A Chinese condition-sponsored risk exercise team tracked as RedGolf has been attributed to the use of a personalized Windows and Linux backdoor known as KEYPLUG.
“RedGolf is a significantly prolific Chinese point out-sponsored risk actor team that has likely been active for lots of many years towards a extensive assortment of industries globally,” Recorded Upcoming advised The Hacker News.
“The team has demonstrated the skill to promptly weaponize freshly claimed vulnerabilities (e.g. Log4Shell and ProxyLogon) and has a background of developing and utilizing a huge vary of tailor made malware households.”
The use of KEYPLUG by Chinese risk actors was 1st disclosed by Google-owned Manidant in March 2022 in attacks concentrating on numerous U.S. point out federal government networks among Could 2021 and February 2022.
Then in October 2022, Malwarebytes specific a individual set of assaults focusing on federal government entities in Sri Lanka in early August that leveraged a novel implant dubbed DBoxAgent to deploy KEYPLUG.
The two these strategies were attributed to Winnti (aka APT41, Barium, Bronze Atlas, or Wicked Panda), which Recorded Foreseeable future mentioned “intently overlaps” with RedGolf.
“We have not observed specific victimology as part of the most current highlighted RedGolf exercise,” Recorded Future claimed. “Having said that, we consider this action is possible becoming conducted for intelligence reasons somewhat than money achieve thanks to the overlaps with formerly described cyberespionage campaigns.”
The cybersecurity agency, in addition to detecting a cluster of KEYPLUG samples and operational infrastructure (codenamed GhostWolf) applied by the hacking team from at minimum 2021 to 2023, observed its use of other equipment like Cobalt Strike and PlugX.
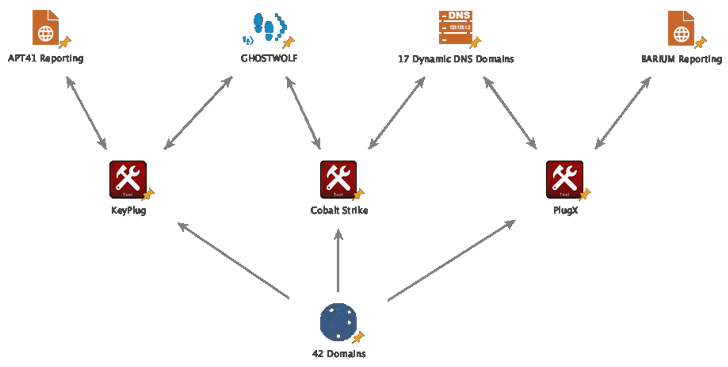
The GhostWolf infrastructure, for its portion, is made up of 42 IP addresses that operate as KEYPLUG command-and-management. The adversarial collective has also been observed utilizing a mixture of both equally traditionally registered domains and Dynamic DNS domains, usually showcasing a technology concept, to act as communication details for Cobalt Strike and PlugX.
“RedGolf will proceed to exhibit a higher operational tempo and swiftly weaponize vulnerabilities in exterior-going through corporate appliances (VPNs, firewalls, mail servers, etcetera.) to achieve first obtain to goal networks,” the organization said.
THN WEBINARBecome an Incident Reaction Pro!
Unlock the tricks to bulletproof incident response – Learn the 6-Stage process with Asaf Perlman, Cynet’s IR Chief!
Don’t Overlook Out – Help save Your Seat!
“Moreover, the group will likely carry on to undertake new tailor made malware families to add to present tooling these kinds of as KEYPLUG.”
To defend from RedGolf attacks, corporations are advisable to use patches routinely, observe accessibility to external dealing with network equipment, track and block identified command-and-management infrastructure, and configure intrusion detection or prevention techniques to watch for malware detections.
The results appear as Pattern Micro exposed that it found more than 200 victims of Mustang Panda (aka Earth Preta) assaults as component of a much-reaching cyber espionage work orchestrated by different sub-teams because 2022.
A greater part of the cyber strikes have been detected in Asia, followed by Africa, Europe, the Middle East, Oceania, North America, and South The united states.
“There are sturdy indications of intertwined conventional intelligence tradecraft and cyber collection endeavours, indicative of a hugely coordinated and complex cyber espionage operation,” Development Micro mentioned.
Identified this article fascinating? Observe us on Twitter and LinkedIn to browse far more distinctive information we submit.
Some parts of this article are sourced from:
thehackernews.com


 FDA Protects Medical Devices Against Cyber-Threats With New Measures
FDA Protects Medical Devices Against Cyber-Threats With New Measures