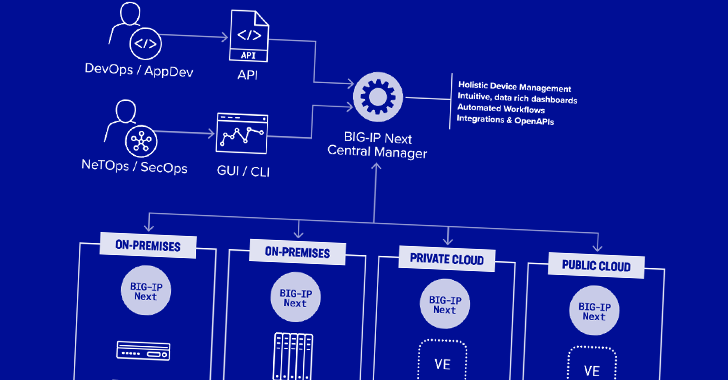
Two security vulnerabilities have been found out in F5 Up coming Central Supervisor that could be exploited by a danger actor to seize handle of the gadgets and generate concealed rogue administrator accounts for persistence.
The remotely exploitable flaws “can give attackers entire administrative regulate of the machine, and subsequently enable attackers to generate accounts on any F5 assets managed by the Next Central Supervisor,” security company Eclypsium mentioned in a new report.
A description of the two issues is as follows –
- CVE-2024-21793 (CVSS score: 7.5) – An OData injection vulnerability that could allow for an unauthenticated attacker to execute destructive SQL statements via the Huge-IP Subsequent Central Manager API
- CVE-2024-26026 (CVSS rating: 7.5) – An SQL injection vulnerability that could permit an unauthenticated attacker to execute destructive SQL statements by way of the Major-IP Subsequent Central Supervisor API
Both equally the flaws influence Subsequent Central Manager variations from 20..1 to 20.1.. The shortcomings have been resolved in edition 20.2..

Profitable exploitation of the bugs can end result in complete administrative handle of the machine, enabling attackers to blend it with other flaws to create new accounts on any Significant-IP Future asset managed by the Central Supervisor.
What is actually extra, these destructive accounts would remain hid from the Central Manager itself. This is created attainable by a server-facet ask for forgery (SSRF) vulnerability that would make it attainable to invoke an undocumented API and make the accounts.

“This usually means that even if the admin password is reset in the Central Manager, and the method is patched, attacker access may nevertheless remain,” the provide chain security enterprise claimed.
Also found by Eclypsium are two additional weaknesses that could simply just brute-force assaults against the admin passwords and permit an administrator to reset their passwords devoid of information of the prior one. An attacker could weaponize this issue to block legit obtain to the gadget from each and every account.
Though there are no indications that the vulnerabilities have arrive under lively exploitation in the wild, it can be suggested that customers update their scenarios to the newest variation to mitigate prospective threats.
“Networking and software infrastructure have turn out to be a important focus on of attackers in recent a long time,” Eclypsium said. “Exploiting these hugely privileged units can give adversaries an ideal way to obtain entry, unfold, and preserve persistence within just an natural environment.”
Uncovered this article exciting? Follow us on Twitter and LinkedIn to browse additional special material we post.
Some parts of this article are sourced from:
thehackernews.com

 A SaaS Security Challenge: Getting Permissions All in One Place
A SaaS Security Challenge: Getting Permissions All in One Place 