The menace actor referred to as Cloud Atlas has been linked to a established of spear-phishing assaults on Russian enterprises.
Targets involved a Russian agro-industrial business and a condition-owned research company, according to a report from F.A.C.C.T., a standalone cybersecurity enterprise shaped after Team-IB’s official exit from Russia earlier this yr.
Cloud Atlas, lively given that at least 2014, is a cyber espionage team of unfamiliar origin. Also called Cleanse Ursa, Inception, Oxygen, and Purple October, the menace actor is identified for its persistent strategies focusing on Russia, Belarus, Azerbaijan, Turkey, and Slovenia.
In December 2022, Check Place and Optimistic Technologies in-depth multi-stage attack sequences that led to the deployment of a PowerShell-dependent backdoor referred to as PowerShower as perfectly as DLL payloads capable of communicating with an actor-controlled server.
Upcoming WEBINAR From User to ADMIN: Master How Hackers Gain Entire Control
Discover the mystery tactics hackers use to turn into admins, how to detect and block it ahead of it is much too late. Register for our webinar right now.
Sign up for Now
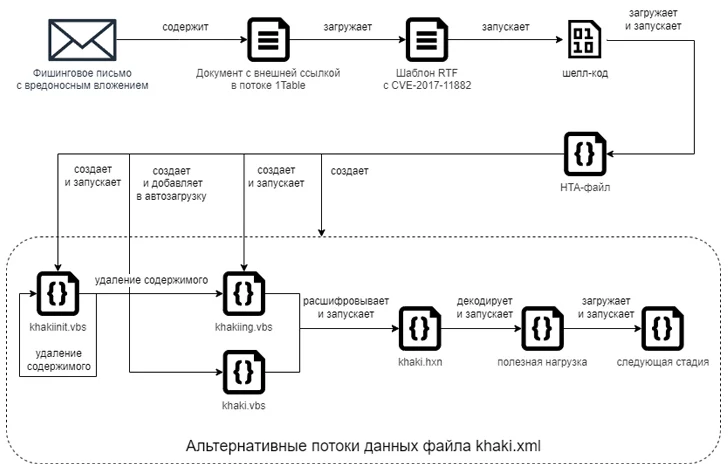
The setting up place is a phishing information bearing a entice document that exploits CVE-2017-11882, a 6-calendar year-aged memory corruption flaw in Microsoft Office’s Equation Editor, to kick-commence the execution of malicious payloads, a procedure Cloud Atlas has used as early as October 2018.
“The actor’s enormous spear-phishing campaigns continue to use its straightforward but helpful procedures in buy to compromise its targets,” Kaspersky mentioned in August 2019. “Contrary to a lot of other intrusion sets, Cloud Atlas has not preferred to use open up supply implants during its latest campaigns, in purchase to be a lot less discriminating.”
F.A.C.C.T. described the hottest destroy chain as related to the just one explained by Constructive Technologies, with successful exploitation of CVE-2017-11882 by using RTF template injection paving the way for shellcode that’s dependable for downloading and working an obfuscated HTA file. The mails originate from common Russian email solutions Yandex Mail and VK’s Mail.ru.
The malicious HTML software subsequently launches Visual Simple Script (VBS) files that are finally accountable for retrieving and executing an mysterious VBS code from a remote server.

“The Cloud Atlas group has been active for lots of years, carefully contemplating by way of each and every aspect of their attacks,” Favourable Technologies claimed of the team very last year.
“The group’s toolkit has not improved for years—they test to disguise their malware from researchers by making use of one-time payload requests and validating them. The group avoids network and file attack detection tools by employing genuine cloud storage and properly-documented application capabilities, in particular in Microsoft Business.”
The growth comes as the firm mentioned that at minimum 20 corporations found in Russia have been compromised using Decoy Dog, a modified edition of Pupy RAT, attributing it to an state-of-the-art persistent threat actor it calls Hellhounds.
The actively managed malware, in addition to allowing the adversary to remotely handle the contaminated host, arrives with a scriptlet built to transmit telemetry facts to an “automated” account on Mastodon with the title “Lamir Hasabat” (@lahat) on the Mindly.Social instance.
“After components on the 1st version of Decoy Pet ended up revealed, the malware authors went to a great deal of exertion to hamper its detection and analysis both equally in traffic and in the file program,” security scientists Stanislav Pyzhov and Aleksandr Grigorian explained.
Identified this write-up intriguing? Adhere to us on Twitter and LinkedIn to browse much more distinctive material we submit.
Some parts of this article are sourced from:
thehackernews.com


 British LAPSUS$ Teen Members Sentenced for High-Profile Attacks
British LAPSUS$ Teen Members Sentenced for High-Profile Attacks