Zero-working day vulnerabilities in Windows Installers for the Atera remote checking and administration software program could act as a springboard to launch privilege escalation attacks.
The flaws, found out by Mandiant on February 28, 2023, have been assigned the identifiers CVE-2023-26077 and CVE-2023-26078, with the issues remediated in variations 1.8.3.7 and 1.8.4.9 introduced by Atera on April 17, 2023, and June 26, 2023, respectively.
“The means to initiate an operation from a NT AUTHORITYSYSTEM context can present prospective security challenges if not adequately managed,” security researcher Andrew Oliveau explained. “For occasion, misconfigured Tailor made Actions operating as NT AUTHORITYSYSTEM can be exploited by attackers to execute nearby privilege escalation attacks.”
Effective exploitation of these kinds of weaknesses could pave the way for the execution of arbitrary code with elevated privileges.
Both the flaws reside in the MSI installer’s fix performance, likely generating a scenario exactly where operations are activated from an NT AUTHORITYSYSTEM context even if they are initiated by a regular person.
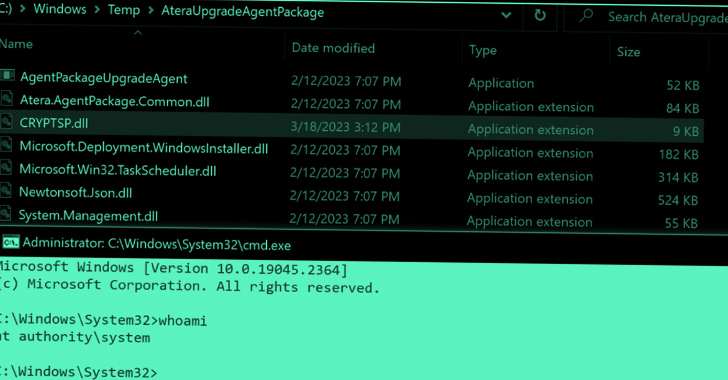
In accordance to the Google-owned menace intelligence company, Atera Agent is vulnerable to a area privilege escalation attack that can be exploited by means of DLL hijacking (CVE-2023-26077), which could then be abused to get hold of a Command Prompt as the NT AUTHORITYSYSTEM consumer.
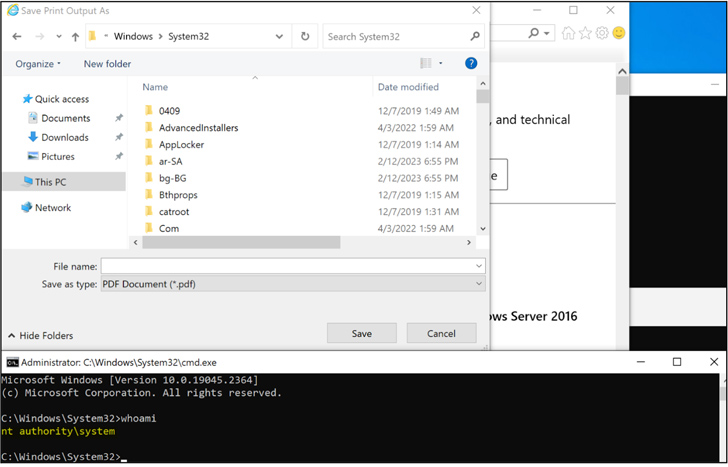
CVE-2023-26078, on the other hand, problems the “execution of program commands that cause the Windows Console Host (conhost.exe) as a baby process,” as a outcome opening up a “command window, which, if executed with elevated privileges, can be exploited by an attacker to carry out a local privilege escalation attack.”
“Misconfigured Tailor made Steps can be trivial to recognize and exploit, thereby posing considerable security risks for corporations,” Oliveau said. “It is critical for program developers to completely review their Tailor made Actions to prevent attackers from hijacking NT AUTHORITYSYSTEM operations triggered by MSI repairs.”
Upcoming WEBINARShield From Insider Threats: Grasp SaaS Security Posture Administration
Concerned about insider threats? We’ve got you coated! Sign up for this webinar to investigate simple strategies and the tricks of proactive security with SaaS Security Posture Administration.
Be part of Now
The disclosure comes as Kaspersky get rid of more light-weight on a now-preset, serious privilege escalation flaw in Windows (CVE-2023-23397, CVSS rating: 9.8) that has come less than active exploitation in the wild by menace actors making use of a specifically crafted Outlook endeavor, concept or calendar party.
Though Microsoft disclosed previously that Russian country-condition groups weaponized the bug given that April 2022, proof collected by the antivirus vendor has discovered that authentic-environment exploit makes an attempt were carried out by an unidentified attacker concentrating on federal government and critical infrastructure entities in Jordan, Poland, Romania, Turkey, and Ukraine a thirty day period prior to the general public disclosure.
Uncovered this write-up interesting? Stick to us on Twitter and LinkedIn to go through extra special material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Google Messages Getting Cross-Platform End-to-End Encryption with MLS Protocol
Google Messages Getting Cross-Platform End-to-End Encryption with MLS Protocol