The sophisticated persistent danger (APT) team referred to as Evasive Panda has been observed concentrating on an global non-governmental corporation (NGO) in Mainland China with malware shipped by way of update channels of legitimate applications like Tencent QQ.
The attack chains are made to distribute a Windows installer for MgBot malware, ESET security researcher Facundo Muñoz said in a new report revealed nowadays. The activity commenced in November 2020 and ongoing in the course of 2021.
Evasive Panda, also recognized as Bronze Highland and Daggerfly, is a Chinese-talking APT group that has been attributed to a collection of cyber espionage attacks concentrating on various entities in China, Hong Kong, and other nations around the world located in East and South Asia because at the very least late December 2012.
The group’s hallmark is the use of the custom MgBot modular malware framework, which is able of receiving further components on the fly to extend on its intelligence-accumulating abilities.
Some of the prominent capabilities of the malware incorporate thieving information, logging keystrokes, harvesting clipboard facts, recording audio streams, and credential theft from web browsers.
ESET, which learned the marketing campaign in January 2022 just after a respectable Chinese application was applied to deploy an installer for the MgBot backdoor, said the qualified end users have been situated in the Gansu, Guangdong, and Jiangsu provinces and are associates of an unnamed global NGO.
The trojanized software is the Tencent QQ Windows client computer software updater (“QQUrlMgr.exe”) hosted on the area “update.browser.qq[.]com.” It can be not straight away distinct how the risk actor managed to deliver the implant via legitimate updates.
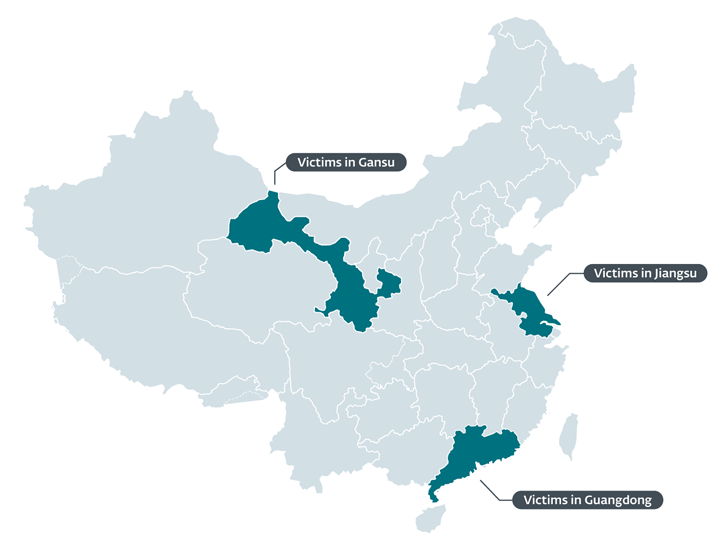
But it details to either of the two scenarios, a source chain compromise of Tencent QQ’s update servers or a scenario of an adversary-in-the-center (AitM) attack, as in-depth by Kaspersky in June 2022 involving a Chinese hacking crew dubbed LuoYu.
In recent years, lots of computer software provide chain attack has been orchestrated by nation-point out teams from Russia, China, and North Korea. The skill to gain a substantial malicious footprint quickly has not been missing on these attackers, who are significantly focusing on the IT offer chain to breach organization environments.
Forthcoming WEBINARZero Belief + Deception: Find out How to Outsmart Attackers!
Explore how Deception can detect state-of-the-art threats, prevent lateral movement, and boost your Zero Trust method. Be part of our insightful webinar!
Help save My Seat!
“AitM designs of interception would be achievable if the attackers – both LuoYu or Evasive Panda – had been ready to compromise vulnerable equipment these as routers or gateways,” Muñoz elaborated.
“With entry to ISP spine infrastructure – through authorized or illegal implies – Evasive Panda would be capable to intercept and reply to the update requests carried out by means of HTTP, or even modify packets.”
This is important as the findings come fewer than a 7 days just after Broadcom-owned Symantec thorough assaults mounted by the danger actor against telecom support suppliers in Africa employing the MgBot malware framework.
Discovered this write-up interesting? Stick to us on Twitter and LinkedIn to browse a lot more exceptional material we article.
Some parts of this article are sourced from:
thehackernews.com


 Browser Security Survey: 87% of SaaS Adopters Exposed to Browser-borne Attacks
Browser Security Survey: 87% of SaaS Adopters Exposed to Browser-borne Attacks