A Chinese-talking menace actor codenamed GoldFactory has been attributed to the growth of hugely refined banking trojans, which includes a beforehand undocumented iOS malware identified as GoldPickaxe that’s capable of harvesting identity documents, facial recognition details, and intercepting SMS.
“The GoldPickaxe family is out there for equally iOS and Android platforms,” Singapore-headquartered Team-IB reported in an substantial report shared with The Hacker Information. “GoldFactory is considered to be a effectively-organized Chinese-speaking cybercrime team with near connections to Gigabud.”
Active since at the very least mid-2023, GoldFactory is also accountable for another Android-based banking malware termed GoldDigger and its increased variant GoldDiggerPlus as nicely as GoldKefu, an embedded trojan inside GoldDiggerPlus.
Social engineering strategies distributing the malware have been identified to target the Asia-Pacific region, precisely Thailand and Vietnam, by masquerading as regional banking companies and govt businesses.
In these assaults, potential victims are sent smishing and phishing messages and guided to change the conversation to fast messaging apps like LINE, prior to sending bogus URLs that lead to the deployment of GoldPickaxe on the equipment.
Some of these malicious applications targeting Android are hosted on counterfeit web-sites resembling Google Enjoy Retailer internet pages or bogus company websites to complete the installation procedure.

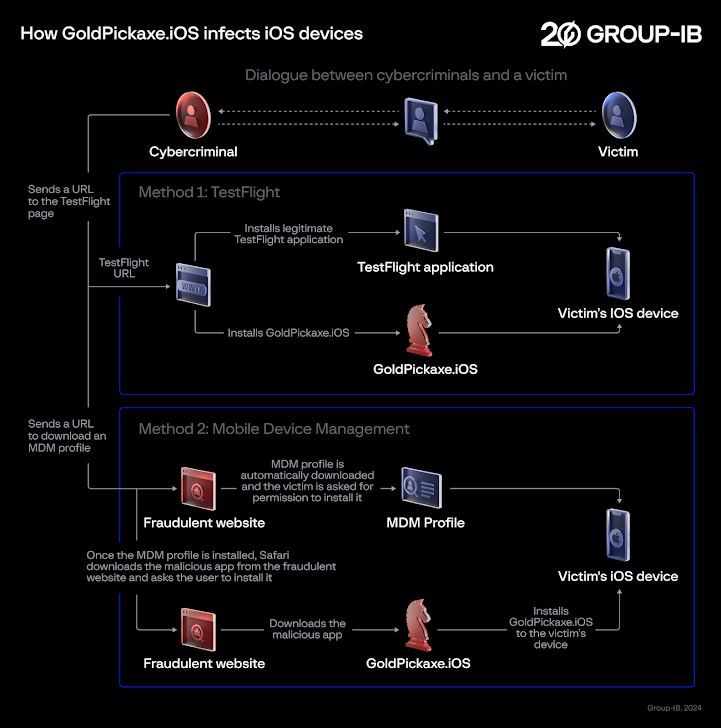
GoldPickaxe for iOS, even so, employs a different distribution plan, with successive iterations leveraging Apple’s TestFlight platform and booby-trapped URLs that prompt buyers to download an Mobile Unit Administration (MDM) profile to grant complete command over the iOS gadgets and put in the rogue app.
The two these propagation mechanisms were disclosed by the Thailand Banking Sector CERT (TB-CERT) and the Cyber Crime Investigation Bureau (CCIB), respectively, in November 2023.
The sophistication of GoldPickaxe is also evident in the simple fact that it can be designed to get all-around security actions imposed by Thailand that demand buyers to verify bigger transactions utilizing facial recognition to avoid fraud.
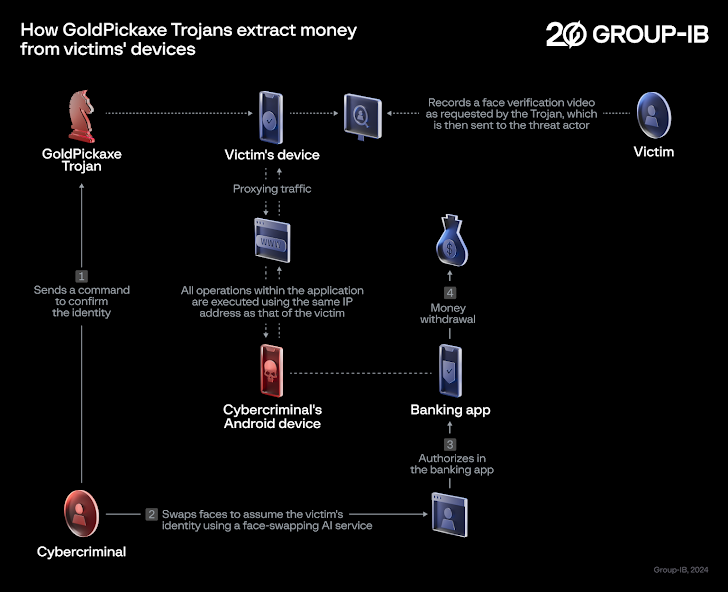
“GoldPickaxe prompts the victim to history a video as a affirmation process in the phony software,” security researchers Andrey Polovinkin and Sharmine Minimal claimed. “The recorded movie is then utilized as uncooked materials for the development of deepfake videos facilitated by face-swapping artificial intelligence products and services.”
Moreover, the Android and iOS flavors of the malware are equipped to obtain the victim’s ID paperwork and images, intercept incoming SMS messages, and proxy visitors by way of the compromised gadget. It can be suspected that the GoldFactory actors use their possess equipment to indication-in to the bank application and conduct unauthorized fund transfers.

That obtaining claimed, the iOS variant displays less functionalities when when compared to its Android counterpart owing to the closed character of the iOS running procedure and reasonably stricter nature of iOS permissions.
The Android variation – regarded as an evolutionary successor of GoldDiggerPlus – also poses as about 20 unique applications from Thailand’s government, the monetary sector, and utility companies to steal login credentials from these companies. Even so, it really is presently not distinct what the menace actors do with this information and facts.
A further notable aspect of the malware is its abuse of Android’s accessibility expert services to log keystrokes and extract on-display information.
GoldDigger also shares code-degree similarities to GoldPickaxe, although it is mainly designed to steal banking qualifications, when the latter is geared far more toward collecting of personalized facts from victims. No GoldDigger artifacts aimed at iOS products have been determined to day.
“The principal attribute of GoldDigger is that it targets over 50 programs from Vietnamese fiscal corporations, like their packages’ names in the trojan,” the scientists claimed. “When the specific apps open up, it will help save the text shown or created on the UI, which include passwords, when they are entered.”
The foundation model of GoldDigger, which was to start with learned in June 2023 and carries on to be nevertheless in circulation, has considering the fact that paved the way for far more upgraded variants, which includes GoldDiggerPlus, which comes embedded with yet another trojan APK component dubbed GoldKefu, to unleash the destructive actions.
GoldDiggerPlus is claimed to have emerged in September 2023, with GoldKefu impersonating a common Vietnamese messaging app to siphon banking qualifications associated with 10 monetary establishments.

Goldkefu also integrates with the Agora Software Progress Kit (SDK) to facilitate interactive voice and online video phone calls and trick victims into speaking to a bogus lender client support by sending bogus alerts that induce a fake sense of urgency by professing that a fund transfer to the tune of 3 million Thai Baht has taken place on their accounts.
If anything at all, the development is a signal that the cell malware landscape continues to be a lucrative industry for cybercriminals looking for brief money obtain, even as they obtain approaches to circumvent defensive steps erected by banking institutions to counter these types of threats. It also demonstrates the at any time-shifting and dynamic nature of social engineering strategies that goal to produce malware to victims’ devices.
To mitigate the dangers posed by GoldFactory and its suite of cellular banking malware, it truly is strongly recommended not to click on suspicious one-way links, install any app from untrusted web sites, as they are a widespread vector for malware, and periodically evaluate the permissions offered to applications, significantly people requesting for Android’s accessibility providers.
“GoldFactory is a resourceful group adept at several strategies, such as impersonation, accessibility keylogging, pretend banking sites, bogus bank alerts, faux simply call screens, identity, and facial recognition data collection,” the scientists said. “The team includes individual enhancement and operator teams focused to distinct regions.”
“The gang has effectively-described processes and operational maturity and frequently boosts its toolset to align with the qualified surroundings showcasing a higher proficiency in malware progress.”
Located this post interesting? Abide by us on Twitter and LinkedIn to read through extra distinctive information we put up.
Some parts of this article are sourced from:
thehackernews.com


 Critical Exchange Server Flaw (CVE-2024-21410) Under Active Exploitation
Critical Exchange Server Flaw (CVE-2024-21410) Under Active Exploitation