A Chinese country-state group has been observed targeting Foreign Affairs ministries and embassies in Europe utilizing HTML smuggling techniques to provide the PlugX distant entry trojan on compromised devices.
Cybersecurity company Examine Issue claimed the exercise, dubbed SmugX, has been ongoing since at least December 2022.
“The marketing campaign utilizes new shipping strategies to deploy (most notably – HTML Smuggling) a new variant of PlugX, an implant generally connected with a wide wide range of Chinese risk actors,” Check Level explained.
“Whilst the payload alone continues to be equivalent to the 1 located in older PlugX variants, its supply approaches end result in very low detection costs, which until finally a short while ago aided the campaign fly underneath the radar.”
The actual identity of the risk actor at the rear of the procedure is a small hazy, despite the fact that present clues position in the course of Mustang Panda, which also shares overlaps with clusters tracked as Earth Preta, RedDelta, and Verify Point’s have designation Camaro Dragon.
Even so, the corporation said there is “inadequate evidence” at this phase to conclusively attribute it to the adversarial collective.
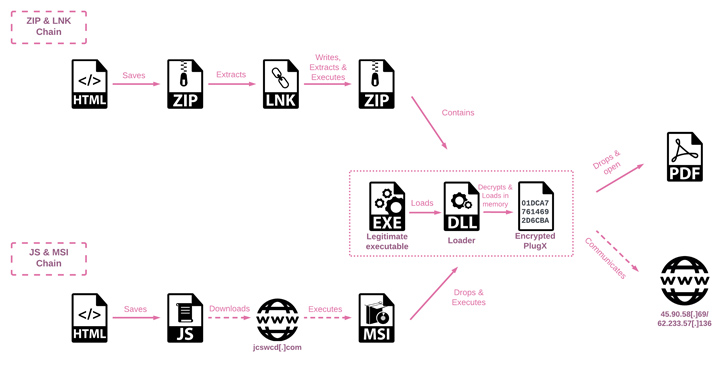
The most recent attack sequence is substantial for the use of HTML Smuggling – a stealthy procedure in which legit HTML5 and JavaScript capabilities are abused to assemble and start the malware – in the decoy documents hooked up to spear-phishing e-mails.
“HTML smuggling employs HTML5 attributes that can function offline by storing a binary in an immutable blob of data in JavaScript code,” Trustwave pointed out before this February. “The data blob, or the embedded payload, receives decoded into a file object when opened by means of a web browser.”
An analysis of the documents, which were uploaded to the VirusTotal malware database, reveals that they are intended to focus on diplomats and authorities entities in Czechia, Hungary, Slovakia, the U.K., Ukraine, and also very likely France and Sweden.

In a person instance, the threat actor is reported to have utilized an Uyghur-themed lure (“China Tries to Block Prominent Uyghur Speaker at UN.docx”) that, when opened, beacons to an exterior server by implies of an embedded, invisible monitoring pixel to exfiltrate reconnaissance details.
The multi-phase infection process makes use of DLL side-loading approaches to decrypt and launch the final payload, PlugX.
Also termed Korplug, the malware dates all the way back to 2008 and is a modular trojan capable of accommodating “various plugins with unique functionalities” that enables the operators to carry out file theft, display captures, keystroke logging, and command execution.
“During the system of our investigating the samples, the danger actor dispatched a batch script, sent from the C&C server, intended to erase any trace of their routines,” Check Point reported.
“This script, named del_RoboTask Update.bat, eradicates the authentic executable, the PlugX loader DLL, and the registry crucial executed for persistence, and in the long run deletes by itself. It is likely this is the final result of the threat actors becoming informed they have been beneath scrutiny.”
Observed this post attention-grabbing? Follow us on Twitter and LinkedIn to go through extra special material we post.
Some parts of this article are sourced from:
thehackernews.com


 Improve Your Security WordPress Spam Protection With CleanTalk Anti-Spam
Improve Your Security WordPress Spam Protection With CleanTalk Anti-Spam