Wing Security announced currently that it now offers totally free discovery and a paid out tier for automated regulate in excess of countless numbers of AI and AI-driven SaaS purposes. This will enable companies to far better guard their intellectual home (IP) and facts towards the expanding and evolving challenges of AI utilization.
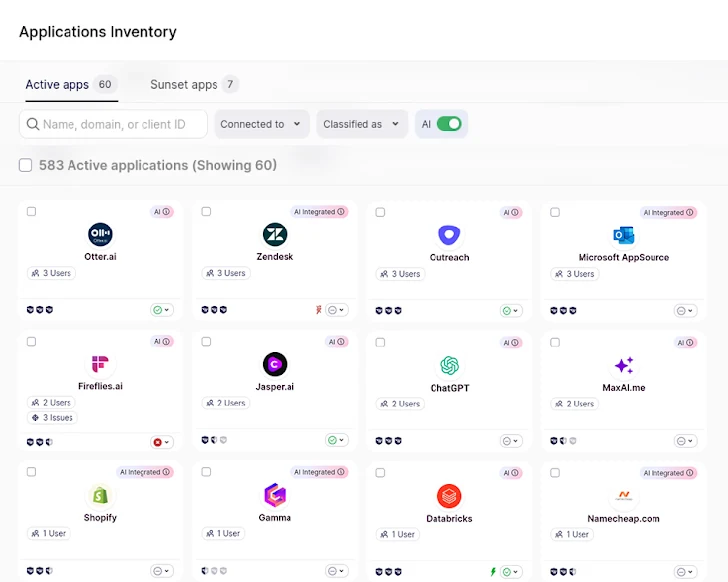
SaaS purposes seem to be to be multiplying by the day, and so does their integration of AI capabilities. According to Wing Security, a SaaS security company that investigated over 320 firms, a staggering 83.2% use GenAI purposes. Whilst this statistic may not arrive as a surprise, the analysis confirmed that 99.7% of organizations use SaaS purposes that leverage AI abilities to produce their companies. This use of GenAI in SaaS purposes that are not ‘pure’ AI usually goes unnoticed by security teams and end users alike.
70% of the most preferred GenAI applications could use your information to prepare their versions, and in numerous instances it is wholly up to you to configure it in another way.
When examining hundreds of AI-making use of SaaS programs, Wing Security was equipped to categorize the various strategies in which these applications use organizational data, as effectively as offer you a option to this new menace:
Facts storing: In some situations, information is saved by the AI for very long periods of time in many others, it can be saved for brief durations only. Storing facts enables AI finding out types, and potential versions, to frequently practice on it. That stated, the major worry is when considering the several distinctive sorts of attacks witnessed on SaaS purposes. When an software is compromised, the information it stores may be compromised as well.
Model education: By processing broad amounts of facts, AI systems can discover styles, developments, and insights that may elude human examination. Via device understanding algorithms, AI types discover from knowledge and adapt in excess of time, refining their efficiency and precision, ensuing in superior provider to their finish people. On the downside, permitting these types to find out your code, patents, sales, and advertising and marketing know-how supplies AI-using programs with the prospective suggests to commoditize your organization’s competitive edge. To some, these knowledge leaks are thought of far more sizeable than details leaks
The human ingredient: Specific AI programs leverage human validation to be certain the precision and reliability of the information they collect. This collaborative approach, generally referred to as human-in-the-loop or human-assisted AI, includes integrating human abilities into the algorithmic selection-earning method. This benefits in greater accuracy for the AI design, but also suggests a human, doing the job for the GenAI software, is uncovered to most likely delicate info and know-how.
Leveraging automation to combat AI-SaaS hazards
Wing’s lately released AI answer assures security teams will far better adapt to, and control, the ever-growing and pretty much unstoppable AI utilization in their companies. Their alternative follows 3 primary techniques – Know, Assess, Manage.
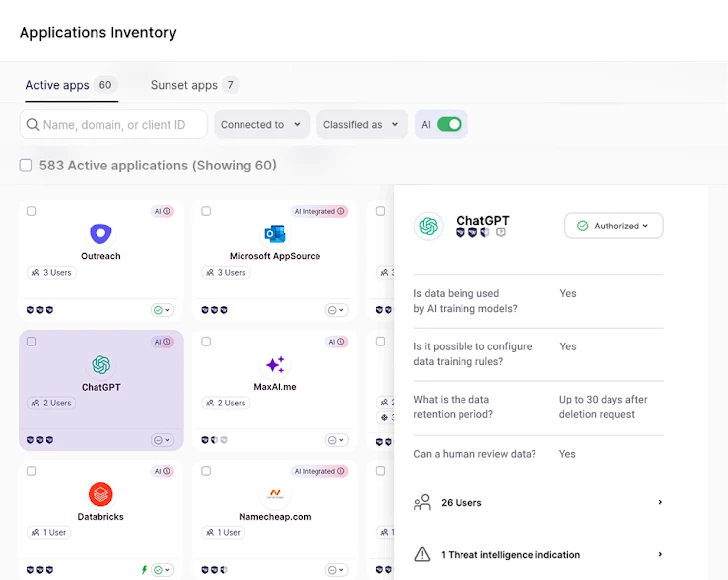
Know: As with numerous security threats, the first stage is to explore them all. In the circumstance of AI, it is not sufficient to simply just flag the “normal suspects” or the pure GenAI purposes this kind of as ChatGPT or Bard. With countless numbers of SaaS applications now utilizing AI to boost their company, discovery must involve any application leveraging purchaser information to enhance their designs. As with their earlier remedies, Wing is presenting this initial and fundamental stage as a absolutely free, self-support resolution for customers to self-onboard and start finding the magnitude of AI-run purposes made use of by their employees.
Assess: When AI-working with SaaS has been uncovered, Wing mechanically presents a security rating and facts the methods in which corporation data is employed by the AI: How very long is it stored for? Is there a human element? And most likely most importantly, is it configurable? Furnishing a in depth see of the application’s people, permissions, and security data. This computerized evaluation lets security teams to make greater-knowledgeable selections.
Handle: Wing’s discovery and assessment pin-points the most critical issues to address, making it possible for security teams to very easily fully grasp the level of risk and forms of steps wanted. For case in point, choosing whether or not they must permit a specific application’s usage or simply configure the AI factors to greater match their security plan.
The Mystery: Automating All Of The Earlier mentioned
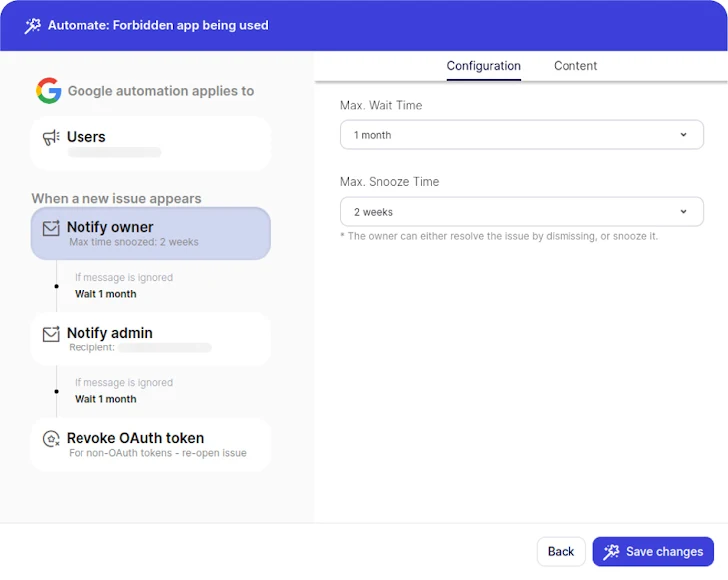
By automating Discovery, Evaluation and Management, security groups save time on figuring out exactly where to aim their efforts alternatively of spreading them selves slim hoping to clear up a massive and evolving attack area. Subsequently, this drastically lowers risk.
Wing’s automatic workflows also permit for a distinctive cross-organizational answer: By making it possible for people to immediately converse with the application’s admin or buyers, Wing prompts better-educated security remedies together with a stronger security society of inclusion alternatively than straightforward black or white listing.
In an era where by SaaS purposes are omnipresent, their integration with artificial intelligence raises a new form of obstacle. On the one particular hand, AI usage has come to be a terrific tool for boosting productiveness, and staff members need to be in a position to use it for its a lot of advantages. On the other hand, as the reliance on AI in SaaS apps carries on to surge, the opportunity pitfalls affiliated with knowledge usage develop into more pronounced.
Wing Security has responded to this obstacle by introducing a new solution, aimed at empowering corporations to navigate and control the escalating use of AI inside of their functions, when involving the end buyers in the loop and making certain they may perhaps use the AI-SaaS they require, securely. Their automatic command platform supplies a thorough knowing of how AI purposes make the most of organizational info and know-how, addressing issues this sort of as facts storing, product coaching, and the human ingredient in the AI loop. Security groups can preserve important time many thanks to obvious risk-prioritization and user involvement.
Identified this post attention-grabbing? Abide by us on Twitter and LinkedIn to browse more exclusive content material we post.
Some parts of this article are sourced from:
thehackernews.com


 Feds Warn of AndroxGh0st Botnet Targeting AWS, Azure, and Office 365 Credentials
Feds Warn of AndroxGh0st Botnet Targeting AWS, Azure, and Office 365 Credentials