” JFrog told The Hacker News in a assertion.
.NET AoT compilation is an optimization system that lets apps to be forward-of-time compiled to indigenous code. Native AOT apps also have faster startup time and scaled-down memory footprints, and can run on a machine with out .NET runtime mounted.
The second-phase payload comes with an car-update system that enables it to retrieve new versions of the executable from a distant site. It further achieves persistence by injecting JavaScript code into Discord or Microsoft Visible Studio Code applications, thereby activating the start of the stealer binary.
The binary then proceeds to search for the installation of the Exodus Wallet desktop application and inserts JavaScript code into many HTML data files in buy to harvest and exfiltrate sensitive knowledge to a tough-coded Discord webhook.
The JavaScript snippet, for its portion, is fetched from an online paste internet site from the place it can be previously been deleted. That reported, it really is suspected that the code may well have been used to steal consumer credentials and obtain other info of interest.
“The undesirable actors used typosquatting tactics to deploy a customized malicious payload […] which targets the Exodus crypto wallet and leaks the victim’s credentials to cryptocurrency exchanges, by applying code injection,” Shachar Menashe, senior director at JFrog Security Research, mentioned.
Forthcoming WEBINARLearn to Safe the Identification Perimeter – Proven Procedures
Strengthen your company security with our impending qualified-led cybersecurity webinar: Investigate Identification Perimeter strategies!
Will not Miss out on Out – Help you save Your Seat!
“Our investigation proves no open source software repository is totally have confidence in-deserving, so security measures need to be taken at every single move of the software program improvement lifecycle to be certain the software program offer chain remains secure.”
The findings come as Phylum unearthed a malicious npm bundle named mathjs-min that was uploaded to the repository on March 26, 2023, and observed to harbor a credential stealer that grabs Discord passwords from the official application as well as web browsers like Google Chrome, Courageous, and Opera.
“This offer is actually a modified version of the extensively applied Javascript math library mathjs, and was injected with malicious code soon after becoming forked,” the software program provide chain security organization claimed. “The modified edition was then posted to NPM with the intention of passing it off as a minified variation of the genuine mathjs library.”
Identified this report attention-grabbing? Abide by us on Twitter and LinkedIn to study extra distinctive material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Estonian National Charged in U.S. for Acquiring Electronics and Metasploit Pro for Russian Military
Estonian National Charged in U.S. for Acquiring Electronics and Metasploit Pro for Russian Military